In a world increasingly dominated by digital interactions, the significance of cryptographic methods cannot be overstated. Two principal types of encryption, symmetric and asymmetric, serve as the bedrock for securing data transmissions, yet they operate on fundamentally different principles. This article delineates the distinctions and applications of these encryption techniques, inviting readers to reevaluate their perspectives on data security.
Fundamental Concepts
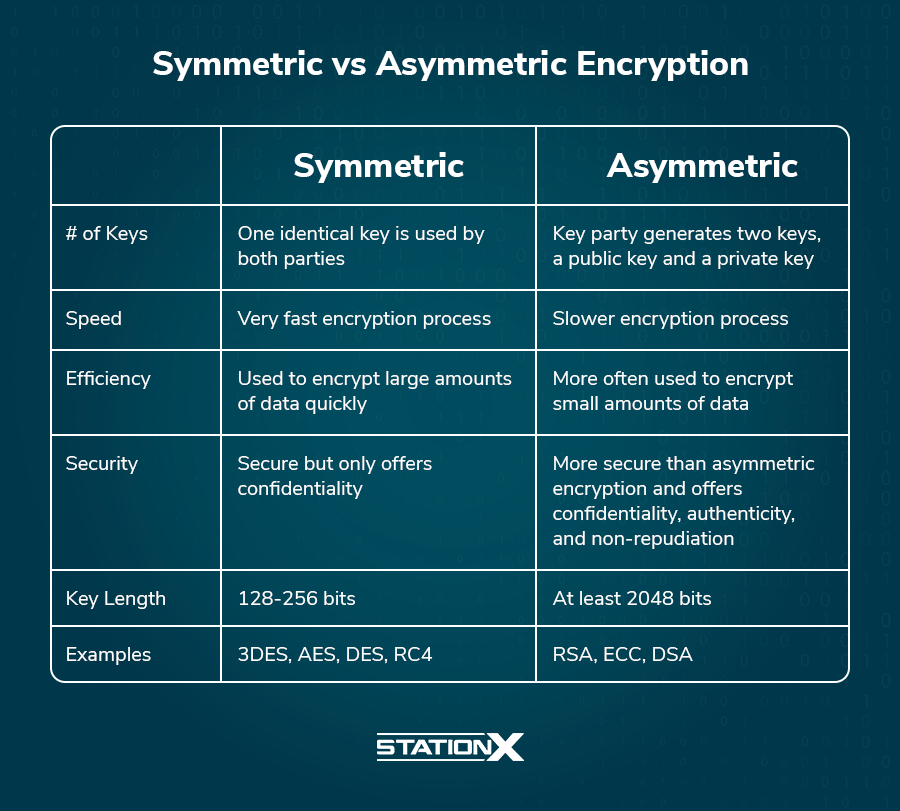
At its core, encryption is the process of converting information into an unreadable format to deter unauthorized access. This transformation is critical in safeguarding sensitive information, whether it is personal data, financial records, or proprietary business information. Symmetric encryption employs a single key for both encryption and decryption, while asymmetric encryption utilizes a pair of keys: a public key for encryption and a private key for decryption. Understanding these concepts is paramount for grasping their practical implications.
Symmetric Encryption Explained
Symmetric encryption, also known as secret key encryption, relies on a single key that must be kept confidential between the communicating parties. The algorithm utilizes this key to encrypt the data, and the same key is required for decryption. One of the principal advantages of symmetric encryption is its efficiency; the process is typically faster than asymmetric methods and requires fewer computational resources. Consequently, symmetric encryption is commonly employed in scenarios where large volumes of data must be transmitted quickly, such as in database encryption or securing communication over VPNs.
However, this method presents significant challenges, particularly concerning key distribution. The key must be securely exchanged and saved, which can be cumbersome and prone to security risks. If a malicious actor gains access to the key, they can decrypt and misuse the information. This vulnerability highlights a critical issue in the realm of symmetric encryption.
Asymmetric Encryption Unveiled
In stark contrast, asymmetric encryption introduces a dual-key mechanism whereby one key is made publicly available, and the other remains secret. The public key is disseminated widely, allowing anyone to encrypt a message that can only be decrypted by the corresponding private key held by the recipient. This paradigm eliminates the necessity for key exchange between parties, exponentially enhancing security.
Asymmetric encryption is particularly advantageous in online transactions, where trust is paramount. Examples include securing connections over HTTPS or digitally signing documents to verify authenticity. However, the computational intensity of asymmetric encryption results in slower processing speeds compared to its symmetric counterpart. This disparity can render asymmetric encryption impractical for encrypting large files or conducting high-frequency transactions.
Comparative Analysis
When juxtaposing symmetric and asymmetric encryption, several factors emerge that warrant careful consideration:
- Speed and Efficiency: Symmetric encryption, owing to its simplicity and lower computational load, excels in speed. It is optimal for encrypting vast datasets or live communications. Conversely, asymmetric encryption’s complexity can introduce latency, making it less suitable for extensive data.
- Key Management: Symmetric encryption’s reliance on a single key raises substantial key management challenges. Securely exchanging the key presents a significant risk if not properly managed. Asymmetric encryption mitigates this issue through its public key infrastructure, allowing users to exchange information without ever disclosing their private keys.
- Security Levels: While symmetric encryption can be highly secure with a sufficiently complex key, the compromise of the key results in a complete breach of security. Asymmetric encryption, due to its dual-key nature, adds layers of security, ensuring that even if the public key is compromised, the private key remains safe barring physical access to the device.
- Use Cases: Symmetric encryption shines in contexts such as encrypting database information or securing sensitive files in storage. Asymmetric encryption is the cornerstone of secure internet communications, digital signatures, and key exchange protocols like SSL/TLS.
Integration of Techniques
While symmetric and asymmetric encryption stand as distinct approaches, they are not mutually exclusive. In practice, many systems utilize a combination of both encryption methods to capitalize on their respective strengths. For instance, asymmetric encryption can facilitate the secure exchange of a symmetric key, which can subsequently be employed for fast data encryption during a session. This hybrid model embodies a strategic equilibrium of speed, security, and practicality.
Evolving Landscape and Future Directions
The future of encryption is poised for further evolution as advancements in technology present both challenges and opportunities. The emergence of quantum computing threatens the integrity of traditional asymmetric encryption methods, necessitating the development of quantum-resistant algorithms. Moreover, as data privacy regulations become more stringent globally, the impetus for robust encryption strategies escalates. Organizations must continuously evaluate and refine their encryption mechanisms to meet these evolving demands.
Conclusion
Asymmetric and symmetric encryption, with their unique characteristics and applications, serve as foundational elements in the quest for secure data transmission. A nuanced understanding of both methods empowers individuals and organizations to make informed decisions regarding data protection strategies. Through continued exploration and adaptation, the cryptographic community can navigate the complexities of modern security challenges, ensuring the safeguarding of sensitive information for years to come.







Leave a Comment