In the realm of cryptography, where data protection is paramount, two encryption algorithms have steadfastly held sway over generations: the Advanced Encryption Standard (AES) and the Data Encryption Standard (DES). As we venture into 2025, one may ponder: which encryption algorithm reigns supreme? This inquiry not only encapsulates the technicalities of these cryptographic methodologies but also reflects upon their relevance and efficacy in today’s vastly interconnected digital landscape. Let us delve into their characteristics, historical contexts, and performance metrics to discern a definitive answer.
The Origins of AES and DES
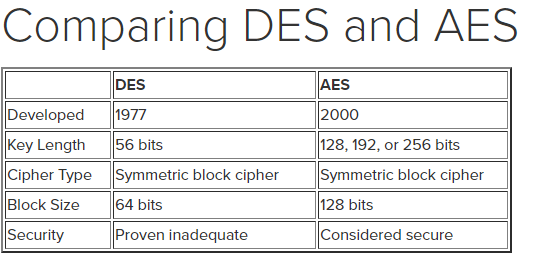
DES, formulated in the 1970s, was a groundbreaking achievement for the National Institute of Standards and Technology (NIST). Its adoption was seen as a revolutionary step in securing electronic data. DES operates through a symmetric key algorithm where a singular key is employed both for encryption and decryption. However, as technology advanced, vulnerabilities in DES’s 56-bit key length became increasingly apparent. The confluence of computational power and cryptographic analysis exposed its frailties, resulting in its obsolescence by the late 1990s.
In response to DES’s shortcomings, NIST initiated a call for a new encryption standard. This led to the advent of AES in 2001, a cipher that utilizes block sizes of 128 bits and key lengths of 128, 192, or 256 bits. The robustness and versatility of AES have made it the de facto standard for securing sensitive data across various sectors, including government, military, and finance. AES employs a series of well-defined and complex transformations, ensuring higher resilience against attacks.
Performance Metrics: AES vs DES
When assessing the performance of encryption algorithms, factors such as speed, efficiency, and security come into play. While DES, by virtue of its simpler structure, may exhibit faster encryption speeds in certain legacy applications, it falls short against the backdrop of modern computational capabilities. In stark contrast, the multifaceted architecture of AES, despite its more complex operations, provides superior speed and efficiency on contemporary systems.
Benchmarking tests have repeatedly demonstrated that AES performs better than DES in cryptographic processing. With key lengths of up to 256 bits, AES can withstand brute force attacks exponentially longer than DES’s antiquated 56-bit key. As we pivot into 2025, this distinction becomes increasingly pertinent given the relentless advance of quantum computing and enhanced cyber threats.
Security Landscape: Evolving Threats
In the current digital age, the security landscape is in a perpetual state of evolution. Cyber attackers are employing more sophisticated techniques and tools, prompting a reevaluation of existing encryption methods. AES’s layered approach to security has rendered it more adept at counteracting a plethora of potential threats, including brute force, differential, and linear cryptanalysis. DES, however, is now viewed as a relic, compromised not only by its limited key space but also by vulnerabilities that have been thoroughly documented and exploited.
In 2025, the necessity for encryption algorithms that can withstand emerging technologies, such as quantum computing, becomes increasingly apparent. Quantum computers have the potential to unravel conventional cryptographic practices using algorithms like Shor’s, which can efficiently factor large integers and solve discrete logarithm problems. Although both AES and DES would face challenges in the face of quantum capabilities, the critical distinction lies in AES’s inherent adaptability through scalable key lengths, thus provisioning a firmer grip on security.
Usability and Deployment Considerations
Beyond raw performance and security metrics, usability also plays a vital role in determining the efficacy of encryption algorithms. DES may still linger in some legacy systems due to its historical significance and established frameworks. Nonetheless, organizations using DES are advised to transition to AES. The transition not only ensures greater security but also aligns with industry standards and regulatory compliance mandates, such as those dictated by GDPR and HIPAA.
AES’s widespread adoption across various sectors is indicative of its utility. It is not simply the realm of seasoned cryptographers; developers across diverse technological landscapes are well-versed in implementing AES. Its extensive libraries and frameworks contribute to an ecosystem that fosters ease of deployment and consistent updates.
The Playful Question: Will the Unforeseen Challenge Emerge?
As we draw closer to 2025, one may pose a playful yet thought-provoking challenge: could another encryption algorithm evolve that could supersede AES? The cyber landscape is replete with innovators harnessing the power of machine learning and artificial intelligence to create next-generation cryptographic techniques. Could this lead to the birth of an encryption methodology that balances computational efficiency with an unprecedented level of security?
While skepticism remains, it is essential to embrace the dynamism of the technological sphere. Trends such as homomorphic encryption and lattice-based cryptography are blossoming, displaying promising attributes that may challenge the longevity of AES. Perhaps in 2025, we will witness a compelling juxtaposition of traditional algorithms against nascent alternatives born from the crucible of innovation.
Conclusion
In conclusion, as we navigate through 2025, it is unequivocal that AES stands triumphantly over DES in terms of security, performance, and adaptability. Nevertheless, the future may hold surprises that could redefine the landscape of cryptography. The key to securing data in this age lies not only in the robustness of algorithms but also in an unwavering commitment to evolve alongside the threats that seek to compromise them. Will AES continue to reign supreme, or will we embrace a revolutionary challenge to the very foundations of encryption? Only time will tell.







Leave a Comment