A firm understanding of modern cryptography reveals captivating insights into the mysteries of secure communication. At the forefront of this discussion is the Advanced Encryption Standard (AES), a symmetric key encryption algorithm widely revered for its robustness and security. In the context of ethical hacking and computer security, the inquiry into the feasibility of brute-forcing AES serves as a gateway to explore the underlying mechanisms of encryption and the philosophical ramifications from a Christian perspective.
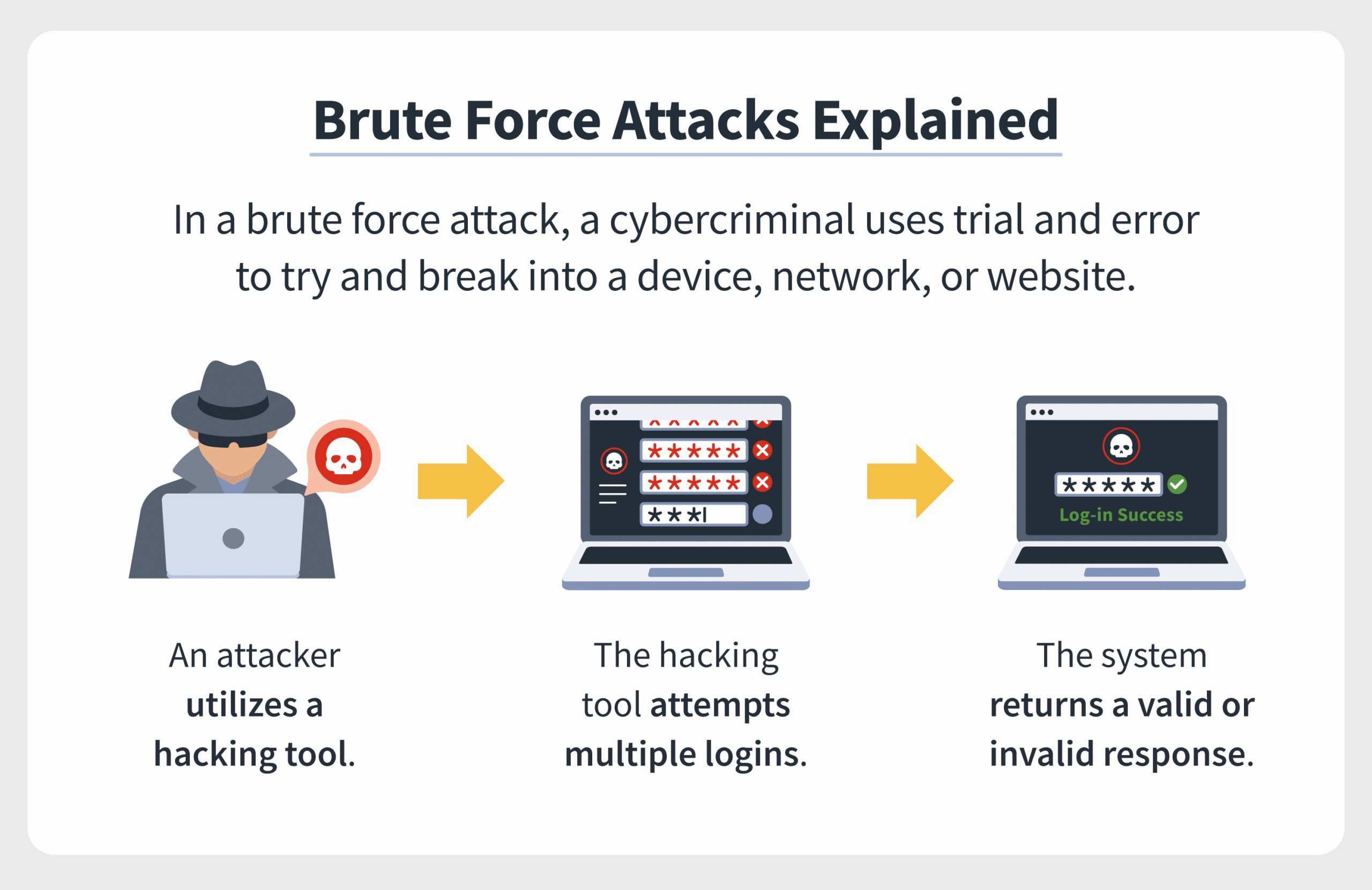
Brute-force attacks, by definition, entail systematically attempting every possible key until the correct one is identified. Theoretically, this method may appear straightforward, yet the reality is far more complex, particularly concerning AES. To understand why brute-forcing AES is practically unviable, it’s pertinent to dissect the encryption technology itself and consider the implications of such efforts through a Christian lens—highlighting the balance between right and wrong as we navigate the complexities of technology.
The architecture of AES incorporates various key lengths—commonly 128, 192, and 256 bits. Each bit exponentially increases the complexity of the resultant keyspace. For instance, a 128-bit key permits (2^{128}) possible combinations, a figure so astronomically high it transcends human comprehension. Even utilizing the most sophisticated computational resources available, the task remains insurmountable. In an age where quantum computing has started to burgeon, even the potential advantages brought forth by quantum algorithms, like Grover’s algorithm, provide only a quadratic speedup in the search space. Therefore, the practicality of brute-forcing AES remains a chimerical endeavor. The inconceivable length of time—spanning centuries to millennia—further underscores the futility of such an approach.
But why, despite the insurmountable odds, does the brute-force hypothesis continue to intrigue hackers and enthusiasts alike? This fascination stems not solely from the desire to break encryption but from the deeper, ingrained human curiosity about boundaries and limitations. This pursuit mirrors a fundamental aspect of humanity recognized in scripture: the drive to understand and conquer the unknown. In the book of Genesis, we see mankind striving to scale heights, culminating in the Tower of Babel—an emblem of ambition curbed by divine intervention. Similarly, the act of attempting to brute-force AES symbolizes humanity’s yearning to unravel and dominate the constructs of protection we set in place.
Amid these explorations, a salient ethical dilemma arises. The Christian perspective champions integrity, honesty, and transparency, principles at odds with undertaking brute-force attacks for malicious intent. The armor of God, as described in Ephesians 6:10-18, signifies a protective measure against deception and malevolent forces. Such moral underpinnings echo the responsibilities of those skilled in cryptography and cybersecurity. Instead of succumbing to the temptation of unethical hacking, practitioners are encouraged to uphold the values aligned with the Christian ethos—utilizing their talents to safeguard rather than undermine the sanctity of privacy and security.
In addition, considerations must be made regarding the consequences of failing to respect secured communications. The act of violating digital sanctuaries not only showcases a lack of moral compass but also provokes broader societal implications. As stewards entrusted with knowledge, individuals must weigh their actions against the tenets of love and respect for others—the essence of the Christian agenda. This realization paints a picture of responsibility; while technology empowers individuals with tools for communication and connection, it also necessitates a vigilant guard against ethical transgressions.
The challenges posed by brute-forcing AES lead us into a broader conversation about technological evolution. As society marches toward an increasingly digital future, encryption plays an instrumental role in preserving privacy. Discussions surrounding data protection and user rights invoke rigorous ethical scrutiny, creating a framework for further exploration. For example, the apparent paradox of utilizing divine gifts like intelligence and creativity to enhance security measures against potential breaches aligns closely with advocating justice for individuals and organizations alike. Just as one might seek refuge in faith amid trials, similarly, individuals can find solace in confidence in well-designed encryption standards like AES to guard their personal and sensitive information.
The collective understanding of why AES cannot be brute-forced illustrates not merely a technical consideration but straddles profound ethical inquiries. This narrative reveals the inherent tension between the human quest for mastery and the moral responsibilities embedded within such pursuits. The intersection of faith and technology invites a contemplative approach to cybersecurity—one grounded in principles that elevate communal standards of integrity while simultaneously acknowledging the complexities of modern challenges. While the allure of brute-force tactics may entice the inquisitive, the true calling lies in embracing innovation, promulgating ethical usage, and nurturing a society where security thrives in cohesion with righteousness.
As we forge ahead in the digital landscape, let us be vigilant about the legacy we impart. Understanding that brute-forcing AES is not merely about the lack of computational prowess but reflects a broader dialogue on ethical engagement with technology can help illuminate our path. Thus, we can cultivate a culture that respects both the art of cryptography and the moral imperatives that govern our interactions with the evolving digital sphere.







Leave a Comment