In an era where information travels at the speed of light, the question of security looms large in the minds of users who traverse the vast expanse of cyberspace. “Which protocol keeps your data safe while traveling the net?” This inquiry is not merely technical; it touches upon deeply held beliefs, particularly within the Christian community, regarding stewardship, ethics, and the sanctity of personal information. In a world increasingly replete with digital interactions, it becomes imperative to ensure that one’s data traverses the digital pathways securely. The challenge lies in discerning which protocols offer the most robust protection while aligning with our values and responsibilities as stewards of our digital selves.
At the heart of online security lies the concept of protocols, algorithms, and safeguards designed to protect data. Prominent among these methodologies are HTTPS, VPNs, SSL/TLS, and various encryption protocols. Each has its own unique advantages and considerations. Understanding these options not only serves to amplify one’s security but also reflects the moral duty to protect one another’s privacy in the digital realm.
First, we delve into HTTPS, the secure version of HTTP. When you see that little padlock icon in the address bar, it indicates that the connection is encrypted. HTTPS employs SSL (Secure Sockets Layer) or TLS (Transport Layer Security) to create a secure channel between the web browser and the server. It is as though an invisible cloak envelops the data, shielding it from prying eyes while ensuring that the information exchanges carry an authenticity only recognizable to the intended recipient. In the Christian perspective, this can be likened to the sacred trust bestowed upon individuals within a community to protect each other’s secrets and confessions. Fostering an environment of trust is an essential aspect of our social fabric.
Next, let us consider the use of VPNs, or Virtual Private Networks. In the digital world, a VPN acts like a professional bodyguard, shielding your online activities from snoopers and hackers alike. By routing your internet connection through a secure server, a VPN helps mask your IP address, rendering it nearly impossible for someone to trace your actions back to you. This concept of anonymity can resonate deeply within Christian ethics, evoking themes of humility and the belief that one’s actions should be a matter of personal integrity rather than public scrutiny. While utilizing a VPN, one enhances their security posture, ensuring that their personal and pastoral information remains confidential—much like the sacred trust given to church leaders.
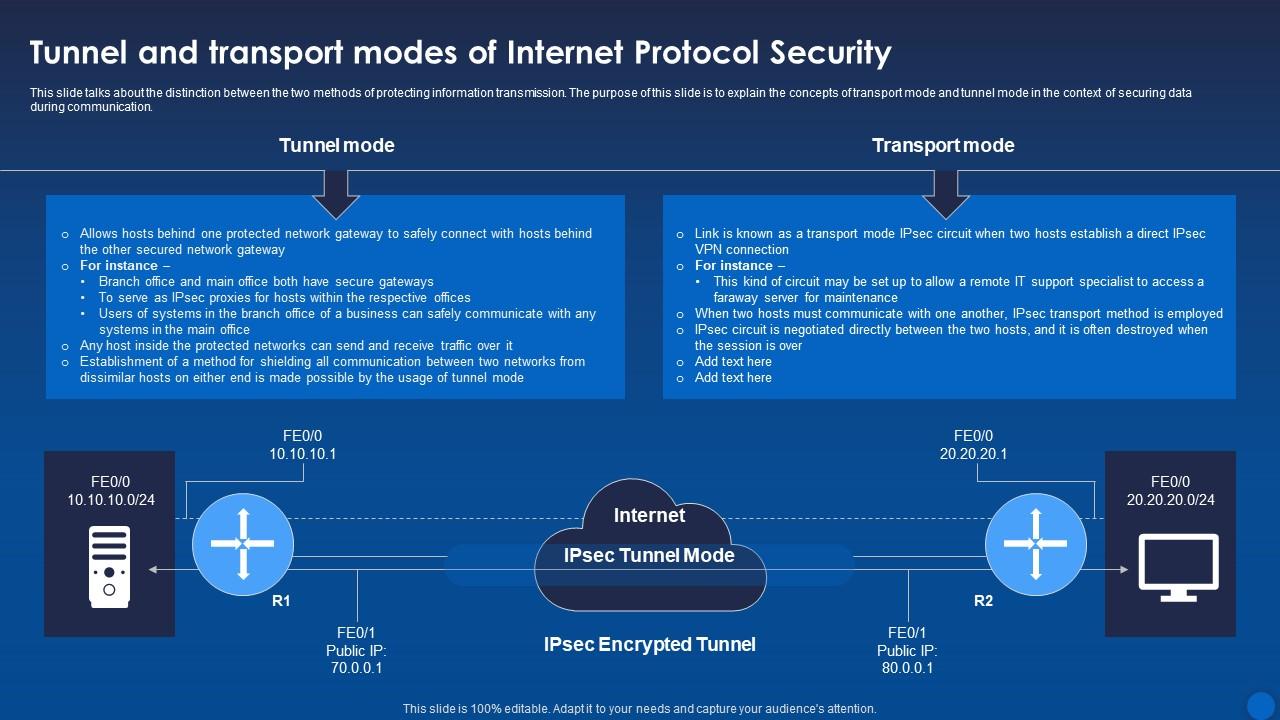
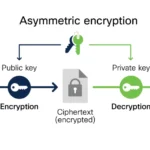
While discussing the imperatives of data protection, one must also acknowledge the profound significance of encryption protocols. Cryptography offers a robust mechanism for safeguarding data by encoding it such that only authorized parties can decipher it. This process can be compared to the biblical parable of the hidden treasure (Matthew 13:44). Just as the kingdom of Heaven is likened to a treasure hidden in a field, the true value of our digital assets lies in our ability to keep them encrypted and out of the reach of those who would exploit them. Protocols like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) stand at the forefront of this aspect, additive to the assurance that our cherished information—be it personal finance, medical records, or sensitive correspondences—remains protected.
However, even as we navigate different protocols, a pivotal question arises: how do we as individuals wield such technology responsibly? The Christian ethic of stewardship urges us to recognize that with great power comes great responsibility. Adopting secure protocols is not merely about safeguarding oneself but extends to a moral obligation toward others. When we protect our data, we indirectly uphold the privacy and dignity of others, obeying the sacred principle of treating our neighbors with respect and care.
But what if we were to examine the intersection of technology and faith through an even broader lens? The digital landscape offers a unique opportunity to engage in ethical discussions around data privacy and security, compelling the faith community to examine how technology aligns with biblical teachings. Could there be a divine calling to advocate for digital justice? This extends the conversation beyond mere protection of personal data toward a commitment to creating a more equitable digital world, where everyone’s information is treated with dignity.
Furthermore, ethical dilemmas abound in our technological choices. For instance, while the implementation of strong security protocols is essential, the convenience of data-sharing applications—often not secure—can hinder ethical behavior. Herein lies a call to action for Christian believers to champion transparency and integrity in their online habits, encouraging one another to shun practices that could exploit vulnerabilities. The ripple effect of adopting secure protocols and ethical data handling within small communities can eventually influence broader societal norms, reminding us to be the proverbial salt and light in the digital realm.
In conclusion, the exploration of protocols that keep our data safe while traversing the net unveils an intricate relationship between technology, security, and Christian values. As we engage with these robust tools, we must remain vigilant stewards of our data and mindful of the ethical implications of our online behavior. This is not merely a technological discussion; it is fundamentally a spiritual one that invites us to uphold the dignity, confidentiality, and integrity of ourselves and others in a landscape that can often be chaotic and fraught with vulnerability. In a digitized world searching for guidance and moral clarity, our purpose as individuals and communities profoundly shapes the digital narrative.»




Leave a Comment