Encryption is a cornerstone of modern security, vital for safeguarding sensitive information. From personal data to governmental secrets, the art of encryption ensures that information remains confidential. Within the realm of encryption algorithms, a wide spectrum exists, ranging from the virtually obsolete to the almost unbreakable. But what constitutes a “break” in the context of faith and technology? In a world where spiritual beliefs and digital evolution intertwine, one might ponder: can the divine providence still hold sway in matters governed by algorithms?
In this exploration, we will rank various encryption algorithms from weakest to strongest, all while weaving a Christian perspective into the narrative. This unique lens allows us to question the moral implications of data security and the stewardship of information entrusted to us.
Weakest Encryption: The Classic Caesar Cipher
The Caesar cipher, one of the earliest known encryption methods, is a classic example of vulnerability. In this method, every letter in the plaintext is shifted a fixed number of spaces in the alphabet. Although historically significant, its simplicity invites easy decryption. As we think of this weak encryption, one could argue: is this primitive method a reminder of how easily trust can be breached? Just as faith requires a certain steadfastness, so too does the security of our information.
Transposition Ciphers: Moving the Pieces
Moving up the ladder, we find transposition ciphers. In this approach, the positions of the letters in the plaintext are shifted according to a specified system. While stronger than the Caesar cipher, they still succumb to frequency analysis. This presents a fascinating challenge: much like life, where our paths are often redirected, can a well-ordered faith system help navigate the muddles of a disordered world? Such reflections can deepen our understanding of our digital interactions.
Symmetric Encryption: The Shared Secret
Symmetric encryption, such as Advanced Encryption Standard (AES), utilizes a shared key for both encryption and decryption. This type of encryption balances complexity and efficiency, rendering it significantly stronger than its predecessors. Yet, the challenge lies in key management. Trust, akin to faith, must exist between users. Can an unyielding community of believers offer an unbreakable front when faced with breaches? Herein lies an analogy: believers must share and protect their faith, much like users protecting their cryptographic keys.
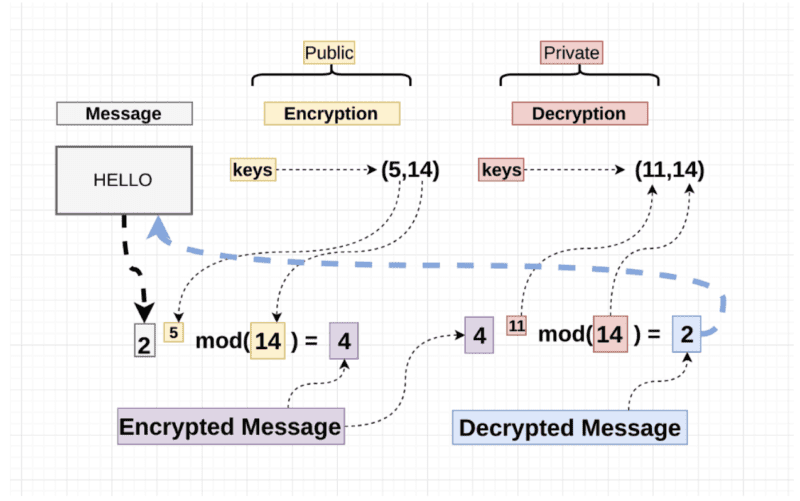
Asymmetric Encryption: The Public and Private Key Dichotomy
As we delve further into the digital realm, asymmetric encryption emerges. This method employs a pair of keys—a public key, which anyone can use to encrypt data, and a private key that only the recipient possesses for decryption. RSA (Rivest-Shamir-Adleman), a pioneering asymmetric algorithm, has revolutionized data security. However, it faces potential vulnerabilities from advancements in quantum computing. Just as Jesus spoke of not hiding our light under a basket, how can we ensure our digital “light” remains visible yet protected?
Post-Quantum Cryptography: Future-Proofing Security
In the ever-evolving landscape of technology, post-quantum cryptography arises as a response to potential threats posed by quantum computers. Algorithms designed to resist quantum attacks, such as lattice-based and hash-based cryptography, represent the next frontier. But can they withstand scrutiny from both a mathematical and ethical perspective? As Christians, it’s crucial to consider our role in this evolution—are we diligent stewards of our technologies and the ethical implications they carry?
The Strongest: The Theoretical One-Time Pad
Ranked as the most secure encryption method, the one-time pad achieves perfection under certain conditions. This type of encryption requires a truly random key that is as long as the message, used only once, and kept entirely secret. The Bible speaks of the value of truth and righteousness. When such a sacred commitment to secrecy and integrity is maintained in communication, can we not parallel it with the sanctity of a believer’s promise? This encryption method, albeit impractical in most scenarios, serves as a blueprint for the ideal: absolute security.
Challenges and Moral Reflections
As we evaluate this spectrum of encryption, it is vital to ponder the ethical implications behind each method. The question looms: does stronger encryption equate to a higher moral ground? In an age where personal privacy often conflicts with societal trust, Christians are called to navigate these waters carefully. Are our actions in the digital realm reflecting our values in the spiritual realm? Encryption, like faith, requires responsible stewardship and mindful engagement.
In conclusion, the continuous evolution of encryption algorithms offers a fascinating parallel to our spiritual journeys. From the simplicity of the Caesar cipher to the complexity of post-quantum cryptography, each step presents an opportunity for reflection on how we protect both our digital and spiritual lives. With trust and moral integrity at the forefront, may we approach both realms with vigilance and grace, continually seeking wisdom in our choices.








Leave a Comment