In the digital age, understanding cybersecurity is paramount. One significant threat is the brute force attack, an insidious method employed by cybercriminals to infiltrate secure systems. This article delves into what constitutes a brute force attack, its implications, and real-life examples that echo biblical principles, offering a perspective that aligns with Christian teachings.
Defining Brute Force Attacks
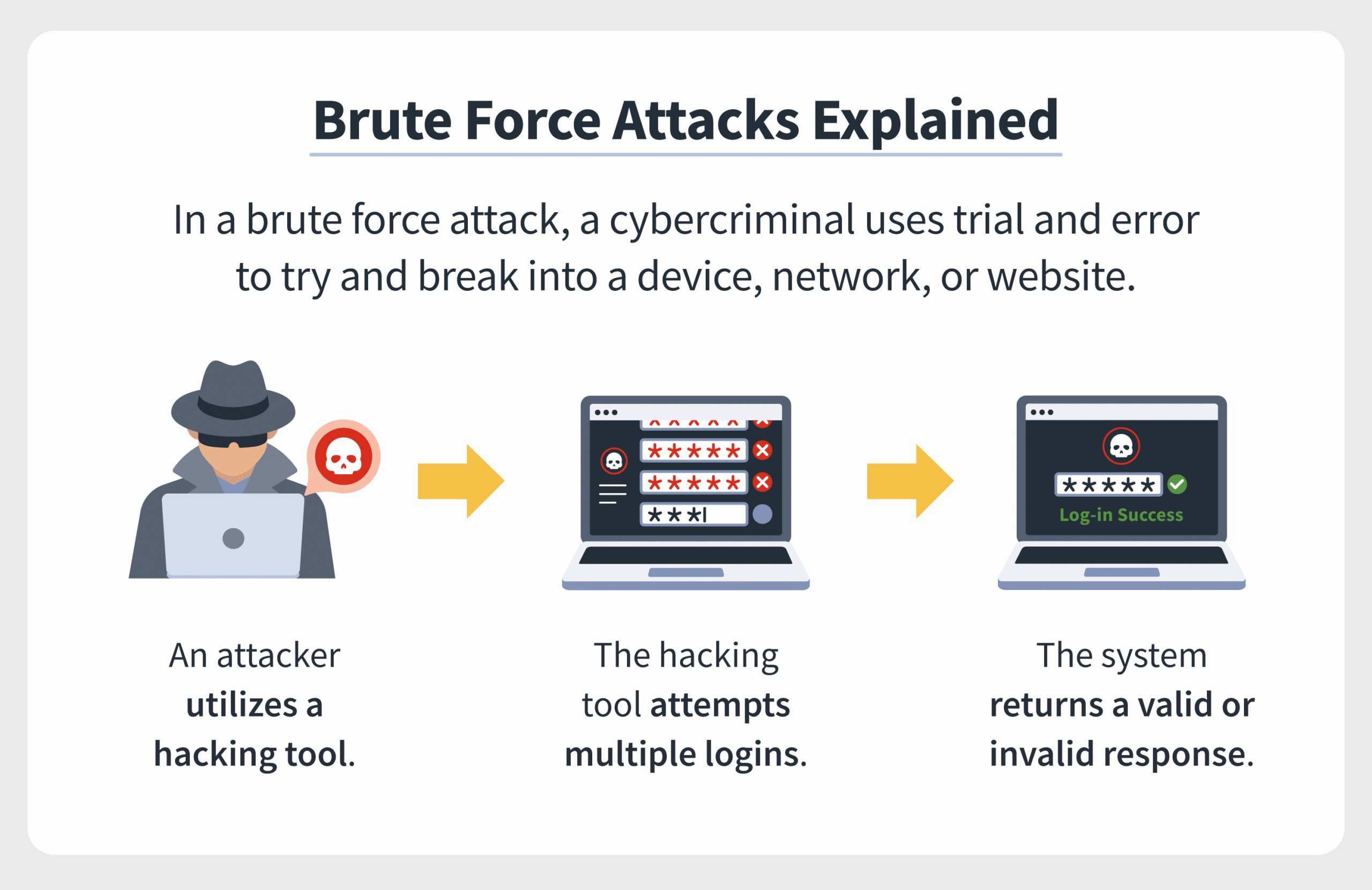
A brute force attack is a method of cryptanalysis that involves systematically testing all possible combinations of passwords or encryption keys until the correct one is discovered. This technique relies on the computational power of modern machines, enabling them to attempt thousands—or even millions—of combinations in mere moments. While simple in concept, the execution of these attacks demands not only patience but also a cavalier disregard for ethical considerations.
The Mechanism Behind Brute Force Attacks
Brute force attacks function on the principle of iteration. Cybercriminals utilize automated software tools to churn through passwords at an astonishing rate. There are multiple variants of brute force attacks, including:
- Simple Brute Force Attacks: In these scenarios, every possible combination is tested sequentially.
- Dictionary Attacks: These attacks use a pre-defined list of common passwords and phrases to expedite the process.
- Hybrid Attacks: Combining dictionary attacks with brute force, these methods introduce variations to common passwords.
Within the Christian narrative, we can draw parallels that illuminate the moral quandaries associated with these cyber intrusions. Just as David confronted Goliath, those who cultivate strong, secure systems must operate with both fortitude and wisdom against relentless attacks.
Real-Life Examples of Brute Force Attacks
In 2012, the attacks on LinkedIn provide a poignant example. Cybercriminals harnessed brute force techniques to crack user passwords, exposing sensitive information. The aftermath was catastrophic—not solely for the individuals impacted but for the overall trust in digital platforms. This incident serves as a modern parable, reflecting the Biblical story of Samson, whose vulnerability to betrayal ultimately resulted in his downfall in the hands of those who sought to exploit his weaknesses.
Another telling incident occurred with the retailer Target in 2013. Although they fell victim to a different form of attack, a component of the infiltration involved brute force methods aimed at accessing sensitive data. The breach led to a significant loss of consumer trust and financial repercussions. This situation resonates with the Christian notion of stewardship, highlighting the responsibility that organizations bear to safeguard the information entrusted to them—reminding us of Proverbs 12:27, where it suggests a diligent person will reap the benefits of their efforts.
The Ethical Dimensions of Brute Force Attacks
From a Christian perspective, brute force attacks represent not just a technical challenge but a profound moral crisis. These actions embody a fundamental breach of trust—a violation of the ethical commandment to love one’s neighbor. When systems are breached through brute force, the fallout extends beyond financial losses, permeating relationships, integrity, and community trust.
Much like the parable of the Good Samaritan, which teaches the importance of caring for those in need, we are called to defend and assist those who fall prey to malicious intents. This call to action urges us to fortify our digital realms, ensuring they are as secure as possible against brute force assaults.
Defensive Strategies Against Brute Force Attacks
Preventing brute force attacks requires a multifaceted approach, akin to the biblical precept of being vigilant and prepared. Here are several strategies that can be employed:
- Strong Password Policies: Encourage the use of complex, unique passwords that combine upper and lower case letters, numbers, and symbols.
- Account Lockout Mechanisms: Implement policies that lock accounts after a certain number of failed login attempts, deterring attackers.
- Multi-Factor Authentication: By requiring two or more verification methods, organizations can add an extra layer of security that significantly thwarts brute force efforts.
In a world where information is kingdom, these protective measures echo the wisdom of Proverbs 4:23: “Above all else, guard your heart, for everything you do flows from it.” Cybersecurity, then, is the heart of digital life—an imperative to safeguard the integrity of our interactions and data.
Conclusion: Lessons from Brute Force Attacks
In conclusion, exploring the concept of brute force attacks through a Christian lens provides a profound understanding of the ethical challenges posed by such cyber intrusions. Just as we are called to be good stewards of our relationships, we must also apply this ethic to our digital engagements. As cyber threats become more sophisticated, this biblical perspective impels us to fortify our defenses and remain vigilant, aligning technology with integrity and compassion.
The story of cybersecurity is far more than counts and codes; it encapsulates the essence of humanity, choice, and ethical conduct. May we navigate this digital landscape with the wisdom and discernment that our faith inspires, fostering an environment of safety and trust amidst the chaos of modern challenges.





Leave a Comment