In the digital age, where information flows freely yet holds immense value, the security of data transmission is paramount. One key component that plays a significant role in safeguarding this data is the TLS cipher. Cipher suites, the selection of algorithms that encrypt and decrypt information, are the backbone of Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, which are vital in creating secure communications over the Internet. To appreciate the significance of TLS ciphers within a Christian perspective, one must delve into the technical intricacies while also understanding the ethical undercurrents that govern their use.
The Essence of TLS Ciphers
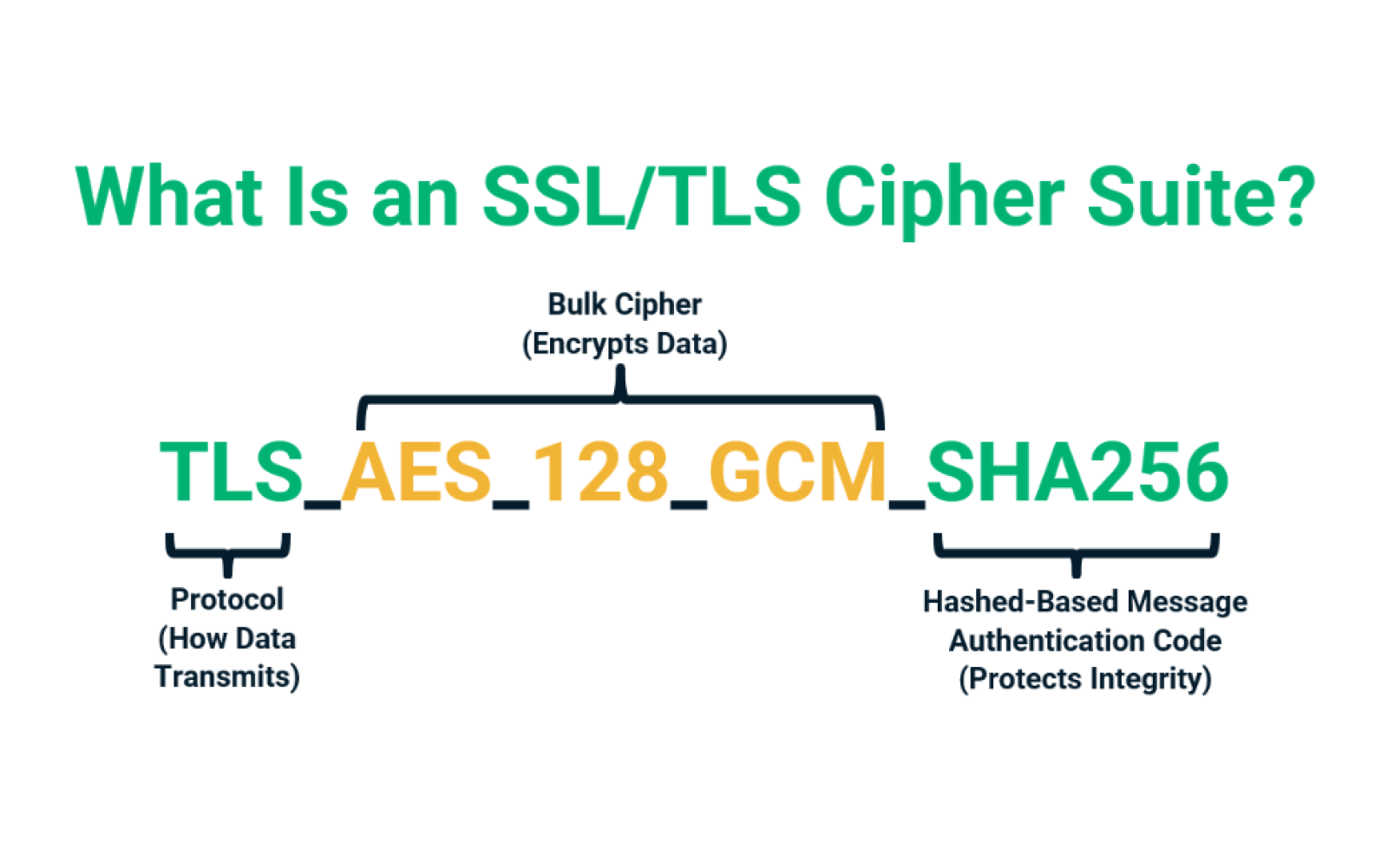
The term “cipher” refers to a method of transforming readable data into an encrypted format to protect it from unauthorized access. TLS ciphers facilitate this transformation by employing various algorithms in combination. Each cipher suite consists of key exchange algorithms, authentication methods, symmetric ciphers for data encryption, and hash functions for data integrity. The choice of these algorithms significantly impacts the robustness of the security they provide.
Key Components of a Cipher Suite
The architecture of a cipher suite provides a rich tapestry of cryptographic methods. This section elucidates the primary components:
- Key Exchange Algorithms: These algorithms allow the secure establishment of a session key between two parties. Common methods include Diffie-Hellman and Elliptic Curve Diffie-Hellman, which provide a means to exchange keys over a potentially insecure channel.
- Authentication Methods: Authentication ensures that the parties involved in the communication are indeed who they claim to be. Public Key Infrastructure (PKI) methods, often reliant on digital certificates, serve to authenticate users and devices effectively.
- Symmetric Ciphers: Once the session key is established, symmetric ciphers, such as AES (Advanced Encryption Standard) and ChaCha20, are employed to encrypt the data being exchanged. The efficiency and strength of these ciphers directly influence the security of the communication.
- Hash Functions: Hash functions, like SHA (Secure Hash Algorithm), ensure data integrity. By producing a hash value that changes if even a single byte of data is altered, they serve as a crucial tool for verifying that transmitted information has not been tampered with.
Traditional vs. Modern Ciphers
In the grand tapestry of cryptography, traditional ciphers, such as DES (Data Encryption Standard), have largely given way to stronger, more sophisticated modern ciphers. The transition towards modern encryption methods reflects a growing awareness of potential vulnerabilities within earlier algorithms. For instance, while DES had been widely used, its relatively short key length made it susceptible to brute-force attacks. Today, AES reigns supreme, favored for its resilience against known cryptographic attacks.
Christian Ethical Considerations
As Christians navigate the digital landscape, engaging with technologies such as TLS ciphers, ethical considerations must be woven into the understanding of this technological advancement. At the core of Christian teachings lies a commitment to truth and integrity. Encrypting data can serve a greater good, safeguarding not only personal information but also promoting transparency in communications, which is a fundamental principle in fostering trust among individuals, organizations, and communities.
Furthermore, the call to stewardship blesses the responsibility of digital interactions. One could argue that employing robust encryption methods aligns with the biblical exhortation to care for one another, particularly in protecting the vulnerable from potential exploitation. The digital realm, rife with threats such as data breaches and cyber attacks, necessitates the use of TLS ciphers to safeguard one’s neighbor’s information as one would one’s own.
The Future of TLS Ciphers
The landscape of encryption continues to evolve. Advances in quantum computing pose potential threats to current cryptographic methods. Emerging discussions around post-quantum cryptography aim to develop encryption techniques that remain secure even in a post-quantum world. The ongoing enhancement of TLS protocols reflects an awareness of these challenges, with organizations keen on adopting cryptographic practices that ensure long-term security for users.
Conclusion
Understanding TLS ciphers transcends mere technical knowledge; it requires an acknowledgment of their moral implications and responsibilities. As the digital realm continues to grow, fostered by an increasing reliance on online interactions, the significance of secure communications becomes ever more critical. TLS ciphers are the unsung heroes behind the curtain, tirelessly working to ensure that each packet of information transmitted over the web is guarded against prying eyes. The intersection of faith and technology reminds us that as we strive for security in our digital communications, we must also balance our actions with ethical considerations, ensuring that the tools we deploy fortify our collective responsibility towards each other.







Leave a Comment