In the vast and intricate ether of the internet, where data flows freely across invisible pathways, the assurance of security often seems elusive. Enter HTTPS, the herald of a secure web. HTTPS, an acronym for Hypertext Transfer Protocol Secure, is not merely a technological safeguard; it is, in essence, a promise—a commitment to data integrity, confidentiality, and authenticity. But what exactly does this entail? To unravel the complexities of HTTPS, one must delve into the underpinnings of SSL, its architectural framework, and its vigorous role in modern digital communication.
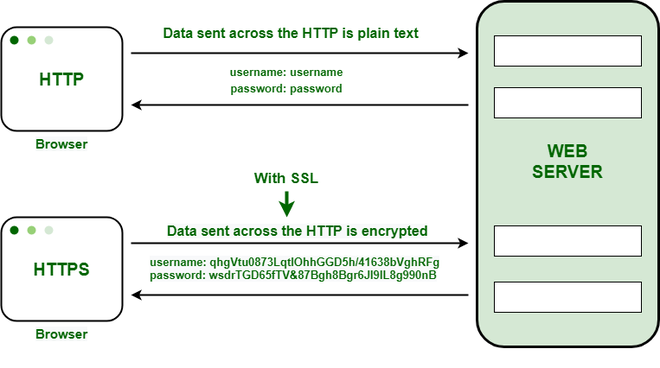
Firstly, let us dissect the lifeblood of HTTPS: SSL, which stands for Secure Sockets Layer. Although it has effectively been supplanted by Transport Layer Security (TLS), the term SSL remains entrenched in popular usage. SSL/TLS functions as a cryptographic protocol that offers a secure channel between two entities—the client and the server. This secure interaction is defined by three quintessential tenets: encryption, authentication, and integrity.
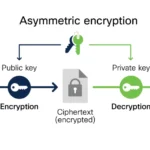
Encryption is the cornerstone of HTTPS’s allure. In a world where data packets hurled through networks may be intercepted by nefarious parties, encryption serves to cloak information in a veil of secrecy. By transforming readable data into an indecipherable format, only intended recipients armed with a unique encryption key can revert this transformation. This asymmetrical ballet between keys—public and private—ensures that potentially sensitive information, such as login credentials or financial transactions, remains safeguarded from prying eyes. The multiplication of encryption layers through the RSA and AES algorithms fortifies this security fortress.
Moving beyond encryption, the necessity of authentication surfaces as a paramount concern. Here, SSL certificates emerge as trusted third-party attestations of identity. Issued by Certificate Authorities (CAs), these digital certificates serve as a digital passport for websites. When a web browser connects to a server over HTTPS, the handshake initiated includes a verification process whereby the authenticity of the certificate is validated. This confirms that the server being accessed is indeed who it claims to be—diminishing the risk of man-in-the-middle attacks, where malicious actors impersonate legitimate entities. This verification builds trust, ensuring users can confidently engage with a website without unwarranted skepticism.
Moreover, integrity plays an instrumental role in the robust architecture of HTTPS. Throughout data transmission, mechanisms such as hashing and message authentication codes (MACs) ensure that the information remains unaltered. When data is sent and subsequently received, these mechanisms verify that no tampering or corruption occurred along the way. This constant check against alterations serves to fortify user trust, as malicious alterations are rendered ineffective—a reflexive barrier akin to a well-manned fortress guarding against siege.
HTTPS is not a mere byproduct of technological evolution; it is a testament to the shifting paradigms of internet usage. With the meteoric rise in e-commerce, the stakes have never been higher for data protection. The recent years of rapid digital transfiguration, driven by mobile devices and an ever-increasing reliance on online services, have made HTTPS not just desirable but obligatory. Websites lacking secure connections are increasingly sidelined, with modern browsers marking them with cautionary symbols, thereby directly impacting web traffic and user engagement.
From the realm of e-commerce to online banking, the applications of HTTPS go beyond the transaction. Communications on social media platforms, collaboration tools, and even personal blogs benefit from the encryption magic of HTTPS. The connectivity that once exposed vulnerabilities now becomes a fortified channel for interaction. As a user, one begins to grasp that this “lock” design in the address bar is more than visual décor; it is an emblem of assurance wrapped in a narrative of encryption, integrity, and unwavering trust.
However, HTTPS is not without its challenges. Despite its numerous benefits, the implementation of HTTPS can be complex and not devoid of potential pitfalls. Misconfigurations can leave a site vulnerable, or self-signed certificates may lead users to mistrust a web service altogether. The landscape of online security is continually evolving, with emerging threats necessitating adaptive security mechanisms. Furthermore, the transition from HTTP to HTTPS often demands additional resources—be it time for implementation or financial costs tied to certificate acquisition.
The future of HTTPS, under the auspices of initiatives like Let’s Encrypt, presents a democratization of web security, aiming to make HTTPS universally accessible. Such movements signal a paradigm shift, where secure communication is no longer a luxury but a normative expectation. This strategy aligns with the ethos of the modern internet, urging developers and site administrators to prioritize user safety unreservedly.
In conclusion, HTTPS represents a paradoxical blend of simplicity and complexity—a simple “S” added to HTTP conveys a message layered with significance: security is paramount. It is a security blanket encompassing the web in a righteous embrace, safeguarding the interactions and transactions we hold dear. By celebrating the importance of HTTPS, society can collectively shift its perspective on digital communication, evolving our understanding of security in an age of intricate technological interdependence. As the digital landscape continues to expand, let HTTPS serve as a bulwark, fostering trust and security—two vital currencies of the internet.




Leave a Comment