In the realm of cryptography, the Secure Hash Algorithm 3 (SHA-3) occupies a noteworthy position as a cryptographic hash function standardized by the National Institute of Standards and Technology (NIST) in 2015. Born out of the Keccak family of hash functions, SHA-3 signifies a departure from its predecessors, SHA-1 and SHA-2, by employing a distinct internal structure known as the sponge construction. This article delves into the intricacies of SHA-3, elucidating its operational mechanisms and contextual relevance in contemporary digital security.
Understanding Cryptographic Hash Functions
To grasp SHA-3 comprehensively, one must first appreciate the essence of cryptographic hash functions. These functions calculate a fixed-size output, known as a hash value or digest, from an arbitrary-sized input. The output retains several properties: it is deterministic, meaning consistent input produces the same hash; it is pre-image resistant, implying that one cannot feasibly derive the original input from the hash; and it is collision-resistant, ensuring that no two different inputs yield the same hash output. Additional characteristics like avalanche effect and computational efficiency further enhance their applicability in secure communications and data integrity verification.
The Genesis of SHA-3: An Overview
The development of SHA-3 emerged from the public competition initiated by NIST in 2007, intended to develop a new standard following the vulnerabilities discovered in SHA-1 and lighting a path for stronger alternatives. The Keccak algorithm, designed by Guido Bertoni, Joan Daemen, Michele Neves, and Gilles Van Assche, triumphed in this competition. Unlike its predecessors, SHA-3 utilizes different mathematical constructs, making it immune to many common attack vectors that plague traditional hash functions.
The Sponge Construction: A Unique Framework
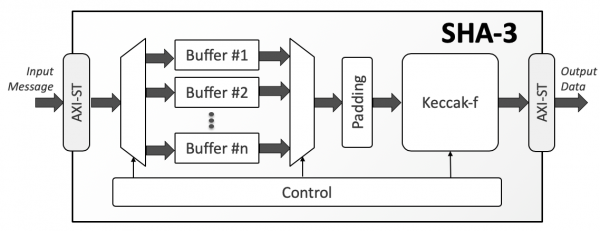
At the heart of SHA-3 lies the sponge construction—a dual-phase mechanism characterized by “absorption” and “squeezing.” During the absorption phase, input data is fed into a fixed-size internal state or “sponge.” This input is permuted and incorporated into the state, gradually leading to a more complex arrangement of bits. The absorbent nature of the sponge allows multitude data block lengths to hash effectively.
Following the integration of the data, the process enters the squeezing phase. Here, the internal state is progressively extracted to produce the hash output. The sponge construction’s advantage lies in its flexibility, allowing for various output sizes ranging from SHA3-224 to SHA3-512. It seamlessly accommodates demands for diverse security applications, such as digital signatures, message authentication codes (MACs), and random number generation.
Operational Dynamics of SHA-3
Delving deeper into the mechanics, SHA-3 operates through an iterative process orchestrated by a permutation function known as Keccak-f. This function performs alterations to the internal state through operations such as bitwise XOR, rotation, and linear diffusion. The cyclic nature of these transformations enhances confusion and diffusion properties essential for cryptographic strength.
In practical terms, when a message is hashed through SHA-3, it is segmented into blocks corresponding to the internal rate of the sponge (e.g., 1088 bits for SHA3-256). Each block is absorbed into the state, followed by the application of the Keccak-f transformation. This process continues until all data is processed. In the squeezing phase, the output is generated as specified by the desired hash length, ultimately producing the final digest.
Advantages of SHA-3
SHA-3 presents numerous advantages over previous hash algorithms. Its innovative sponge construction allows for enhanced security, as it offers resilience against length-extension attacks—an issue that plagued the earlier SHA family. Furthermore, its versatility and performance efficiency ensure that it is suitable for a wide array of applications, from blockchain technology to secure data storage solutions.
Moreover, the extensibility of SHA-3 allows for customized output sizes, permitting users to select hash lengths that best suit their security needs, a feature that isn’t as readily available in SHA-2. The fact that it is built from the ground up also contributes to its robustness—the design was crafted to resist known forms of cryptographic attacks, granting users confidence in its reliability.
Use Cases and Applications
The inherent reliability and adaptability of SHA-3 make it a staple in various technological domains. In blockchain applications, SHA-3 can serve to secure transaction data, rendering it immutable and tamper-resistant. Within digital certificates, its hashing capabilities ensure data integrity and bolster authentication protocols.
Furthermore, SHA-3’s robust hashing methodologies allow for its integration into secure communications. This includes its utility in the construction of secure messaging protocols and cryptographic digital signatures—critical components in establishing trusted online interactions. It also finds resonance in the banking sector, where transaction integrity is paramount.
Conclusion
As technology continues to evolve, the need for robust cryptographic solutions becomes increasingly vital. SHA-3 stands at the forefront of this revolution, showcasing not only a sophisticated design that bolsters security measures but also a forward-thinking approach to cryptographic hashing methodologies. Its sponge construction, unique to its architecture, reflects a stride towards adaptive and resilient encryption standards.
Embracing SHA-3 as a staple in the future of cyber security offers the promise of fortified digital communication and a steadfast shield against the myriad challenges posed by emerging technologies and threats. In an unpredictable digital landscape, knowledge of such cryptographic advancements is indispensable.








Leave a Comment