In the landscape of modern networking, security proliferates as an indispensable element. Among various protocols established to safeguard data transmission, Secure Socket Layer (SSL) emerges as a noteworthy archetype. It acts as a pivotal technology that ensures confidentiality and integrity in online communications. For individuals and organizations alike, understanding SSL is crucial, especially as the digital world burgeons.
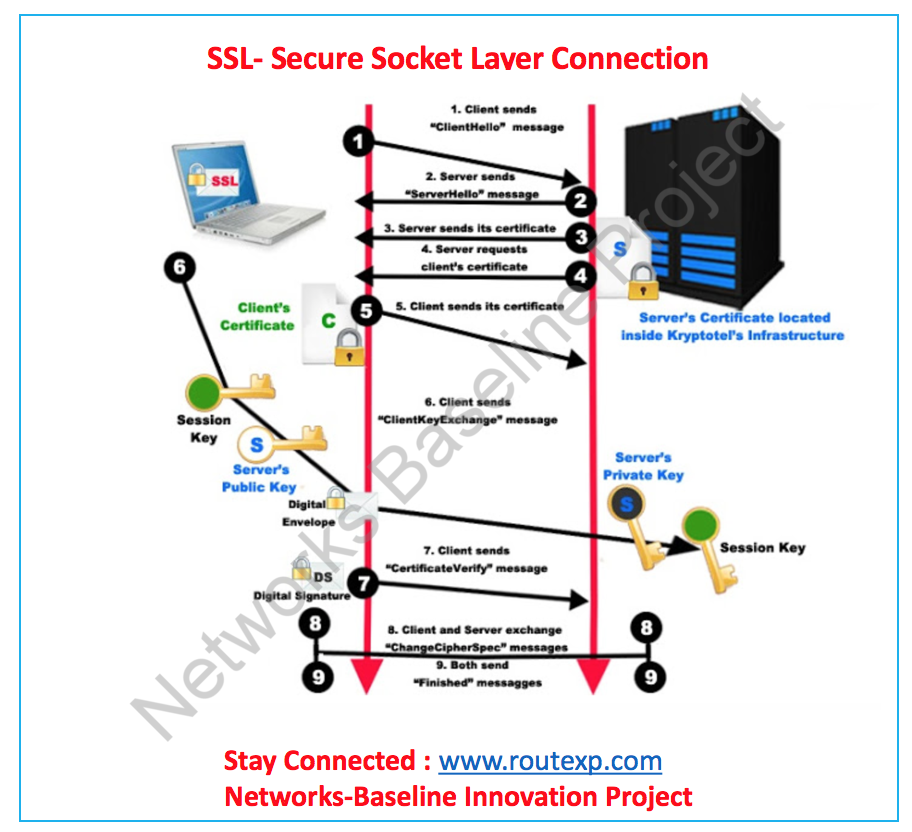
To comprehend SSL, one must first appreciate its foundational principles. SSL is a cryptographic protocol that encompasses both security and authentication measures. Its primary function helps in encrypting the data exchanged between client and server, thereby thwarting potential eavesdroppers and preventing unauthorized access. This symbiotic relationship between encryption, server authentication, and data integrity is delve into further detail.
Encryption constitutes the core of SSL. It transforms plain text into ciphertext utilizing complex algorithms, making it indecipherable to anyone lacking the requisite encryption key. This obfuscation is paramount when transmitting sensitive information such as credit card numbers, passwords, or any personal data over the internet.
Server authentication bolsters SSL’s significance within networking. It confirms that clients engage exclusively with legitimate servers, thereby mitigating the risk of man-in-the-middle attacks. These attacks transpire when an adversary impersonates a legitimate endpoint to intercept sensitive data. SSL employs digital certificates issued by trusted Certificate Authorities (CAs) to validate server identities. This validation engenders a robust web of trust that underpins secure online transactions.
Moving beyond technical intricacies, let us examine the various types of SSL certificates. Each type carries unique attributes, tailored to specific business needs. The three predominant categories include Domain Validation (DV), Organization Validation (OV), and Extended Validation (EV) certificates.
Domain Validation certificates represent the most basic form of SSL certification. CAs verify that the applicant holds ownership over the domain but impose minimal requirements for verification. Typically issued in mere minutes, DV certificates offer essential encryption yet lack comprehensive assurance about the legitimacy of the organization behind the domain.
Organization Validation certificates extend the validation layer. In this case, CAs perform a deeper investigation involving the organization’s identity. This method not only verifies domain ownership but also ensures that the entity exists and is authorized to operate the domain. OV certificates thus provide greater assurance to users, reflected in additional information presented on the certificate, such as the company’s name and location.
Finally, the Extended Validation certificate epitomizes the zenith of SSL offerings. These certificates undergo rigorous vetting processes, where CAs scrutinize the organization meticulously. Only once comprehensive documentation is provided and approved does the CA issue the EV certificate. As a result, users often see distinctive green address bars in their browsers, symbolizing an elevated level of trustworthiness. In an age fraught with digital fraud, the visibility offered by EV certificates can significantly bolster user confidence.
Transitioning from types of certificates, it’s imperative to grasp the mechanisms deployed within SSL protocols. SSL operates on a framework composed of various phases, transitioning from handshake to data transfer. Initially, during the SSL handshake, the client and server establish parameters for communication. This process encompasses the authentication of server certificates and the negotiation of encryption algorithms.
Once the handshake is complete, a secure connection materializes, enabling the exchange of data. During this phase, SSL ensures that all transmitted data is encrypted, thereby safeguarding it from potential interception. Additionally, this layer validates the integrity of the data. Even if an intruder manages to access the data stream, they would encounter meaningless encryption without the decryption key.
Moreover, the evolution of SSL leads to its successor, Transport Layer Security (TLS). Developed in response to vulnerabilities identified within SSL, TLS provides enhanced security features. Despite the transition from SSL to TLS, the term SSL remains prevalent within industry parlance, often used interchangeably. However, modern implementations predominantly utilize TLS to ensure high-level encryption.
In the context of website security, the proliferation of SSL has prompted significant shifts in how users interact with online platforms. Websites featuring SSL certificates exhibit a padlock icon in the browser’s address bar—a visual cue signifying a secure connection. This icon has become an essential trust signal, as users are increasingly cognizant of security risks online.
Consequently, the implementation of SSL has transcended basic security measures and evolved into a fundamental requirement for businesses operating online. From e-commerce enterprises to banking institutions, every domain must prioritize establishing secure connections to protect their clientele’s information. In an era where data breaches are grave threats, SSL serves as a cornerstone for cultivating trust and credibility within digital enterprises.
In conclusion, while the concept of SSL may seem intricate at first glance, the fundamentals revolve around establishing secure connections and safeguarding sensitive information. As technology advances and cyber threats grow more sophisticated, embracing SSL, along with its successor TLS, becomes indispensable for maintaining security in the digital domain. Whether one is a novice exploring network encryption or a seasoned professional reinforcing security protocols, understanding SSL’s nuances can significantly impact how data privacy issues are tackled in the contemporary digital era.







Leave a Comment