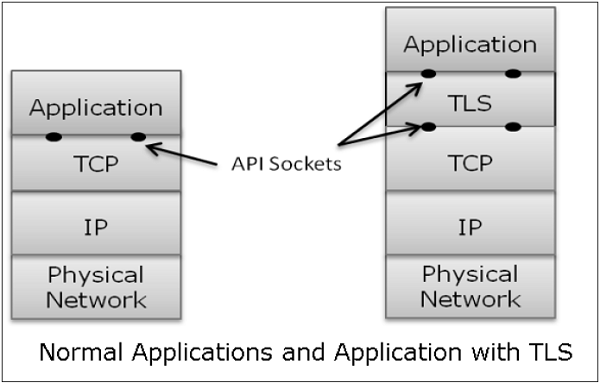
In the sprawling landscape of digital communication, the journey from TCP to TLS epitomizes the evolution of network security layers. This transformation is akin to the gradual fortification of a castle, where each layer not only enhances the defensibility of the structure but also contributes to the overall integrity of the architectural masterpiece. The tale of these technologies begins with the humble Transmission Control Protocol (TCP), a robust foundation upon which the edifice of secure communications is constructed.
At its inception, TCP plays the role of a diligent messenger, ensuring the reliable transmission of data packets across networks. Picture it as an adept courier seamlessly navigating the bustling streets of a medieval town, ensuring that each letter arrives intact and in due time. This protocol establishes a connection-oriented communication channel, meticulously managing the segmentation of data, retransmissions, and flow control. Such functionalities are indispensable, as they safeguard against the chaos of data loss and misdelivery, so every byte is a step closer toward effective communication.
However, the reliable framework of TCP lacks the armor needed to fend off the threats lurking in the shadows of the digital realm. Herein lies the shortcoming of this foundational layer; it does not encrypt data, leaving it exposed to prying eyes. In this metaphorical castle, while the walls may be sturdy, the message within remains vulnerable to eavesdroppers who can glean sensitive information from unprotected communication.
This predicament beckons the advent of Transport Layer Security (TLS), a protocol designed to envelop data in a shield of cryptographic principles. TLS can be likened to the enchanted barrier surrounding a castle, which not only deters intruders but also protects the noble inhabitants within. Enabling encryption, authentication, and integrity assurance, TLS fortifies the communication channel, ensuring that data traverses the network as securely as a royal decree sealed with wax.
The architecture of TLS is intricate yet fascinating. At its core, it is composed of three essential layers: the Record Protocol, the Handshake Protocol, and the Alert Protocol. Each of these components work harmoniously to provide a secure framework for data exchange. The Record Protocol is responsible for encapsulating the data with encryption and ensuring its integrity. Here, the user can imagine a highly skilled scribe meticulously enclosing scrolls in a protective casing, so they are impervious to the elements and adversaries alike.
As packets pass through this sophisticated system, the Handshake Protocol welcomes and verifies connections, ushering in an atmosphere of trust. This protocol is comparable to a castle’s gatekeeper, who inspects visitors for their credentials before granting passage. Through a series of exchanges, TLS establishes shared secrets that enable symmetric encryption for subsequent transmissions. Thus, trust is meticulously forged between communicating parties, akin to the establishment of alliances in medieval times.
Moreover, the Alert Protocol plays a pivotal role in this complex tapestry, alerting parties when an error arises or if an insecure connection attempt is made. This feature mirrors the watchman’s call to arms, signaling the onset of potential threats and ensuring a rapid response to vulnerabilities. TLS thus fortifies data integrity, ensuring that any tampering attempts are promptly thwarted.
The growing importance of TLS cannot be overstated in an era where cyber threats proliferate. As attacks become more sophisticated, the layers of security provided by TLS act as a bulwark, protecting sensitive information from malevolent forces. The implications of this protection are immense, encompassing various domains, from online banking to e-commerce. Consider it as a strong fortress that not only harbors its treasures but also allows merchants to trade with confidence, knowing that their transactions are secured against deceitful larceny.
Moreover, as the usage of TLS becomes ubiquitous, it is essential to comprehend the distinct advantages it confers. The enhanced privacy and confidentiality it provides are manifestations of modern security demands. When TLS envelops your online activities, it is akin to traversing a hidden path away from the prying eyes of the world. Every click and interaction, now cloaked in a veil of secrecy, ensures that only the authenticated participants can access the essence of the communication.
Furthermore, the authentication frameworks embedded within TLS lend themselves to ensuring data authenticity. The use of digital certificates, akin to sealed documents, guarantees that users are indeed who they claim to be. This prevents Man-in-the-Middle (MitM) attacks from distorting the narrative of communication. In our castle analogy, it prevents impostors from masquerading as trusted allies, safeguarding both the gate and the chamber beyond, wherein sensitive dialogues happen.
Nevertheless, the landscape of network security is perpetually evolving. Newer protocols and augmentations, such as TLS 1.3, are emerging, promising to enhance efficiency while further fortifying security measures. These advancements reflect the progression of craftsmanship within the castle walls, where builders are constantly innovating to ensure resilience against wear and tear wrought by time and conflict.
In conclusion, the journey from TCP to TLS encapsulates a narrative replete with transformation, advancement, and necessity. This evolution showcases the duality of simplicity and complexity, starkly highlighting the importance of layered security in the digital age. Just as a castle stands tall, fortified yet welcoming, the amalgamation of TCP and TLS exemplifies the unwavering commitment to safeguarding the domain of digital communication. Each layer enriches the experience, ensuring that data remains not only intact but also cherished, as it traverses the intricate pathways of our interconnected world.








Leave a Comment