In the ever-evolving sphere of digital banking, the security of sensitive customer data is paramount. Financial institutions deploy a myriad of cutting-edge encryption techniques to safeguard transactions and protect personal information from prying eyes. Among these, one particular strategy stands out: symmetric encryption. This article elucidates the encryption techniques predominantly utilized by banks, unraveling the complexities of their implementation and underlying principles.
Encryption, in its essence, is the process of converting plaintext into ciphertext, rendering the information unintelligible to unauthorized users. By employing sophisticated algorithms, banks can ensure data integrity, confidentiality, and authenticity. These objectives are pivotal in fostering trust between financial institutions and their clientele.
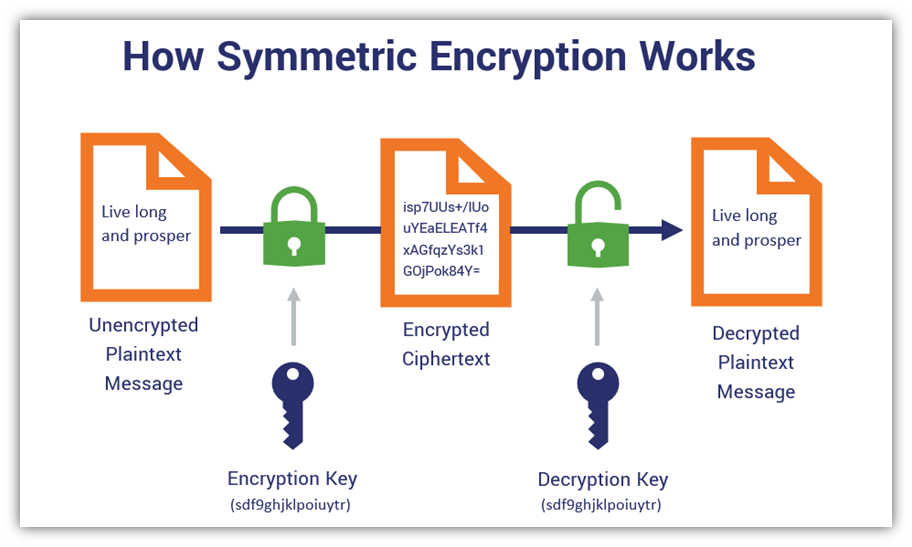
At the heart of banking encryption systems lies a dichotomy between symmetric and asymmetric encryption methodologies. While both serve a crucial purpose, their functional mechanics diverge significantly. Symmetric encryption employs a singular key for both the encryption and decryption processes, whereas asymmetric encryption utilizes a pair of keys: a public key for encryption and a private key for decryption. Most banks favor symmetric encryption due to its swiftness and efficiency, making it ideal for large volumes of transactions.
One of the most commonly used symmetric encryption algorithms is the Advanced Encryption Standard (AES). Established by the National Institute of Standards and Technology (NIST) in 2001, AES has become the gold standard for encrypting sensitive data. Its robustness lies in its key sizes, which can be 128, 192, or 256 bits. The higher the key size, the more resistant the encryption is to brute-force attacks, further enhancing the security of bank-held data.
Moreover, banks often implement AES in conjunction with other security protocols, such as the Transport Layer Security (TLS) protocol. TLS encrypts the connection between the user’s device and the bank’s servers, utilizing symmetric keys to secure the data during transmission. This combination creates a fortified barrier against eavesdropping and man-in-the-middle attacks, ensuring that customers can access their account information securely.
The practical application of AES in banking can be exemplified through the encryption of customer transactions. When a customer initiates a transfer, their banking application generates a symmetric key that is employed for the transaction. This key is ephemeral, meaning it is generated uniquely for each session and discarded once the transaction is concluded. This transient nature minimizes the risk of key compromise and fortifies data security.
However, symmetric encryption is not without its drawbacks. The paramount concern revolves around key distribution. Since the same key is used for both encryption and decryption, securely sharing this key between parties can pose substantial challenges. To mitigate this risk, banks often employ key management systems (KMS) to generate, store, and distribute keys securely. These systems utilize stringent access controls and encryption techniques to safeguard keys against unauthorized access.
As technology advances, some banks are exploring the integration of asymmetric encryption into their systems, particularly for authentication purposes. By utilizing Public Key Infrastructure (PKI), banks can establish secure authentication pathways while still relying predominantly on symmetric encryption for data transmission. This hybrid approach optimizes both security and efficiency, allowing financial institutions to provide a seamless user experience without compromising data integrity.
In addition to symmetric and asymmetric encryption, banks also employ various hashing algorithms to maintain data integrity. Hashing, unlike encryption, transforms data into a fixed-length string of characters, known as a hash value. This process is inherently one-way, making it impossible to reverse-engineer the original data. Banks utilize hashing algorithms, such as SHA-256 (Secure Hash Algorithm 256-bit), to verify transaction authenticity and safeguard sensitive information like passwords. By hashing passwords before storage, banks minimize the risk of data breaches, as stolen hash values cannot easily be deciphered without significant computational effort.
The regulatory landscape also plays a critical role in dictating encryption standards within the banking sector. Compliance with frameworks such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS) necessitates the implementation of robust encryption protocols. Failing to comply not only jeopardizes customer data but could also result in substantial financial penalties for financial institutions.
In recent years, the emergence of quantum computing poses an existential threat to conventional encryption methods. The ability of quantum computers to process vast quantities of data at unprecedented speeds could undermine the security of classic encryption algorithms. Consequently, banks are beginning to explore post-quantum cryptography, which leverages mathematical problems that are considered difficult for quantum machines to resolve. These advancements aim to future-proof banking encryption and ensure sustained consumer confidence.
In summary, most banks primarily rely on symmetric encryption, particularly the AES algorithm, to secure their transaction processes. The dual emphasis on security protocols, such as TLS, alongside key management systems, underscores the complexity and importance of maintaining robust encryption in the banking industry. As technology evolves, banks must remain vigilant and adaptive, preparing for potential threats posed by innovations like quantum computing while continuing to safeguard their customers’ financial information. The encryption landscape is continuously shifting, yet the commitment to data security remains steadfast, ensuring that customers can conduct their banking activities with confidence and ease.







Leave a Comment