In the year 2025, data encryption can be likened to a vault in a high-security bank. It is not merely a precaution; it is an imperative. As we navigate an increasingly interconnected digital landscape, the fidelity of our data is ever more paramount. Encryption stands as the modern fortress protecting sensitive information from the prying eyes of cyber intruders. Understanding the nuances and implications of data encryption necessitates a journey through its multifaceted dimensions—historical context, operational mechanics, contemporary applications, and future trajectories.
Historically speaking, the concept of encryption can be traced back to ancient civilizations, where messages were concealed using rudimentary ciphers. Fast forward to 2025, and the methods of concealing information have evolved exponentially. The once-simple Caesar shift is now replaced by advanced algorithms that baffle even the most astute hackers. Algorithms like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are the contemporary equivalent of cryptographic gold bullion—highly prized for their ability to safeguard data integrity.
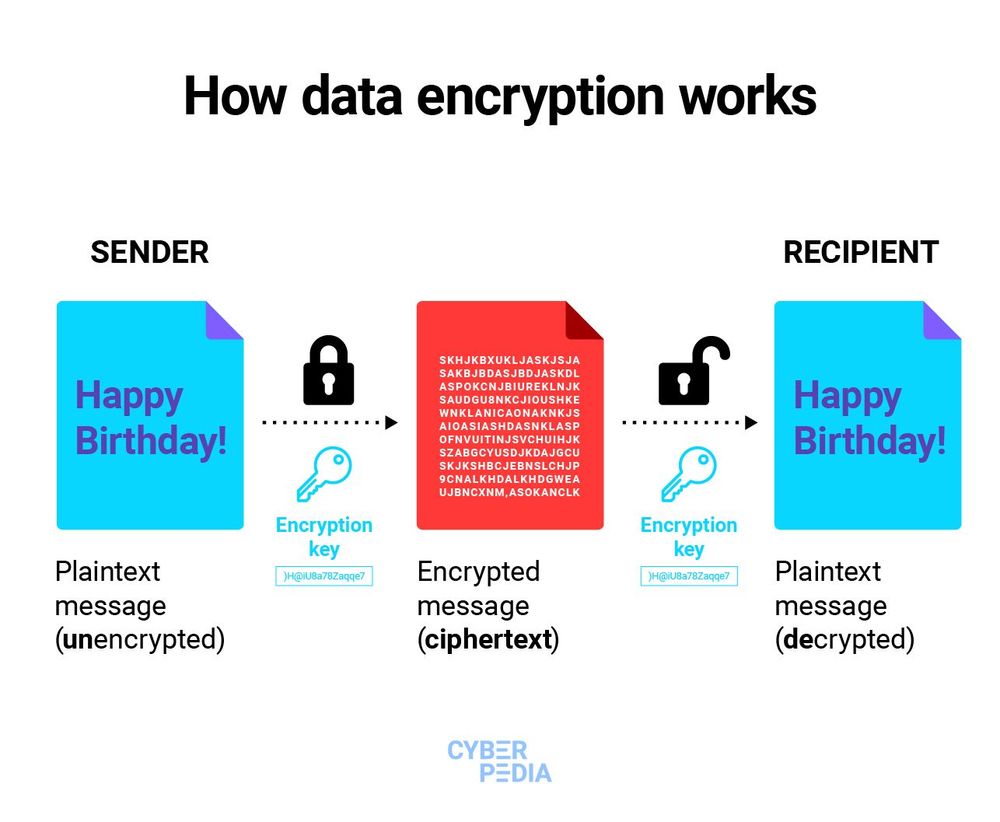
At its core, data encryption is a process that transforms plaintext into ciphertext. This metamorphosis occurs through various encryption techniques, including symmetric and asymmetric encryption. Symmetric encryption utilizes a single key for both encryption and decryption, creating a scenario akin to a shared secret. Conversely, asymmetric encryption employs a pair of keys—a public key to encrypt data and a private key to decrypt it, resembling a locked box secured by a complex puzzle. This dual-key architecture enhances security, making unauthorized access exceedingly challenging.
In 2025, the implementation of data encryption is ubiquitous, spanning various sectors. From financial institutions to healthcare providers, encryption acts as the bedrock of secure transactions and confidentiality. Personal information—whether it be your banking details or medical records—resides safely behind layers of encrypted walls. The ramifications of inadequate encryption are profound; data breaches can precipitate not just financial loss but also irreparable damage to reputations. The stakes are high; our digital existence hangs delicately on the efficacy of encryption technologies.
One significant trend shaping the encryption landscape in 2025 is the rise of quantum computing. Quantum computers wield the potential to crack traditional encryption methods with alarming speed, akin to a digital lightning bolt slicing through conventional defenses. The emergence of quantum-resistant algorithms is a race against time, reminiscent of an arms race, where cryptographers and hackers alike vie to outsmart one another. Such advancements in quantum theory will necessitate a paradigm shift in how we view and implement encryption, steering us towards post-quantum cryptography landscapes that can withstand this formidable threat.
Moreover, the concept of zero trust—an emerging cybersecurity philosophy—has gained traction. In a zero-trust model, no user or device is automatically trusted, regardless of its location within a network. Encryption plays a pivotal role in this approach, securing every data exchange with robust cryptographic measures. The metaphor of a castle under siege is pertinent here; every entry point is fortified, and access is granted only on stringent criteria, ensuring that even within the castle walls, the king’s treasure remains protected.
As we engage with data encryption in day-to-day applications, its integration into cloud computing and the Internet of Things (IoT) is critical. Data encryption ensures that sensitive information transmitted between smart devices maintains its confidentiality. For instance, smart home systems must employ encryption to prevent unauthorized access, thereby thwarting potential security breaches. Consequently, the smart home of the future will exist as a digitally reinforced stronghold, where every gadget contributes to a cohesive, secure ecosystem.
However, despite its protective qualities, data encryption is not devoid of challenges. Key management remains a formidable hurdle; misplaced or poorly managed keys can lead to catastrophic repercussions, akin to losing the only key to a highly secure safe. Additionally, complexity in deploying encryption protocols can lead to operational bottlenecks. Striking a balance between robust security measures and user accessibility is paramount. The encryption landscape in 2025 continuously evolves as technological advancements influence its integration into everyday usage.
Education on encryption is equally pivotal. In a rapidly digitalized world, end-users must grasp the significance of encryption and its applications. Cybersafety begins with awareness, ensuring individuals recognize the value of secure communication. Whether sending sensitive emails or making online transactions, an understanding of how encryption safeguards personal information empowers users to navigate the digital domain with confidence.
Looking ahead, the future of data encryption in 2025 and beyond remains a tapestry of innovation and adaptation. As technology advances, so too do the mechanisms for data protection. Encryption will grow increasingly sophisticated, evolving with emerging technologies like artificial intelligence and blockchain, each contributing to a more secure digital architecture. The complexities of maintaining a secure digital environment will perpetually demand forward-thinking solutions.
Ultimately, data encryption embodies much more than a technical jargon; it is the sentinel of our digital existence. As we venture deeper into an era that thrives on information, the importance of robust encryption practices cannot be overstated. A dynamic interplay of history, mechanics, and future considerations weaves together a narrative that underscores the significance of safeguarding our digital assets in an ever-evolving landscape.






Leave a Comment