Public key cryptography, a cornerstone of modern security protocols, floats in a realm of usability often misunderstood. The public key, an integral component of asymmetric encryption, serves dual purposes: enabling secure communications and establishing verified identities. Understanding how this key dynamically functions in everyday applications can provide insights into its comprehensive significance.
1. The Architecture of Public Key Infrastructure
At the heart of public key utilization lies the Public Key Infrastructure (PKI), a framework designed to manage security credentials and public-key encryption. The PKI establishes a hierarchy of trust through digital certificates issued by Certificate Authorities (CAs). These certificates entwine public keys with identities, thereby creating a bridge between user identities and their corresponding cryptographic keys. Without this robust architecture, the efficacy of public keys would diminish, as users would struggle to verify the authenticity of each other’s keys.
Digital certificates, teeming with pertinent information, not only certify that a public key belongs to a specific individual or organization but also delineate the issuing authority’s legitimacy. When a user attempts a secure transaction or communication, a handshake occurs: certificates are exchanged, examined, and validated. This process reinforces the underpinnings of trust that allow public key cryptography to flourish.
2. Secure Communications: The Art of Encryption
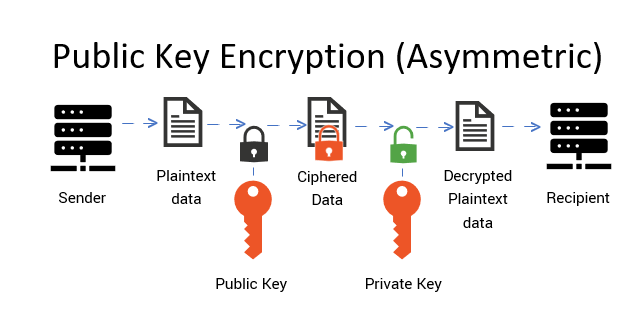
Consider the act of sending an encrypted email. The sender employs the recipient’s public key to encrypt the message. Remarkably, only the recipient’s corresponding private key can decrypt that communication. This one-way function allows the public key to roam freely in various digital landscapes without jeopardizing the secure content of the transmission. The encryption process itself is an amalgamation of mathematical operations, manipulating plaintext into ciphertext—a nearly inscrutable format that can only be deciphered through the use of the appropriate private key.
This methodology is not confined to just emails. Secure Socket Layer (SSL) protocols, which underpin web security, utilize public key cryptography when establishing secure connections between browsers and servers. When a user navigates to an encrypted website, the initial connection process employs the server’s public key to establish a secure channel. The apparent seamlessness of this interaction belies the sophisticated mechanics at work, exemplifying the elegance of public key usage across domains.
3. Digital Signatures: Authenticating Identity
Public keys extend beyond merely encrypting information; they also play a crucial role in authentication through digital signatures. A digital signature, akin to a handwritten one, guarantees the integrity and authenticity of digital correspondence. When a user signs a document with their private key, they create a signature that anyone can verify using the corresponding public key. Thus, the public key functions as a beacon of trust, allowing recipients to ensure that the document has not been tampered with and that it genuinely originates from the purported sender.
This mechanism is pivotal in various sectors, particularly in legal and financial transactions. Contracts signed electronically, for instance, garner the same legitimacy as their physical counterparts when bolstered by digital signatures. The legal implications are profound, as they enable remote transactions to proceed with the same rigor and reliability as traditional methods.
4. The Imperative of Key Management
Despite the undeniable advantages of public key utilization, challenges arise in the management of keys, which plays a crucial role in the efficacy of cryptographic systems. Public keys need to be safeguarded from manipulation or impersonation; otherwise, malicious actors could undermine the very tenets of cryptography. Key management encompasses the generation, distribution, and storage of keys, necessitating stringent protocols to mitigate risks associated with key exposure or loss.
Specifically, the dissemination of public keys often occurs through key servers or directories where they are made publicly accessible. However, without adequate mechanisms to verify the legitimacy of keys stored in these repositories, users risk falling prey to man-in-the-middle attacks. The assurance that users are working with the correct public key, verified through mechanisms such as web of trust or Certificate Authorities, is paramount. This facet of the public key ecosystem invites scrutiny and continuous evolution in security measures.
5. Cryptocurrencies: A Modern Manifestation
The cryptocurrency realm exemplifies public key application in contemporary financial contexts. In this ecosystem, users generate pairs of keys—public and private—to facilitate transactions on a decentralized ledger. The public key serves as an address for receiving funds, while the private key functions as the means to access and control those funds. This paradigm shift from traditional banking systems showcases the potent capabilities of public key cryptography in fostering secure, peer-to-peer transactions unencumbered by intermediaries.
The implications of such innovations are profound, challenging the conventional paradigms of finance and ownership. However, they also underscore the stakes involved in key management, as the irrevocability of transactions in cryptocurrencies places the burden of security squarely on the users’ shoulders.
6. Ongoing Challenges and Future Directions
As technological landscapes evolve, so do the methodologies and challenges associated with public key cryptography. Quantum computing, for instance, poses experiential risks to traditional public-key algorithms, prompting research into quantum-resistant cryptographic methodologies. Awareness of such threats cements the importance of continuous advancements in public key practices, along with an underlying commitment to maintaining security ecosystems robust against emerging vulnerabilities.
In summary, a person’s public key is far more than a mere cryptographic accessory. It is a pivotal instrument that influences communication security, authenticates identities, and heralds the forefront of digital transactions. Understanding its multifaceted applications not only demystifies but also illuminates the profound intricacies of modern cryptographic practices, laying the foundation for a secure and resilient digital future.







Leave a Comment