Throughout history, the art of cryptography has evolved from simple ciphers into complex systems of secrecy that have captivated and perplexed individuals across cultures. The greatest ciphers ever devised are not just intriguing puzzles; they embody rich histories, contexts, and technological advancements that reflect the minds behind them. In this exploration, we delve into the compelling world of these ciphers, examining their construction, purpose, and the inspiration they continue to provide in our modern age.
1. The Caesar Cipher
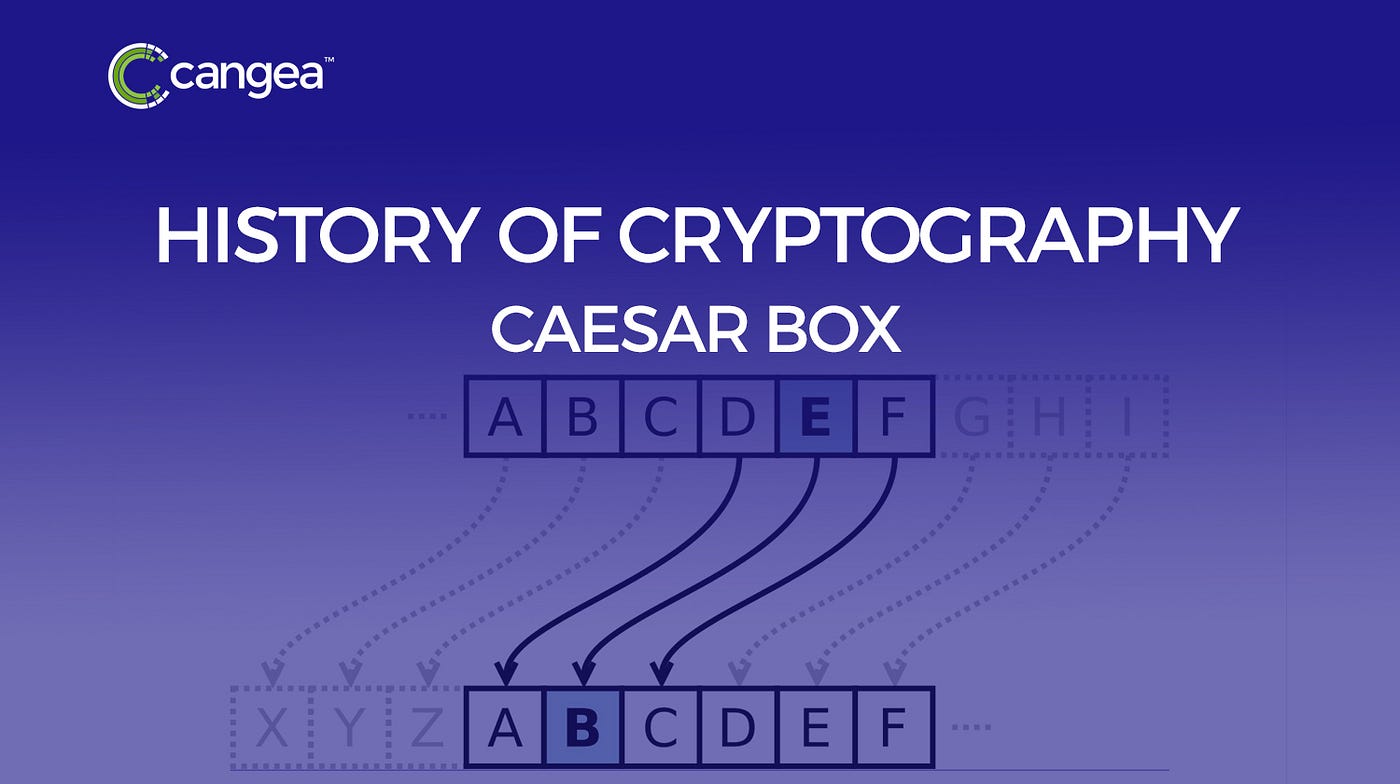
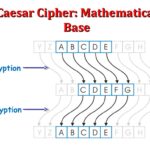
One of the most rudimentary and antiquated forms of encryption, the Caesar cipher dates back to Julius Caesar himself, who purportedly used it to secure his military communications. This substitution cipher arose from rotating the alphabet by a predetermined number of places, commonly three. While deceptively simple, the Caesar cipher serves as a foundational touchstone in the evolution of cryptography.
The elegance of the Caesar cipher lies in its simplicity; anyone who understands the shift can decode it. While it may seem elementary in today’s context, it represents the pivotal moment when the need for secrecy became paramount. Its enduring presence in popular culture—often discussed in classrooms and featured in films—showcases its continued relevance, compelling users to rethink the complexity and usability of cryptographic methods.
2. The Vigenère Cipher
Emerging from the shadows of Renaissance Europe, the Vigenère cipher introduced a significant leap in the realm of cryptography by employing a keyword to vary the shift for each letter of the plaintext. This polyalphabetic cipher obscured the frequency analysis that plagued simpler substitution techniques, making it significantly harder to crack. The beauty and strength of the Vigenère cipher lie in its intricate repetition of letters from a keyword, creating a tapestry of complexity that invites guiard against amateur cryptanalysis.
This cipher, dubbed “le chiffre indéchiffrable” or the “indecipherable cipher,” was employed by nobility and diplomats to conceal sensitive correspondence. Its presence in literature and espionage infuses it with an alluring mystique. In contemporary times, it urges cryptographers to contemplate the vast landscape of encryption methods that can evade prying eyes.
3. The Enigma Machine
Perhaps one of the most iconic ciphers of the 20th century, the Enigma machine played a crucial role in World War II, safeguarding German military communications. With its rotating rotors and plugboard configuration, the Enigma operated as a complex polyalphabetic substitution cipher, rendering intercepted messages nearly impenetrable. The ingenuity behind the machine’s design reflected the era’s technological advancements, intertwining mathematics, engineering, and cryptography.
The Enigma cipher’s allure lies not only in its construction but in the monumental effort required to decipher it. The work of cryptanalysts like Alan Turing laid the groundwork for modern computing while simultaneously unmasking the encryption that had confounded so many. The lasting impact of the Enigma machine continues to inspire intrigue in both cryptographic and technological fields, serving as a reminder of the delicate dance between secrecy and discovery.
4. The RSA Algorithm
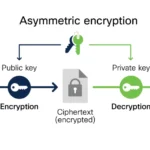
Transitioning from mechanical to digital, the RSA algorithm looms large in the landscape of contemporary cryptography. Developed in the 1970s by Ron Rivest, Adi Shamir, and Leonard Adleman, this asymmetric encryption method relies on the properties of prime numbers to secure data transmission over the internet. RSA’s significance is underscored by its foundational role in secure communications—be it for online banking, email, or any digital platform demanding assured privacy.
What makes RSA captivating is its duality: while the public key can freely encrypt messages, the corresponding private key is an obscure secret known only to the recipient. The immense mathematical complexity involved in factoring large primes adds a layer of security that continues to withstand the test of time. As the digital age flourishes, RSA serves as silent sentry, protecting the integrity of our most sensitive data.
5. The One-Time Pad
Lauded by many as the only truly unbreakable cipher, the one-time pad requires a random key that is as long as the message itself. When properly implemented, this method provides absolute secrecy, as the encryption is so statistically complex that whatever is received bears no discernible patterns. This cipher’s transience and exclusivity echo the ephemeral nature of secrets themselves.
The philosophical implications of the one-time pad stir curiosity—its reliance on an unshared key emphasizes trust between entities. As cybersecurity threats evolve, enthusiasts and professionals alike often reflect on the pristine simplicity and moral dilemmas surrounding the one-time pad, sparking discussions on privacy, ethics, and the value of information in the digital age.
6. Contemporary Ciphers: The Post-Quantum Landscape
In an era where quantum computing threatens to upend traditional encryption standards, researchers are already at work developing post-quantum cryptography. This ongoing pursuit is indicative of the relentless human endeavor to secure information against emerging threats. Ciphers such as lattice-based and hash-based encryption open the door to new methodologies, inspiring curiosity in their potential to reshape how security is conceptualized in our increasingly interconnected world.
The fascination with these new frontiers reflects an intrinsic motivation to protect what is sacred in our digital interactions. As we advance into this new era, the quest for unbeatable codes continues to captivate the imagination of cryptographers and technology enthusiasts alike.
Conclusion
The ciphers mentioned in this exploration each carry a slice of history, embodying human creativity and resilience against the forces of adversity. From the basic Caesar cipher to the complex Enigma machine and beyond, these cryptographic marvels inspire us to reconsider not only the nature of secrecy but also the profound relationship between communication and security. As we persevere in the search for new methods, the legacy of these enigmatic creations fuels our curiosity for what lies ahead in the realm of cryptography.




Leave a Comment