Data Encryption Standard (DES) is an encryption algorithm that has played a pivotal role in the development of cryptographic systems. Initially adopted in the 1970s, DES has undergone extensive scrutiny and evaluation over the decades, leading to a rich diversity of discourse regarding its advantages, disadvantages, and modern alternatives. This article aims to elaborate on the multifaceted aspects of DES encryption, dissecting its operational dynamics and the surrounding implications.
Understanding DES Encryption
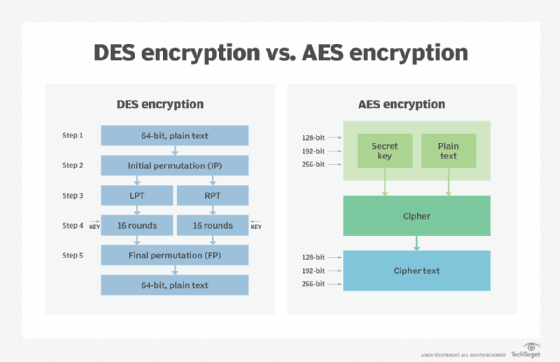
At its core, DES is a symmetric-key block cipher that employs a fixed-size key of 56 bits to encrypt and decrypt data in 64-bit blocks. Although it may seem rudimentary by today’s standards, DES was groundbreaking at the time of its inception. Utilizing a series of permutations and substitutions, it transforms plaintext into ciphertext through 16 iterations of complex operations. The majority of its cryptographic strength hinges on the process of diffusion and confusion, wherein the data complexity obscures any inferential attempts to derive the original message without the key.
Advantages of DES Encryption
Despite its vulnerability to modern attacks, DES encryption boasts several advantages. Firstly, its simplicity merits notable attention. The relatively elementary algorithm design enables fast encryption and decryption processes, allowing it to be efficiently implemented across hardware and software platforms. This efficiency is vital for systems requiring real-time encryption, such as telecommunications.
Moreover, extensive implementation of DES has led to broad support across various systems, notwithstanding its historical significance. The ubiquity of DES resulted in the development of numerous tools and libraries, making it readily accessible to developers and organizations around the globe. Thus, for entities with legacy systems, transitioning from DES might necessitate a significant overhaul.
Another noteworthy benefit of DES is its clear specification. The standardization process ensured a level of transparency, which aids in the scrutiny and formal testing of its security properties. As a well-researched algorithm, countless studies have been conducted on DES, yielding insights that refine our understanding of its security landscape.
Disadvantages of DES Encryption
In stark contrast to its merits, there are severe drawbacks to using DES in contemporary applications. Foremost among these is its key length. A mere 56-bit key length renders DES highly susceptible to brute-force attacks. With the exponential growth of computational power, this vulnerability has become more pronounced, raising alarms in the cryptographic community. Modern hardware can execute billions of possible key combinations every second, which effectively nullifies the algorithm’s initial strength.
Another drawback resides in the nature of the encryption itself. DES is characterized by its fixed-size blocks of 64 bits. Consequently, it may result in a phenomenon known as “birthday attacks,” where collisions in the ciphertext can occur. Such collisions introduce additional vulnerabilities that attackers can exploit. While DES employs a series of permutations and substitutions to obscure data, the rigidity of its block size limits flexibility and opens avenues for cryptanalysis.
Furthermore, DES’s design incorporates a relatively simple structure, which, while advantageous from a performance perspective, poses significant risks. Its predictability, when combined with inadequate key management practices, can lead to dire outcomes. Because DES does not inherently provide adaptability against emerging threats, this shortcoming further compromises its reliability in a digital landscape marked by perpetual advances in attack methodologies.
Alternatives to DES Encryption
Another notable alternative is the Triple DES (3DES), which enhances the security of DES by applying the algorithm three times with different keys. Though it provides a significant improvement over standard DES, 3DES still struggles with performance issues in environments demanding high-speed encryption. It is gradually being phased out in favor of AES due to the inefficiency and computational overhead it introduces.
Furthermore, Elliptic Curve Cryptography (ECC) also merits consideration as a contemporary alternative. ECC offers high levels of encryption strength relative to smaller key sizes. Its efficiency makes it suitable for resource-constrained devices, enabling robust security without the burden of extensive computational demands. This adaptability has positioned ECC as an increasingly favorable choice in modern cryptographic systems.
Conclusion
In summary, while DES encryption has its advantages, such as simplicity and historical relevance, its numerous disadvantages make it an inadequate choice for contemporary security needs. The algorithm’s vulnerabilities, particularly due to its insufficient key length, have ushered in a wave of advanced alternatives. AES, Triple DES, and ECC present varied solutions to the challenges posed by DES, steering the cryptographic landscape towards more formidable and adaptive encryption strategies.
Ultimately, organizations must weigh their specific security requirements against the potential risks and benefits offered by DES and its alternatives. As technology continues to evolve, so too must our approaches to encryption, ensuring that sensitive data remains secure in an increasingly interconnected world.








Leave a Comment