RSA (Rivest-Shamir-Adleman) has long been hailed as a cornerstone of public key cryptography, underpinning countless secure communications across the globe. However, over time, it has become increasingly evident that this algorithm exhibits significant limitations in online applications. This article elucidates these constraints, providing a comprehensive overview of RSA’s shortcomings in contemporary digital environments. From key size implications to computational inefficiencies, the following sections delve into the multifaceted challenges posed by RSA.
1. Key Size and Security Paradigms
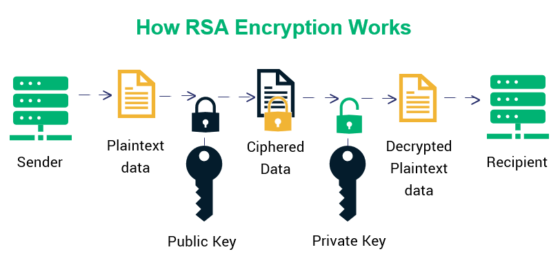
At the heart of RSA’s security lies its key size. As cyber threats evolve, the requisite key length for RSA to remain secure has skyrocketed. Originally deemed sufficient, a 1024-bit key is now considered vulnerable to modern computational capabilities. Security experts now recommend using 2048-bit or even 4096-bit keys. However, there’s a corollary: the larger the key, the more computationally intensive the encryption and decryption processes become. As a result, the practical application of RSA becomes riddled with trade-offs. Increased key size results in sluggish performance, which can drastically affect the responsiveness of online applications.
2. Computational Intensity
The RSA algorithm is inherently computationally intensive. Unlike symmetric key algorithms, such as AES, which can process data in parallel, RSA relies on operations that require significant CPU cycles. This is particularly problematic in environments where speed and efficiency are paramount. For instance, consider online payment systems that require rapid transaction processing. The reliance on RSA for securing these transactions can introduce latency, ultimately impairing user experience. Furthermore, devices with limited processing power—such as mobile phones or IoT devices—struggle with the heavy computational demands of RSA, resulting in unreliable performance.
3. Production of Key Pairs
Generating RSA key pairs consists of computationally demanding tasks, primarily the multiplication and division of large prime numbers. This resource-intensive process can lead to bottlenecks, especially when multiple key pairs need to be created simultaneously, such as in user authentication systems for web applications. The latency introduced during this operation can pose significant challenges for scalability, making RSA less favorable for applications requiring rapid user onboarding and session establishment.
4. Vulnerability to Quantum Computing
As the realm of cryptography continues to evolve, the advent of quantum computing looms large. Theoretical advancements suggest that quantum computers could efficiently execute Shor’s algorithm, which is capable of factoring large numbers in polynomial time—rendering RSA’s encryption practically obsolete. Although practical quantum computers are still a work in progress, the impending disruption they bring alters the landscape of cryptographic security. Organizations leveraging RSA may find themselves vulnerable and underprepared for an epoch wherein quantum decryption capabilities become reality. Transitioning to quantum-resilient algorithms is necessary, but the logistical hurdles of swapping established systems for novel solutions cannot be underestimated.
5. Lack of Forward Secrecy
Forward secrecy is a crucial feature in modern cryptographic protocols. It ensures that session keys are not compromised even if the private key is exposed later. Unfortunately, RSA does not inherently provide forward secrecy. In scenarios where an RSA private key is disclosed, past communications protected under that key become susceptible to decryption. This limitation signifies a notable security gap, particularly detrimental in sensitive exchanges such as legal communications or financial transactions, where confidentiality is paramount.
6. High Forgeability of Signatures
RSA’s signature verification process, while efficient, can be undermined by its deterministic nature. A crucial realization is that an adversary with sufficient computational resources can generate a multitude of plausible signatures for a given message. The potential for signature forgery remains an inherent risk. This is particularly worrying for scenarios that rely on asserting authenticity and integrity, such as software distribution or digital contracts. Each time an RSA signature is used, the risk of facing a forged signature rises, thereby jeopardizing the integrity of communication protocols.
7. Legal and Compliance Considerations
The use of RSA in online applications may not align with the evolving legal landscape surrounding data protection and cybersecurity. Compliance with standards such as GDPR or CCPA mandates rigorous security measures for the protection of personal data. While RSA can provide a level of security, staying compliant often necessitates additional layers of encryption and security controls. The complexities associated with managing key lifecycles, adopting best practices, and ensuring proper key storage and disposal make RSA a cumbersome choice for organizations aiming to adhere to legal standards.
8. The Rise of Alternative Algorithms
With the limitations of RSA becoming increasingly pronounced, alternative cryptographic algorithms are emerging. Elliptic Curve Cryptography (ECC), for instance, provides equivalent security to RSA but with significantly smaller key sizes. This not only enhances efficiency but also reduces the computational load, thus transforming the viability of secure communications in scenarios with resource constraints. As industry standards evolve, more organizations are migrating toward these alternative solutions, raising questions about the future relevance of RSA.
Conclusion
The utility of RSA in online applications is increasingly compromised by various factors. Key size requirements, computational intensity, vulnerability to quantum threats, and legal challenges contribute to a landscape where RSA may no longer be the optimal choice. As organizations strive for secure, efficient, and compliant frameworks, understanding these limitations is crucial in guiding the transition toward more robust cryptographic solutions. As the discourse surrounding digital security progresses, the need for comprehensive strategies to address these challenges becomes paramount for securing the digital frontier.







Leave a Comment