Throughout history, the art of cryptography has captured the imagination of scholars and enthusiasts alike, serving as a tantalizing riddle wrapped in an enigma. One of the most iconic ciphers in the annals of cryptography is the Caesar Cipher. Named after Julius Caesar, who reportedly employed it for secure military communications, this ancient technique has transcended its immediate historical context, evolving into a fascinating subject that continues to intrigue modern minds. Today, we’ll delve into the intricacies of breaking Caesar’s Cipher, employing classic techniques that not only unravel its mysteries but also amplify our appreciation for the craft of cryptography.
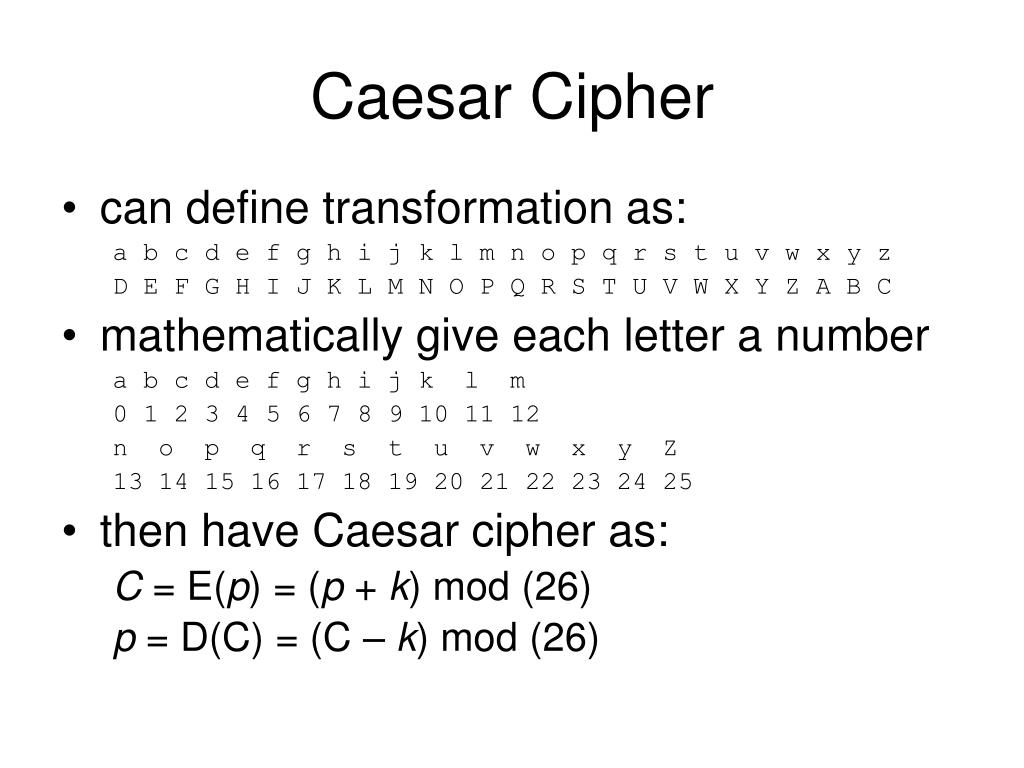
At its core, the Caesar Cipher is a substitution cipher, wherein each letter in the plaintext is shifted a fixed number of places down or up the alphabet. For instance, with a shift of three, A becomes D, B becomes E, and so on. Despite its simplicity, the cipher represents a fundamental concept in cryptographic history: that of transposition. This reconfiguration of letters can be likened to rearranging furniture in a room—though the essence remains unchanged, the appearance alters dramatically, potentially obscuring the true nature of the contents.
To the modern mind, one might liken the endeavor of cracking a Caesar Cipher to solving a complex jigsaw puzzle. The pieces are scattered, and while the outline of the picture provides a framework, it’s only through careful analysis and manipulation that the full image can be revealed. A keen observer notices that the Caesar Cipher, while elegantly simple, is not impervious to the scrutiny of astute cryptanalysts.
The first technique that emerges in our toolkit for deciphering Caesar’s Cipher is **brute force**. In its essence, brute force denotes the exhaustive method of attempting every possible shift until the original message is unveiled. Given that the English alphabet comprises just 26 letters, one can hypothesize a mere 25 potential shifts. The chromatic beauty of this technique lies not only in its simplicity but also in the anticipation it generates. Each decryption reveals a new facet of the enigma, much like peeling back layers of an onion. Yet, this method, while straightforward, often lacks sophistication—akin to bludgeoning a door down when a key exists that fits perfectly.
As one delves deeper, the metaphorical toolbox of cryptanalysis expands, leading us to the **frequency analysis** technique. Knowledge of letter frequency in the target language catalyzes more informed decryption efforts. In English, for instance, the letter ‘E’ reigns supreme as the most frequently occurring character, followed by ‘T’, ‘A’, and ‘O’. By mapping these frequencies against the letters appearing in the encrypted text, one can hypothesize which letters correspond to one another. This process is a dance between intuition and deduction, orchestrated by the frequency of letters—a graceful ballet in the realm of cryptography.
Understanding the common digraphs and trigraphs—pairs and triplets of letters—enhances this analysis. Recognizing common combinations, such as ‘TH’, ‘HE’, and ‘IN’, equips the cryptanalyst with additional contextual clues. When one observes that certain letter pairings appear unusually frequently, it signals a likely shift, revealing patterns that may lead to the original plaintext. The interplay of frequency is analogous to interpreting a jazz composition: the notes played create an underlying rhythm, and through concerted effort, the melody emerges.
Beneath the surface of frequency analysis, the technique of **contextual clueing** comes into play. Here, the cryptanalyst not only deciphers letters but interprets meaning through context. This strategy involves anticipating potential words based on the subject matter or thematic elements of the content. By gauging the structure of language, one can surmise likely candidates for words. In a Caesar encrypted message about victory in battle, words such as ‘victory’, ‘battle’, or ‘strategy’ may surface as prime targets for deciphering. Contextual understanding lays the framework for intelligence gathering, akin to solving a detective mystery where whispers of the past coalesce into a coherent narrative.
Though historical methods hold their appeal, the advent of technology has birthed tools that exponentially amplify our capabilities. With the birth of modern digitization, the **power of algorithms** has transformed the landscape of cryptanalysis. Computational tools can execute brute-force attacks and frequency analyses at lightning speed, illuminating pathways that were once obscured. Algorithms formulated for cryptography hyperaccelerate the journey from cipher to plaintext, unraveling secrets in the blink of an eye.
The intersection of history and technology enriches the discourse surrounding the Caesar Cipher. It becomes a testament to human innovation, reminding us that while the techniques may evolve, the underlying principles remain enduring. The challenge lies in preservation and adaptation, as cryptography continually metamorphoses with each new technological advance.
As we traverse this landscape of codes and ciphers, we uncover that breaking the Caesar Cipher is not merely a task—it is a cerebral expedition filled with puzzles, clues, and revelations. Each technique provides insight not only into the cipher itself but into the minds of those who crafted and sought to break it. The elegance of simplicity intertwines with the complexity of human thought—creating a dance that spans centuries.
Ultimately, the process of breaking Caesar’s Cipher offers a compelling glimpse into the vast realm of cryptography, revealing a rich tapestry of methods that bridge ancient traditions with contemporary applications. As minds of today grapple with the vestiges of the past, the exploration of classic techniques crafted for this age-old cipher ignites a passion for decoding mysteries, proving that the pursuit of knowledge, in all forms, remains a timeless endeavor.







Leave a Comment