Brute force attacks, a method of breaking into systems by exhaustively guessing passwords and encryption keys, continue to be a significant concern in the digital realm. As we leap into 2025, one must ponder: are these attacks still as effective as they once were? This exploration delves into the architecture of brute force attacks, the advancements in countermeasures, and the evolving landscape of cyber threats.
At the core of brute force attacks lies an elementary principle: trial and error. By systematically attempting every possible combination of characters until the correct one is uncovered, malicious actors exploit computational power and time. While traditional brute force attacks target static passwords, variations such as dictionary attacks mine from a database of common passwords, leveraging the tendency of users to create easily guessable codes. This simple yet insidious approach has been enhanced with technical advancements, allowing attackers to deploy sophisticated algorithms and utilize high-performance computing resources to expedite the process.
Recent years have witnessed an astonishing leap in computing capabilities. With the advent of multi-core processors, GPUs, and cloud computing, the ability to conduct brute force attacks has exponentially increased. Notably, the use of botnets—assemblies of compromised computers—enables attackers to coordinate vast numbers of simultaneous attempts. Consequently, this begs the question: can systems withstand these relentless onslaughts as technology continues to accelerate? As systems advance, so too do the tactics employed by cybercriminals.
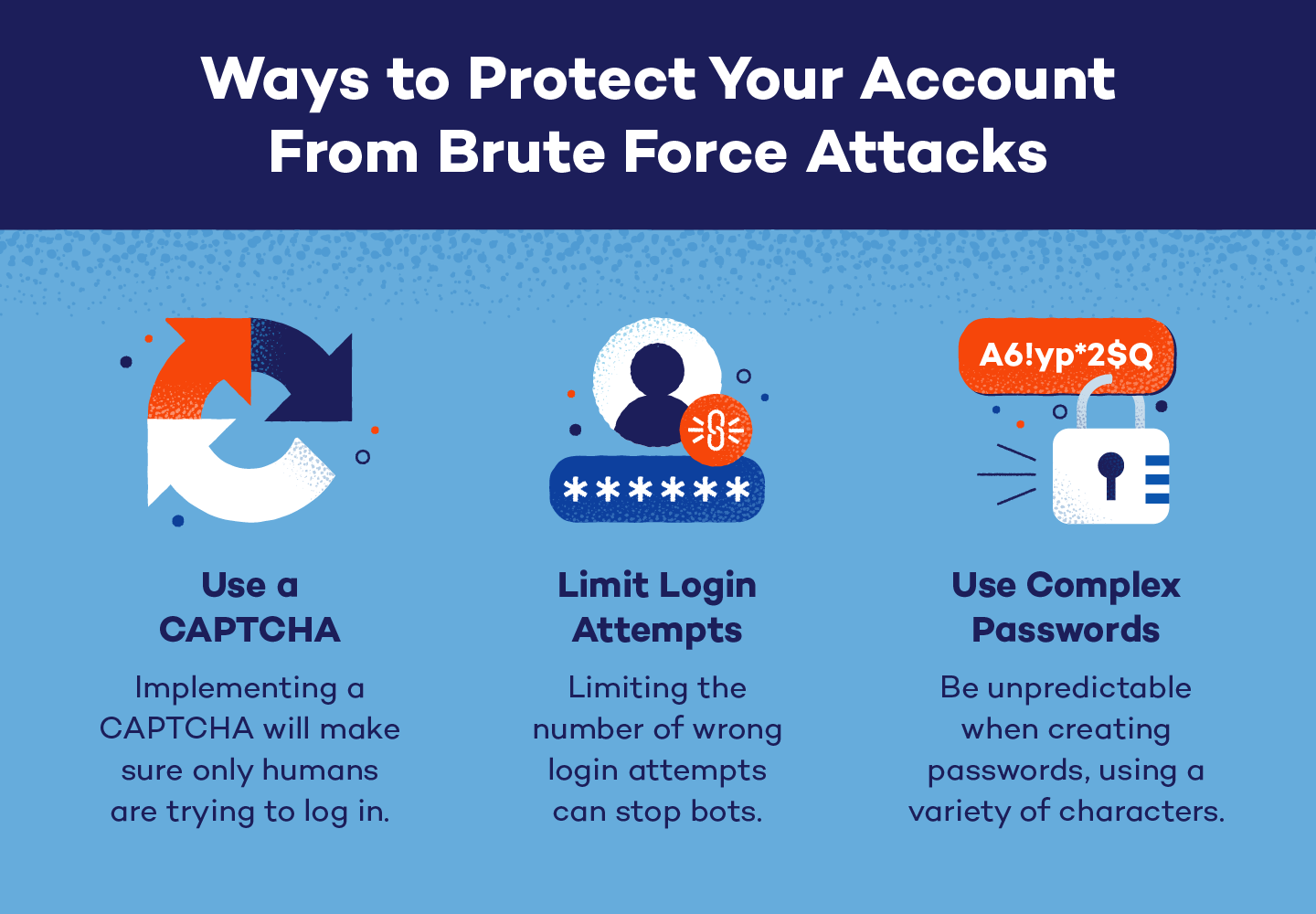
However, the mitigative measures adopted by organizations have become increasingly effective in elongating the time required for a brute force attack to succeed. Multi-factor authentication (MFA), for instance, serves as a formidable barrier against attacks. By necessitating not only a password but also additional verification methods—such as biometric scans or one-time codes—MFA complicates the attacker’s path. The introduction of time-based one-time passwords (TOTPs) further nullifies the efficacy of brute force strategies, rendering many password attempts futile.
Another pivotal development in combating brute force attacks is the implementation of account lockout policies. When numerous incorrect attempts are made within a set timeframe, account access is temporarily suspended. This strategy not only impedes the attack but also alerts users to potential security violations. Often employed in tandem with CAPTCHA systems, these practices represent a substantial bulwark in the face of automated login attempts.
Security professionals advocate for the adoption of password complexity requirements, mandating longer and more intricate passwords that blend letters, numbers, and special characters. While such measures may seem rudimentary, they exponentially increase the number of possible password combinations, thus amplifying the time required for a successful brute force attempt. Educating users about the importance of password hygiene can significantly mitigate risks, as awareness remains a formidable weapon in a digital arsenal. By encouraging practices such as password managers and the avoidance of password reuse across platforms, individuals can bolster their defenses substantially.
The evolution of machine learning (ML) and artificial intelligence (AI) is poised to transform the landscape of cybersecurity. With the ability to differentiate patterns and detect anomalies, advanced security systems that integrate these technologies can identify unusual login behaviors indicative of an ongoing brute force attack. By employing predictive analytics, organizations can proactively thwart attacks before they escalate, showcasing an evolution from reactive to proactive security measures.
Yet the menace of brute force attacks remains, as cybercriminals tirelessly adapt to new technologies. The trade-off between security and usability is also a pervasive dilemma. The introduction of more complex security measures can inadvertently frustrate users, leading to poor adherence and possible security lapses. This presents a continuous challenge for organizations seeking to balance user experience with robust security protocols.
Biometric authentication has emerged as a potential alternative to traditional password systems. Utilizing unique physiological traits, such as fingerprints, facial recognition, or retinal scans, biometric systems introduce an additional layer of protection. However, these systems are not impervious to attack; the potential for spoofing and the ethical implications surrounding privacy raise substantial concerns that must be addressed as the technology matures.
In 2025, the effectiveness of brute force attacks hinges on various factors: the fortification of user credentials, the adoption of state-of-the-art authentication mechanisms, and the ceaseless innovation within the cybercrime sphere. While brute force attacks may not be as commonplace as they once were, they still represent a plausible threat to inadequate systems. As both attackers and defenders refine their techniques, remaining vigilant is essential.
In conclusion, the ongoing arms race between cybersecurity efforts and cyber threats underscores the dynamic nature of digital security. Although brute force attacks maintain a level of efficacy, the advancements in mitigating technologies—coupled with user awareness and strategic password management—render these attacks less likely to succeed against properly fortified systems. The imperative for continued evolution in security measures is clear; the challenge lies in sustaining this momentum as technology and tactics evolve further. In the digital age, complacency is a luxury that no organization can afford.







Leave a Comment