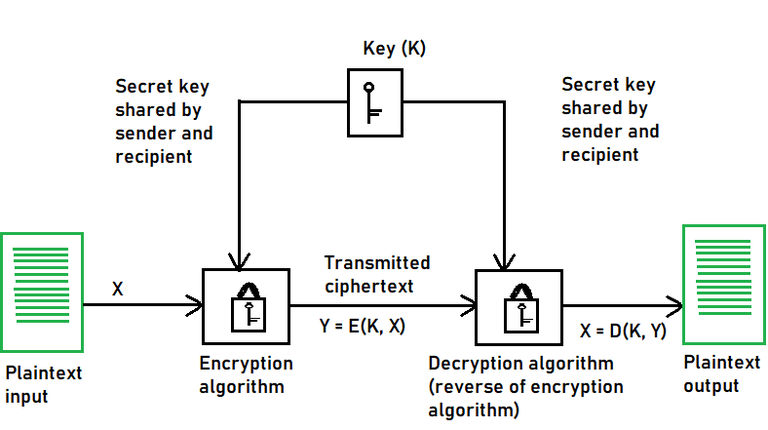
In the intricate realm of cryptography, one term often surfaces with auspicious regularity: symmetric key encryption. Imagine a world wherein communication is shielded from prying eyes, wielding the psychotic precision of mathematical algorithms. What are the advantages of employing symmetric key encryption in real-world scenarios? This inquiry invites exploration into the calculus of security, efficiency, and practicality. Moreover, while this encryption method is regularly lauded, are there challenges lurking in the shadows? Let’s delve into the sinews of symmetric key encryption’s advantages across diverse applications.
1. Simplicity and Speed
At the pinnacle of symmetric key encryption’s advantages lies its intrinsic simplicity. Unlike asymmetric methods that utilize a pair of keys—a public and a private key—symmetric encryption requires a solitary key for both encryption and decryption. This duality renders it not only straightforward but also expeditious. Algorithms such as AES (Advanced Encryption Standard) operate with remarkable swiftness. Data encryption and decryption can occur in mere milliseconds, a characteristic that is critical for applications requiring real-time processing, like credit card transactions or instant messaging.
2. Resource Efficiency
Another contender for the crown among symmetric key encryption’s virtues is its efficient consumption of resources. The algebraic operations underpinning symmetric encryption are relatively low in computational complexity. This efficiency becomes particularly salient in environments with limited resources, such as IoT (Internet of Things) devices. In these contexts, where processing power and battery life are at a premium, the lightweight nature of symmetric encryption stands as a formidable ally.
3. Scalability
In any burgeoning enterprise, scalability is the holy grail. Symmetric key encryption provides a perennial solution to this quandary. The simplicity of managing a single key enables organizations to scale their encryption operations seamlessly. When compared to asymmetric encryption, where the proliferation of users necessitates the generation of numerous key pairs, symmetric encryption circumvents this issue and fosters a more manageable framework. However, as the number of users increases, so does the challenge of key management. Can you envision a labyrinth of keys, each required to encrypt and decrypt a myriad of communications?
4. High Security for Targeted Applications
Contrary to common misconceptions, symmetric key encryption can offer formidable security, particularly when the key remains secret and robust algorithms are deployed. It is particularly advantageous in scenarios where the risk of interception during transmission is minimal. Encrypted databases, file storage systems, and virtual private networks (VPNs) frequently utilize this form of encryption. Additionally, the rapid advancements in cryptographic techniques have continuously fortified symmetric encryption against new vectors of attack, turning it into a bastion of digital security in certain applications.
5. Reduced Latency
In a world dominated by instantaneous gratification, reduced latency is a coveted asset. Symmetric key encryption minimizes the latency that often plagues asymmetric methods. Asymmetric cryptography frequently requires a lengthy key exchange process that can engender delays, especially in environments with high data throughput. In contrast, symmetric encryption circumvents these delays by utilizing pre-shared keys, facilitating swift data exchanges. This characteristic is vital in sectors such as online gaming or real-time video streaming, where lag can spell disaster for user experience.
6. Versatility Across Platforms
Yet another remarkable characteristic of symmetric key encryption is its versatility. It can be employed across a multitude of platforms and devices, from personal computers to mobile devices and cloud services. This adaptability makes it a go-to solution for numerous applications across diverse industries. Organizations engaged in sensitive data management, such as healthcare or finance, can leverage symmetric encryption to maintain compliance with regulatory standards while ensuring robust data protection. This widespread applicability enhances its appeal, empowering businesses to adopt a unified encryption strategy.
7. Legacy Systems Compatibility
In many business ecosystems, legacy systems still play significant roles. Symmetric key encryption exhibits compatibility with these older infrastructures, providing a pathway to modernize security without necessitating a complete overhaul of existing systems. By integrating symmetric encryption, organizations can bolster their security posture while maintaining operational continuity. However, the underlying challenge persists: how do organizations effectively manage transitioning away from outdated systems while ensuring data integrity and confidentiality?
8. Facilitating Privacy in Communications
The ever-evolving landscape of digital communication underscores the necessity for privacy. Symmetric key encryption serves as a guardian of confidentiality, permitting individuals and organizations to communicate securely. Platforms such as WhatsApp and Signal employ symmetric encryption methods to ensure message confidentiality, thereby facilitating trust in digital communications. The near-instantaneous encryption and decryption processes allow conversations to occur in real-time without sacrificing security, turning the art of secure communication into a mundane reality.
Conclusion
In summary, symmetric key encryption emerges as a linchpin of modern cryptographic practices, offering advantages that reverberate across various sectors. Speed, resource efficiency, scalability, security, reduced latency, versatility, compatibility with legacy systems, and enhanced privacy are paramount features that render symmetric key encryption indispensable. However, the complexities of key management and potential challenges associated with security breaches must not be overlooked. As the digital landscape continues to evolve, how will organizations navigate the challenges that accompany these benefits? The balance between the allure of efficiency and the imperative of security remains an everlasting dance for cryptographers and businesses alike.








Leave a Comment