In the digital age, the necessity for robust security mechanisms is paramount. Public-key cryptography plays a crucial role in safeguarding sensitive information. Among the myriad of algorithms available, RSA, DSA, and ECC emerge as the preeminent contenders. Each has unique attributes, performance characteristics, and prospective applications, making the choice contingent upon specific use cases and requirements.
Understanding the Algorithms
RSA, or Rivest-Shamir-Adleman, epitomizes the pioneering spirit of public-key cryptography. Introduced in 1977, it leverages the mathematical properties of large prime numbers. RSA’s security primarily hinges on the computational difficulty of factoring the product of two large primes. The algorithm generates a public key for encryption and a private key for decryption, allowing secure exchanges over unsecured channels.
DSA, or Digital Signature Algorithm, was designed for digital signatures and is a component of the Digital Signature Standard (DSS). Unlike RSA, DSA utilizes a combination of modular exponentiation and finite field mathematics to produce signatures. Its security is anchored in the complexity of solving the discrete logarithm problem. DSA employs a signature verification process that enhances its efficacy in authentication, but it is not suitable for encryption.
On the other hand, ECC, or Elliptic Curve Cryptography, offers powerful advantages through its reliance on the algebraic structure of elliptic curves over finite fields. By utilizing smaller key sizes compared to RSA and DSA while achieving an equivalent level of security, ECC has garnered acclaim for its efficiency. This efficiency makes ECC particularly appealing for devices with constrained computational resources.
Comparative Analysis
When juxtaposing these three algorithms, several factors come into play, including security strength, performance, and resource utilization. The comparison invariably reveals trade-offs that organizations must navigate.
1. Security Strength
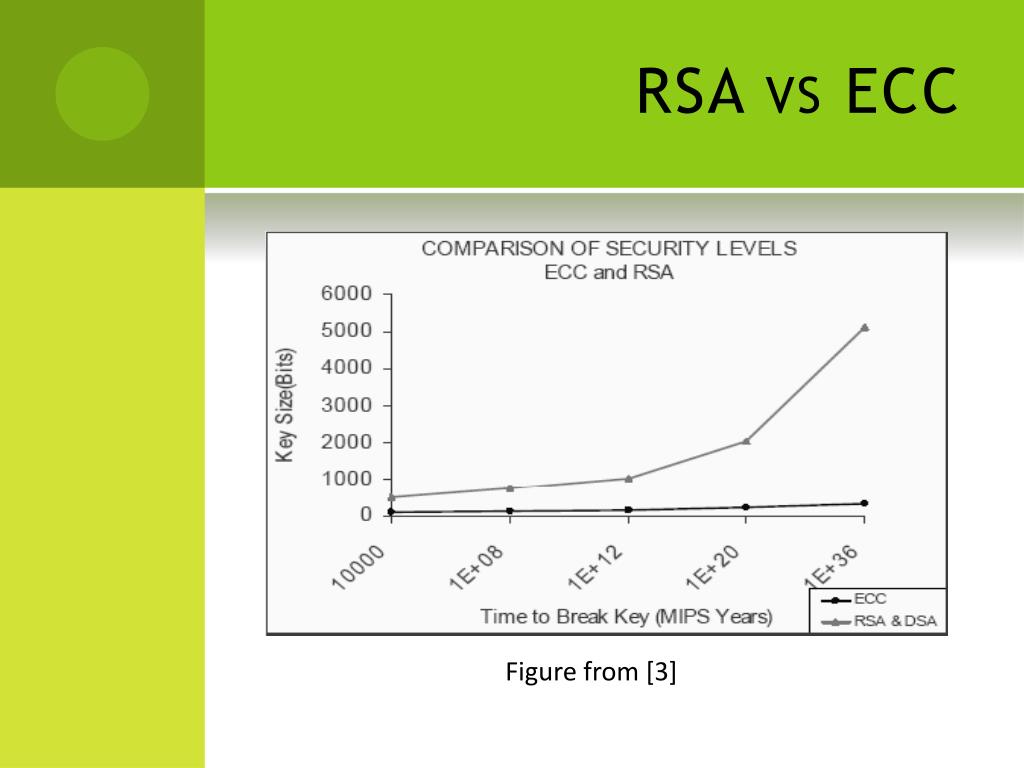
In terms of sheer security strength, ECC holds a notable advantage. For instance, a 256-bit key in ECC is purported to offer a security level comparable to a 3072-bit key in RSA. This discrepancy implies that ECC can deliver equivalent security with significantly reduced computational and bandwidth costs. However, RSA has been a stalwart for decades, and its established history in cryptography instills a level of confidence. Conversely, DSA’s security is often assessed relative to the key length. A minimum 2048-bit key is recommended for DSA to ensure robust security in modern applications.
2. Performance Efficiency
Performance is another critical metric. RSA possesses a reputation for being computationally intensive, particularly during the key generation phase. The encryption and decryption processes can be time-consuming, particularly as the key size escalates. In contrast, DSA is primarily efficient in signature generation and verification, yet it requires careful consideration regarding the randomness of the generated keys, which can affect its performance and security.
ECC, by virtue of its design, offers superior efficiency among the trio, necessitating smaller keys for similar security levels. This attribute renders ECC not only faster but also less demanding on system resources, making it ideal for mobile devices and Internet of Things (IoT) applications where performance and battery life are paramount.
3. Resource Utilization
The implications of resource utilization cannot be overlooked. RSA, while cryptographically sound, demands substantial computational resources for operations, increasing latency especially in constrained environments. ECC, with its lower overhead, excels in scenarios requiring rapid computations without compromising security. DSA also aims for efficiency, particularly in generating signatures, yet it entails a more significant resource footprint than ECC.
Use Cases and Applications
The choice of a public-key algorithm invariably influences the landscape of potential applications. RSA has been extensively utilized for securing communications over the internet, including SSL/TLS protocols. Its explosive popularity stems from its robust encryption capabilities and ease of implementation.
DSA, while less ubiquitous than RSA, finds its niche predominantly in digital signatures, especially in scenarios where authentication and message integrity are vital. Its incorporation in standards like the Digital Signature Standard illustrates its significance in legislative and organizational contexts that prioritize non-repudiation.
Conversely, ECC has gained traction in contemporary applications, especially in environments requiring heightened performance and security. With the increasing prominence of mobile devices and IoT, the necessity for lightweight cryptographic solutions is more pronounced. Cryptocurrencies, which require secure transactions with minimal overhead, have also embraced ECC for its efficacy.
Conclusion: Making the Choice
In conclusion, the debate surrounding RSA, DSA, and ECC must be contextual. Each algorithm possesses distinct strengths and weaknesses that cater to different operational needs. RSA’s decade-long legacy provides robustness in familiarity, while DSA offers efficiency within its specialized domain of digital signatures. ECC stands out for its modernity, efficiency, and suitability for constrained environments. Organizations must weigh their specific security needs, performance requirements, and resource limitations to arrive at an informed decision. Through careful consideration, the right public-key algorithm can bolster an organization’s commitment to digital security in an increasingly complex landscape.







Leave a Comment