Cryptography, the art of secure communication, has evolved remarkably over the millennia. Imagine, if you will, a world where secrets are exchanged in whispered tones and scrawled notes, a time long before the advent of digital technology. What is it about the age-old practice of encrypting messages that has retained its allure? This exploration beckons a curious inquiry: how did we traverse from the rudimentary Caesar cipher to the sophisticated SHA algorithms that encapsulate our modern digital communications? Join us on this historical journey through cryptography.
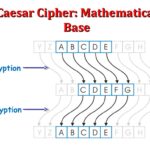
To begin with, let’s delve into the ancient roots of cryptography. The term “cipher” itself derives from the Arabic word “sifr,” which means zero. Historically, the foundations of cryptographic techniques can be traced back to the Roman Empire with the legendary Caesar cipher. Used by Julius Caesar to communicate with his generals, this simple substitution cipher shifts letters a predetermined number of spaces in the alphabet. The effectiveness of such a cipher lies not in its complexity but in its clever simplicity; an encrypted message can be deciphered by anyone who knows the shift. However, this also brings forth an intriguing challenge: how can one secure a message if the method of encryption is widely known? Even in antiquity, the delicate balance of security and accessibility was paramount.
As we venture deeper into the annals of history, we encounter the Middle Ages, a time marked by an increased complexity in cryptographic systems. During this period, various ciphers proliferated, including the Vigenère cipher—an ingenious method that employed a keyword to encipher text. The brilliance of the Vigenère cipher was its polyalphabetic nature, where the same letter could be represented by different symbols based on its position in the keyword. Yet, is it not ironic how such innovations also paved the way for more sophisticated decryption techniques? The age-old cat-and-mouse game of cryptography evolved, with cryptanalysts dedicated to decoding messages and cryptographers intent on fortifying their systems.
With the onset of the Renaissance came a transformative surge in interest surrounding cryptography. Manuscripts filled with cryptographic lore circulated among scholars and aspiring spies alike. The invention of printing allowed for the sharing of these innovations on an unprecedented scale. Consequently, the sheer volume of encoded messages prompted a renewed emphasis on creating robust encryption methods. The arrival of frequency analysis—a technique revealing the commonality of letters in a language—signified a paradigm shift in the ability to crack codes. As we ponder this progression, one cannot help but wonder how the rise of a single technique could simultaneously enhance both encryption and decryption capabilities.
The dawn of the 20th century heralded a new chapter in cryptographic history, propelled by the necessities of warfare. World War I and II ignited an arms race not only in battleships and weapons but also in codes and ciphers. Concomitantly, the Enigma machine emerged, a stunning mechanical device employed by the Germans for secure communications. The reliance on rotors and electrical circuits encapsulated a remarkable convergence of technology and cryptography. However, the vulnerability of the Enigma lay in the human element of its operation, and the astute efforts of Allied cryptanalysts, exemplified by Alan Turing, ultimately unlocked its secrets. Could this be indicative of a greater truth—that the most intricate systems often possess the most exploitable flaws?
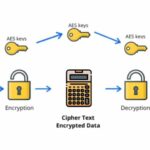
As we segued into the domain of the digital age, the landscape of cryptography transformed dramatically. The advent of computers necessitated the development of new encryption algorithms that could withstand the computational prowess of machines. The Data Encryption Standard (DES), established in the 1970s, became a staple for many years. What was initially deemed secure, however, soon fell prey to the relentless march of technology. The exponential increase in computing power revealed the inadequacies of DES, which, as time progressed, could be deciphered with relative ease. The call for more robust encryption gave birth to the Advanced Encryption Standard (AES), a versatile and powerful cipher still in use today.
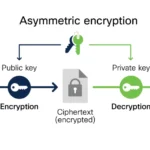
Parallel to symmetric-key encryption systems such as AES emerged public-key cryptography, a revolutionary concept that shifted the paradigm entirely. Introduced by Whitfield Diffie and Martin Hellman in 1976, this technique utilized two keys—one public and one private—to facilitate secure communications over insecure channels. The beauty of public-key cryptography lies in its exponential complexity; the cryptographic security it offered could be scaled in ways that were previously impossible. Yet, with these advancements arose an existential question: does the democratization of cryptographic tools inevitably lead to their exploitation for nefarious purposes?
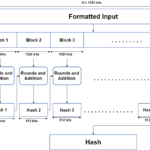
Fast forward to the present, and we find ourselves amidst a digital explosion characterized by heightened concerns over security and privacy. The Secure Hash Algorithm (SHA), a family of cryptographic hash functions, has become an integral part of contemporary cryptography. SHA-256, widely used in blockchain technology, exemplifies a shift toward ensuring data integrity in an ever-expanding information landscape. The hallmark of SHA lies in its one-way function: transforming input data into a fixed-size hash that appears random. This inherent unpredictability poses a formidable challenge for anyone attempting to reverse-engineer the original data. However, as we embrace the benefits of such algorithms, ethical quandaries emerge regarding privacy, data security, and surveillance.
As we conclude this historical odyssey, we recognize that cryptography is not merely a collection of techniques—it is a reflection of our evolving relationship with information, privacy, and security. The playful inquiry about our journey from the Caesar cipher to SHA illuminates not only the ingenuity of human beings but also the persistent challenges we face in balancing security with accessibility. Just as ancient scholars etched their secrets in ciphers, we navigate an increasingly complex digital realm fraught with vulnerabilities and ethical dilemmas. Indeed, as we traverse this cryptographic continuum, the promise of secure communication must also contend with the shadows of potential misuse in our interconnected world.





Leave a Comment