In the vast tapestry of digital communication, secrets flourish within the intricate labyrinth of cryptography. Imagine, if you will, a castle besieged by foes, with only the strongest of locks guarding its precious treasures. This is the essence of cryptographic algorithms, those formidable sentinels protecting the sanctity of information in a world laden with threats. As we embark on this exploration of modern cryptography, we unravel the secrets of its most prominent types, each with unique attributes and unparalleled significance.
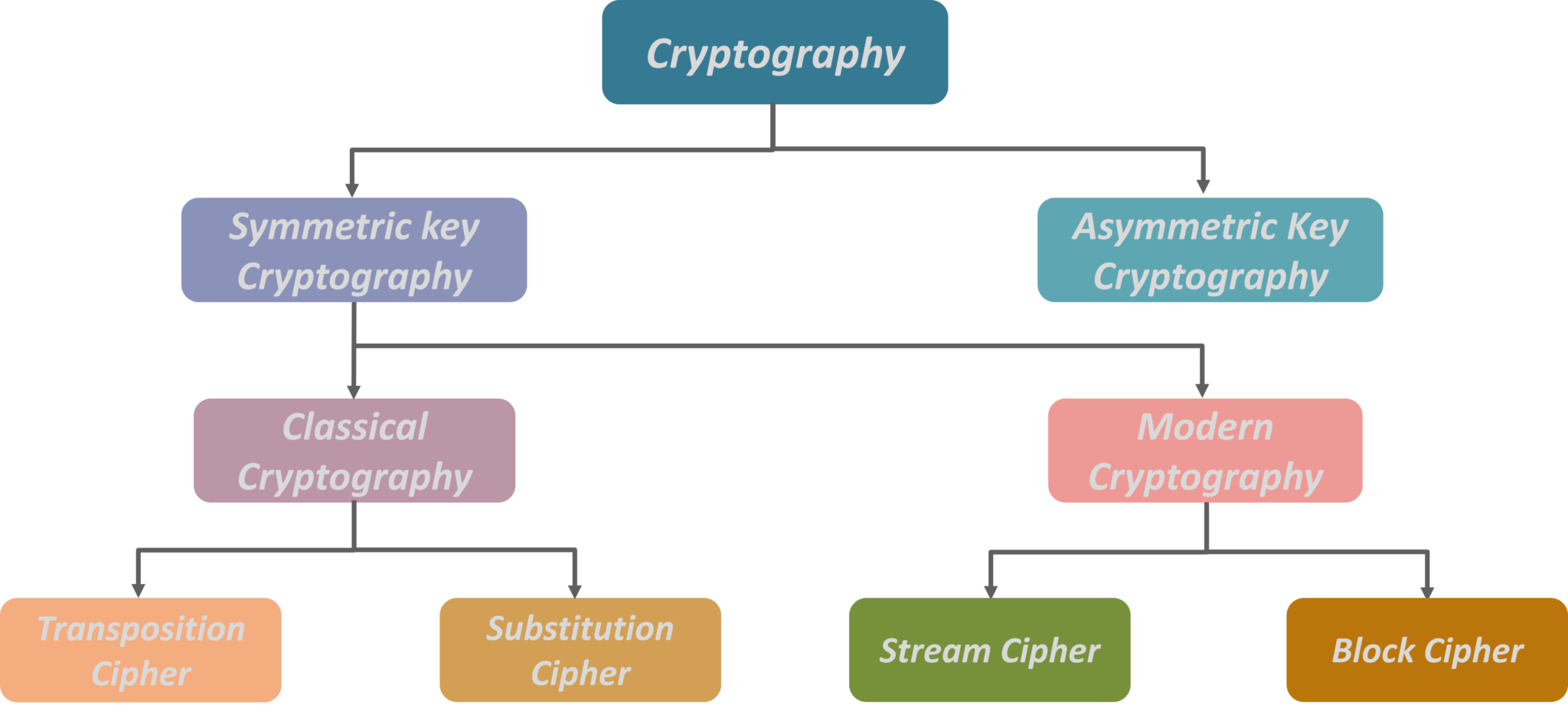
At the foundation of contemporary cryptographic practices lies symmetric-key cryptography, a method reminiscent of a shared secret between two confidants. In this paradigm, the same key is employed for both encryption and decryption. The strength of symmetric-key systems is encapsulated in their brevity and efficiency. However, with elegance comes vulnerability; if the key is intercepted during transmission, the entire citadel of data is laid bare. Prominent algorithms like Advanced Encryption Standard (AES) and Data Encryption Standard (DES) exhibit the powerful potential of symmetry, streamlining the encryption processes that underpin secure communications.
Delving deeper into the multidimensional world of cryptography, asymmetric-key cryptography emerges as a captivating enigma. Often likened to a highly secured mailbox, this method utilizes a pair of keys: one public and one private. The public key, akin to a mailbox visible to all, allows anyone to send encrypted messages, while the private key remains a closely guarded secret, enabling the owner to decrypt received communications. The allure of asymmetric cryptography stems from its ability to facilitate secure exchanges without the necessity of prior key sharing. Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC) stand as paragon examples, showcasing how complex mathematical constructs underpin these systems, ensuring the safety and integrity of modern communications.
Both symmetric and asymmetric cryptography possess their own merits, yet neither can exist in isolation. The symbiotic relationship between these two paradigms is highlighted in hybrid cryptography, a synthesis that harnesses the strengths of each. Imagine a sophisticated vault that employs traditional locks fortified by modern electronic security. Hybrid systems often use asymmetric cryptography to exchange a symmetric key securely. Once the key is established, symmetric methods take over for the actual data encryption, combining efficiency with robust security. This duality is vital in contemporary applications, from secure email transmission to the safeguarding of digital currencies.
The realm of cryptography is not merely confined to encryption and decryption processes. A significant component lies in hashing—akin to a unique fingerprint for data. Hashing transforms input data into fixed-length strings. Each morsel of information, whether a simple message or an extensive document, can be meticulously processed into a hash, which serves as a digital signature. The immutability of hashing ensures that even a minute alteration in the input will result in a radically different hash output. Secure Hash Algorithm (SHA), particularly SHA-256, has ascended as a prominent tool in this domain, underpinning various security protocols and serving as the backbone for blockchain technology.
As we traverse this digital landscape, attention must be paid to digital signatures, an application of asymmetric cryptography that transcends mere identity verification. These signatures are akin to a handwritten autograph on a contract, offering authenticity and integrity. When a person digitally signs a document using their private key, others can validate its authenticity with the corresponding public key. This process engenders trust in digital communications and transactions, making digital signatures indispensable in sectors ranging from legal documentation to software distribution.
In parallel with the evolution of cryptographic technologies is the rising tide of quantum computing, an impending paradigm shift that augurs potential challenges for traditional cryptographic systems. Quantum computers, equipped with unprecedented processing power, threaten the foundations of current encryption methodologies. Classical asymmetric algorithms like RSA could be rendered obsolete by quantum algorithms, particularly Shor’s Algorithm, capable of factoring large integers exponentially faster. The advent of this technology has prompted cryptographers to explore quantum-resistant algorithms, ensuring the longevity of secure communications in a post-quantum world.
In the canvas of modern cryptography, one cannot overlook the significance of key management and distribution—the custodians of cryptographic secrets. The very strength of any encryption technique hinges on the protection and distribution of cryptographic keys. Breaches often occur not due to flaws in the algorithms themselves, but through mismanagement of keys. Secure key management strategies, encompassing hardware security modules and robust access controls, play an indispensable role in defending against cryptographic vulnerabilities.
Furthermore, the convergence of cryptography with emerging technologies, such as blockchain and decentralized networks, amplifies its revolutionary essence. Blockchain, the cornerstone of cryptocurrencies like Bitcoin, relies on cryptographic principles to ensure the integrity and validation of transactions. As this technological marvel proliferates, cryptographic methodologies are duly adapted and integrated, forging paths to originality and ingenuity. The marriage of cryptography and blockchain embodies a new frontier, where trust is distributed, and transparency is paramount.
In essence, the exploration of modern cryptography unveils a world where secrets intertwine with security, and algorithms stand as vigilant guardians of information. From the steadfast foundations of symmetric and asymmetric encryption to the dexterous intricacies of hashing, digital signatures, and the looming specter of quantum computing, the narrative of cryptographic evolution is ongoing. As we decipher the layers of complexity, we derive an understanding that in this digital age, the allure of cryptography lies not just in its capacity to safeguard secrets but in its pivotal role in fostering trust—a quality as essential as the very data it aims to protect.







Leave a Comment