In the realm of modern digital communications, the idea of unbreakable cryptographic algorithms evokes a curious blend of fascination and skepticism. Cryptography, often referred to as the science of secret writing, has evolved tremendously over centuries, adapting to the intricate dance between security and the ever-developing capabilities of potential attackers. This exploration delves into the mythos surrounding truly unbreakable cryptographic algorithms—a discourse that intertwines mathematical ingenuity and pragmatic considerations.
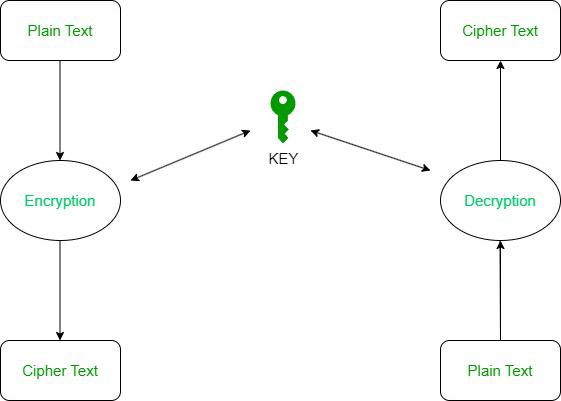
The concept of unbreakability begins with the classical notion of a cipher, a method by which a message is obscured to safeguard it from prying eyes. Historically significant ciphers, like the Caesar cipher or the Vigenère cipher, served their purposes well in eras devoid of complex computational threats. However, they fell prey to systematic analysis and brute-force attacks as cryptanalysis matured. The realization emerged that absolute security is a challenging, if not unattainable, ideal.
At the heart of the inquiry lies the one-time pad, a unique cipher that has frequently been touted as the epitome of unbreakable encryption. The one-time pad operates on a simple premise: if a random key, as long as the message itself, is used and never reused, the resultant ciphertext is theoretically immune to decryption without possession of the key. The mathematical underpinning of this assertion stems from the law of probability; each symbol in the plaintext message can be effectively transformed into any other symbol of equal length, making deciphering without the key an exercise in futility.
However, despite its fascinating theoretical framework, the practical implementation of the one-time pad encounters insurmountable challenges. The generation, distribution, and safeguarding of truly random keys on a scale that matches modern communication needs present formidable obstacles. Inevitably, the human element reintroduces flaws—mismanagement or reuse of keys can annihilate the promised security, casting doubt on the notion of its unbreakability.
Transitioning from the one-time pad to contemporary algorithms, we encounter a suite of cryptographic techniques that balance security and pragmatism. Symmetric cryptography, with algorithms such as AES (Advanced Encryption Standard), dominates the landscape. AES, with its robust key lengths of 128, 192, or 256 bits, maximizes complexity and renders brute-force attempts impracticable for all but the most determined adversaries. Nevertheless, the lifeblood of AES’s efficacy hinges on the strength of key management and the dynamism of computational advancements.
Further in this exploration, the realm of asymmetric cryptography introduces intriguing concepts as well. The RSA algorithm, named after Rivest, Shamir, and Adleman, operates on the principle of factoring large integers—an inherently complex mathematical problem. The security of RSA is predicated on the difficulty of this factorization, but embodies another layer of inquiry; as quantum computing ascends from theoretical obscurity into the limelight, RSA’s practicality faces existential threats. Quantum algorithms, specifically Shor’s algorithm, promise efficient factorization, thus undermining RSA’s essence of security and stretching the dialogue around what constitutes ‘unbreakable.’
This cascading chain of questioning brings to the forefront post-quantum cryptography, an emerging field dedicated to safeguarding against the advent of quantum-enabled decryption. Lattice-based cryptography, hash-based signatures, and other forms of asymmetric encryption are being assessed for their resilience against quantum attacks. Yet, the shift towards these untested paradigms ignites debate—can we consider them unbreakable merely because they resist currently known attack vectors? Or do we simply postpone the inevitable reckoning with the progression of computational power?
Unbreakability, then, transcends a simple binary classification. Instead, it morphs into a continuum influenced by mathematical complexity, key management, implementation practices, and even user behavior. The growing realization that complete security remains an elusive ideal invites a philosophical reconsideration of how we approach cryptography itself. While algorithms striving for fortification continue to arise, the interplay of human errors and technological changes creates a labyrinth of vulnerabilities.
Furthermore, the emergence of artificial intelligence and machine learning introduces additional variables that could radically alter the state of cryptanalysis. These sophisticated algorithms hold the potential to analyze vast datasets, perhaps unveiling weaknesses in encryption methodologies that have eluded traditional analysis. If superintelligent entities can be deployed to explore the labyrinths of cryptographic systems, can we still stake claims on unbreakability?
Ultimately, the question of whether there are cryptographic algorithms that are truly unbreakable takes on spectral dimensions as technology and society progress. The storytelling of cryptography is one of evolution—a constant dance fueled by ingenuity and pragmatism. It reflects a broader philosophical articulation of security that recognizes that while some algorithms may resist known attacks for now, they are inevitably entangled in a web of human choices and shifting technological landscapes.
In conclusion, the quest for unbreakable cryptographic algorithms beckons an acknowledgment of the complex interplay between possibility and reality. Rather than an ultimate destination, it invites ongoing inquiry—a continuous engagement with the challenges of securing information in an ever-evolving digital world. The assertion of unbreakability perhaps lies not in the algorithms themselves, but in our collective responsibility to continually question, innovate, and adapt within this intricate field of cryptography.







Leave a Comment