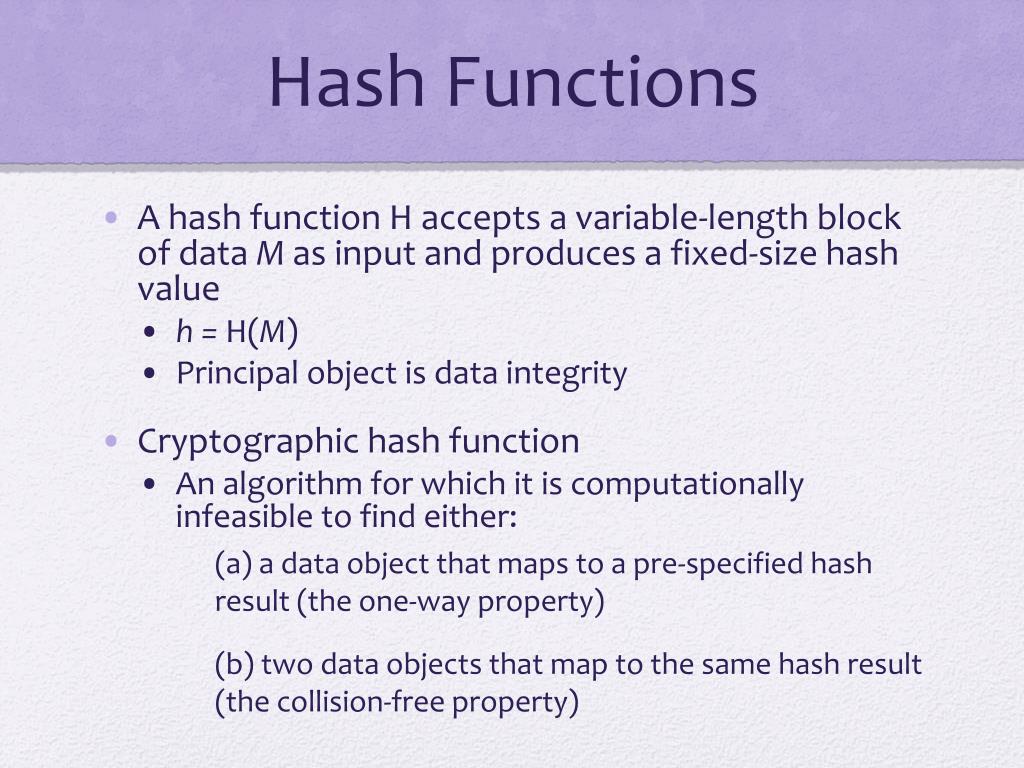
The profound significance of hash functions in cryptography cannot be overstated. Essential for securing data integrity and authenticity, these mathematical marvels play a pivotal role across various domains, from securing online transactions to password management. Crafting an effective hash function involves both technical acumen and an understanding of core cryptographic principles. Below is an extensive examination of best practices for designing a killer hash function.
1. Comprehend the Mathematical Foundation
To establish a robust hash function, one must begin with a firm grasp of the underlying mathematics. Familiarity with number theory, combinatorics, and probability theory is imperative. A thorough understanding of concepts like modular arithmetic and finite fields can significantly enhance the robustness of your hash function. These mathematical principles provide the agility needed to develop complex and collision-resistant algorithms.
2. Prioritize Collision Resistance
Collision resistance is a non-negotiable feature of any effective hash function. It ensures that two different inputs do not yield the same hash output. A well-designed hash algorithm should have a vast output space, significantly larger than the input space, making it computationally infeasible to find two distinct inputs that map to the same output. Utilizing longer hash sizes, such as 256 bits or more, can ameliorate the risk of collisions in the hash space, thus enhancing overall security.
3. Employ a Nonlinear Transformation
The intricacies of a hash function’s transformation process are integral to its security. Nonlinear transformations significantly complicate the relations between input and output, ensuring that even a minute alteration in input results in a drastically dissimilar output. Techniques such as mixing, diffusion, and confusion can provide the cryptographic strength needed to withstand pre-image attacks and second pre-image attacks.
4. Implement Iterative Hashing
Iterative hashing involves repetitively applying the hashing function to the input data. This method not only enhances the mixing properties of the hash but also makes it more resistant to structural analysis and attacks. Furthermore, using hash chaining can facilitate an even deeper level of complexity and security. Iterative approaches can harness the benefits of previous outputs, fortifying the integrity of the hashing process.
5. Maintain Uniform Distribution
A killer hash function must traverse the output space uniformly; an even distribution of outputs prevents predictable patterns. Non-uniform distributions can lead to clustering, providing attackers with potential vulnerabilities for exploitative strategies. Techniques such as stellar diffusion mechanisms help scatter hash outputs comprehensively, promoting resilience against statistical attacks.
6. Provide Sensitivity to Input Changes
In cryptographic applications, the hallmark of a strong hash function lies in its sensitivity to inputs. Even the slightest modification in the input should generate a completely different hash, leading to what is referred to as the avalanche effect. This property is critical for ensuring data integrity, especially in scenarios where any unintentional alteration could have severe repercussions.
7. Conduct Rigorous Testing and Validation
Before deploying any newly created hash function, it is essential to subject it to an exhaustive suite of tests. Rigorous validation ensures that the function’s security properties hold true under different attack vectors. Consider employing known cryptographic benchmarks and comparative analysis against established hash functions to evaluate performance, speed, and security. Peer reviews and cryptographic examinations from the community can lend credence to the efficacy of your design.
8. Stay Abreast of Current Research
The field of cryptography is in a constant state of evolution. Keeping abreast of the latest research, methodologies, and vulnerabilities exposed in existing hash functions is crucial. Engage with cryptography-focused communities, forums, and conferences to glean insights into potential pitfalls and enhancements. A proactive approach to knowledge acquisition can significantly bolster the resilience of your hash function.
9. Consider Future Scalability
When developing a hash function, contemplating future scalability is imperative. As technology advances and data environments become ever more complex, a hash function must be adaptable. Elements such as the ability to increase hash output size without degrading performance or incorporating additional security features can prove beneficial in navigating future challenges.
10. Leverage Existing Frameworks
While developing a hash function from the ground up can be an intellectually stimulating endeavor, leveraging existing frameworks often acts as a pragmatic choice. Renowned hash functions like SHA-512 or BLAKE2 have undergone extensive scrutiny and optimization. By building on these tried-and-true foundations, developers can redirect their focus toward innovating other aspects of their systems while ensuring the cryptographic integrity of their data.
Conclusion
In conclusion, designing a killer hash function requires a meticulous approach that harmonizes mathematical rigor with pragmatic security considerations. From ensuring collision resistance to maintaining output uniformity and engaging in rigorous testing, each aspect plays a crucial role in fortifying the hash function against potential vulnerabilities. By adhering to these best practices, cryptographers can craft hash functions that not only satisfy immediate security requirements but also stand the test of time in an ever-evolving digital landscape.







Leave a Comment