In a digital world inundated with information, the necessity for secure data transmission and storage has become imperative. Central to this security is the concept of cryptographic hashes and hash functions. These mathematical constructs play a pivotal role in ensuring data integrity, authenticity, and confidentiality. While often perceived as esoteric, their underlying principles resonate deeply within the realms of computer science and cybersecurity.
At its essence, a cryptographic hash function is a one-way mathematical algorithm that transforms input data of arbitrary length into a fixed-size string of characters, typically a sequence of numbers and letters. This fixed-size output, known as the hash value or hash code, exhibits a series of properties that are crucial for its utility in various applications.
The first and foremost characteristic of a cryptographic hash function is determinism. For any given input, the output will consistently produce the same hash value. This property aids significantly in data verification, as a user can compare the hash values before and after data transfer to ascertain that no alterations have occurred. An illustration of this determinism can be observed in the process of downloading files from the internet. Often, websites provide a hash value alongside the downloadable file. Users can compute the hash value of their downloaded file and confirm that it matches the originally provided hash, ensuring the file’s integrity.
Another quintessential property of cryptographic hash functions is collision resistance. A function is collision-resistant if it is computationally infeasible to find two distinct inputs that yield the same hash value. This characteristic is particularly vital in preventing malicious actors from substituting fraudulent data or creating counterfeit digital signatures. In the realm of cryptocurrencies, for example, the integrity of transactions hinges on the ability to maintain unique hash outputs, further emphasizing this property’s importance.
The third salient characteristic is pre-image resistance, which denotes the difficulty of reconstructing the original input data from its hash value. This “one-way” nature of cryptographic hashes ensures that even if an adversary gains access to the hash, extracting the original data remains impractical. This property is foundational in safeguarding sensitive information, such as passwords, which are often stored in hashed form. By hashing passwords rather than storing them in a retrievable format, organizations significantly mitigate the risks associated with data breaches.
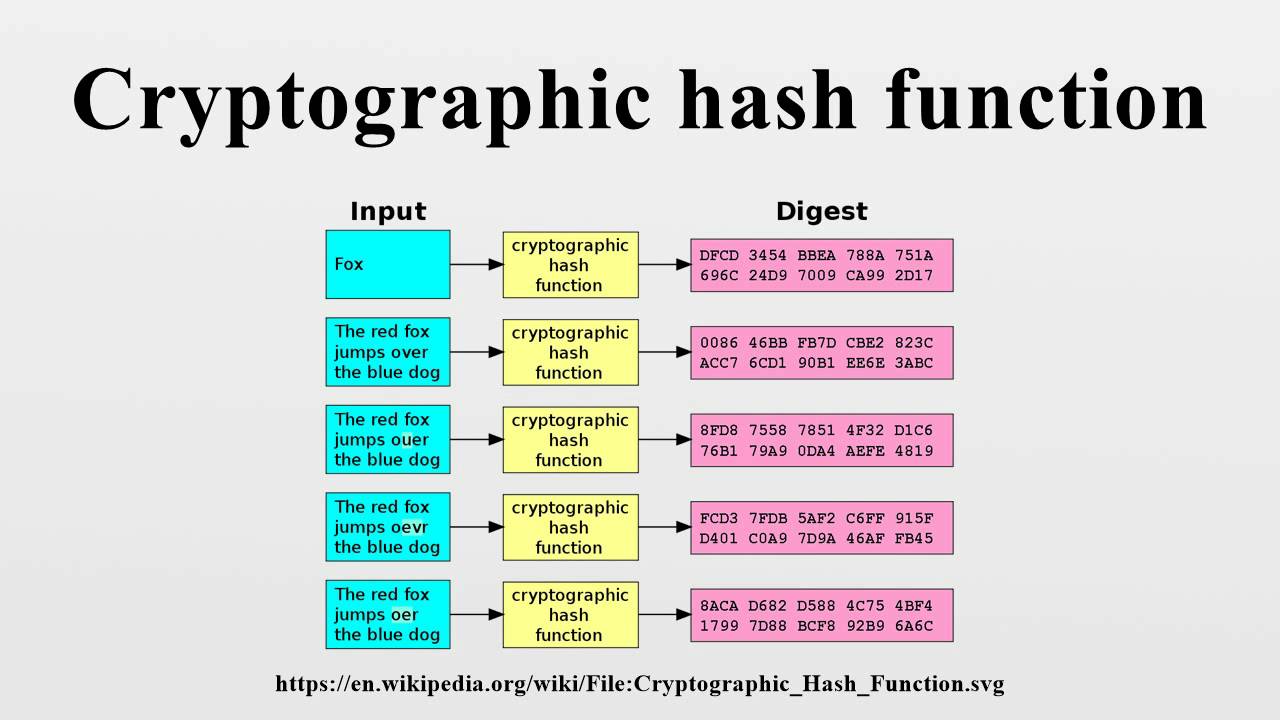
Intriguingly, even slight alterations in the input—be it a mere character change or an additional space—result in drastically different hash values. This phenomenon highlights the avalanche effect, another compelling attribute of cryptographic hash functions. It underscores the unpredictable nature of the output, ensuring that no discernible correlation exists between closely related inputs. This feature provides an additional layer of security, rendering hash functions particularly adept at thwarting cryptanalysis attempts.
Though the properties of cryptographic hash functions offer compelling advantages, it is crucial to recognize that not all hash functions are created equal. Some widely recognized hash functions include SHA-256, SHA-3, and MD5, each with distinct characteristics and varying degrees of security. For instance, while MD5 was once a popular choice due to its speed, it has since been deemed insecure due to vulnerabilities that facilitate collisions. On the other hand, SHA-256, part of the SHA-2 family, continues to be widely employed in blockchain technologies, representing a notable improvement in security and robustness.
The applications of cryptographic hash functions span a multitude of domains, encompassing digital signatures, data integrity verification, and password hashing. In digital signatures, these hashes serve as a unique representation of data, providing a means to authenticate the origin and ensure the integrity of a message. By signing the hash of the message rather than the message itself, the process becomes more efficient, while still retaining authenticity.
Moreover, in modern distributed ledger technologies, such as blockchain, cryptographic hashes are paramount. Transactions are hashed and linked in a chronological order, creating a permanent and immutable record. This mechanism not only ensures data integrity but also bolsters trust within a decentralized environment devoid of central authorities.
As technology evolves, so too does the fascination with cryptographic hash functions. Their intricate properties and applications not only safeguard our digital interactions but also act as a bulwark against the ever-evolving threats posed by cybercriminals. This duality—simplicity in concept yet complexity in execution—continues to captivate cryptographers and technophiles alike.
In conclusion, cryptographic hashes and hash functions embody a synthesis of mathematical rigor and practical application. Their determinism, collision resistance, pre-image resistance, and avalanche effect collectively forge an indispensable arsenal for securing digital information in an age where data breaches abound. Understanding these constructs not only elucidates their significance in contemporary cybersecurity practices but also highlights their critical role in fostering trust and integrity in our increasingly interconnected world. The study and application of cryptographic hashes remain an ever-evolving field, ensuring that the pursuit of security will continue to pique curiosity and drive innovation for years to come.








Leave a Comment