Encryption and decryption lie at the heart of modern digital communication, safeguarding sensitive data and ensuring privacy in an increasingly interconnected world. As a form of cryptography, these processes transform readable information into an obscured format and revert it back, respectively. This article delves into the intricacies of encryption and decryption, elucidating these concepts with clear examples to provide a comprehensive understanding.
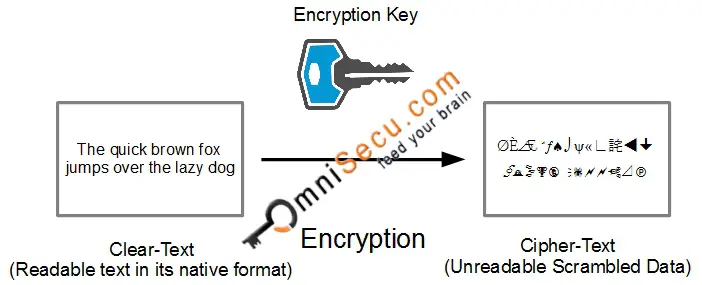
To begin with, it is crucial to grasp the basic definitions of encryption and decryption. Encryption is the process of converting plain text, which is easily readable and understandable, into cipher text, an unreadable format that conceals the original information. This transformation renders the data inaccessible to unauthorized eyes. Conversely, decryption is the process of reverting cipher text back to its original plain text form, making it intelligible once more. This reciprocal relationship between encryption and decryption ensures that only those equipped with the proper keys or credentials have the ability to decrypt the data.
One common observation regarding encryption is the pervasive need for data protection in our digital age. In an era dominated by technological advancement, where personal information is shared across various platforms, the potential for breaches and infiltration by malicious entities raises significant concerns. This demand for security fuels the fascination with cryptographic methods—a realm where mathematics and computer science intersect to create robust solutions.
There are various encryption techniques, but they can generally be categorized into two primary types: symmetric-key encryption and asymmetric-key encryption. Understanding these categories is vital for comprehending how encryption operates in different contexts.
Symmetric-Key Encryption
In symmetric-key encryption, the same key is used for both encryption and decryption. This implies that both the sender and recipient must possess the key and keep it confidential. One of the most prominent algorithms in this category is the Advanced Encryption Standard (AES), widely utilized for encrypting data across various applications.
To illustrate symmetric-key encryption, consider a scenario where Alice wishes to send a confidential message to Bob. Alice constructs a message, say “Meet me at noon,” and chooses a symmetric key—let’s say “12345.” Using this key, Alice employs the AES algorithm to encrypt her message, which transforms it into incomprehensible cipher text: “j8&$t1*X%.” She transmits this cipher text to Bob.
Upon receiving the cipher text, Bob utilizes the identical key “12345” to decrypt the message using the same AES algorithm. The decryption process converts the cipher text back into plain text, enabling Bob to read Alice’s original message effortlessly. The security of this form relies heavily on the secrecy and strength of the key; if an unauthorized user discovers the key, they can easily decrypt the message.
Asymmetric-Key Encryption
Asymmetric-key encryption, on the other hand, employs a pair of related keys: a public key and a private key. The public key is openly distributed, while the private key remains confidential to the owner. This technique is integral in establishing secure communications over the internet—the hallmark of secure websites (HTTPS) and email encryption.
For instance, consider the case of Alice and Bob again, but this time, Alice wants to send Bob an encrypted message without sharing a key in advance. Bob generates a key pair: a publicly accessible key and a privately retained key. He sends the public key to Alice, who then encrypts her message “Meet me at noon” using this public key, converting it into a cipher text that only Bob’s private key can decrypt.
Upon receiving the cipher text, Bob employs his private key to decrypt it. Because the encryption process was reliant on Bob’s public key, only the corresponding private key can make sense of the cipher text. This process ensures secure communication, allowing Alice to send confidential information without first exchanging keys.
One of the underlying reasons for the allure of encryption and decryption lies in their mathematical foundations. The remarkable complexity inherent in algorithms that underpin encryption processes draws mathematicians and cryptographers alike. Techniques such as prime factorization, modular arithmetic, and elliptic curve cryptography contribute to the strength of these methods, creating a fascinating web of numbers that serve as armor for our data.
Moreover, the implications of these cryptographic processes extend beyond individual privacy. In a broader context, they play a pivotal role in the security of national governments, financial institutions, and corporations. The safeguarding of sensitive information—ranging from personal identities to trade secrets—uses encryption as a bulwark against espionage and cyber threats. This domain’s impact resonates widely, establishing encryption as a cornerstone of our digital infrastructure.
In conclusion, a thorough understanding of encryption and decryption reveals their fundamental role in contemporary communication and information security. Through symmetric and asymmetric techniques, these processes facilitate confidential exchanges that are critical in a world increasingly reliant on technological advancement. As individuals and institutions commit to safeguarding their information, the art and science of encryption continue to evolve, highlighting the intricate relationship between mathematics, technology, and security in the modern era.








Leave a Comment