In the ever-evolving landscape of digital security, the question of whether symmetric or asymmetric encryption offers superior protection remains a tantalizing conundrum. As cyber threats grow more sophisticated, a playful inquiry arises—if both symmetric and asymmetric encryption are designed to safeguard our data, can one be deemed more secure than the other? To address this question thoroughly, we must critically analyze the strengths and vulnerabilities inherent in each encryption method.
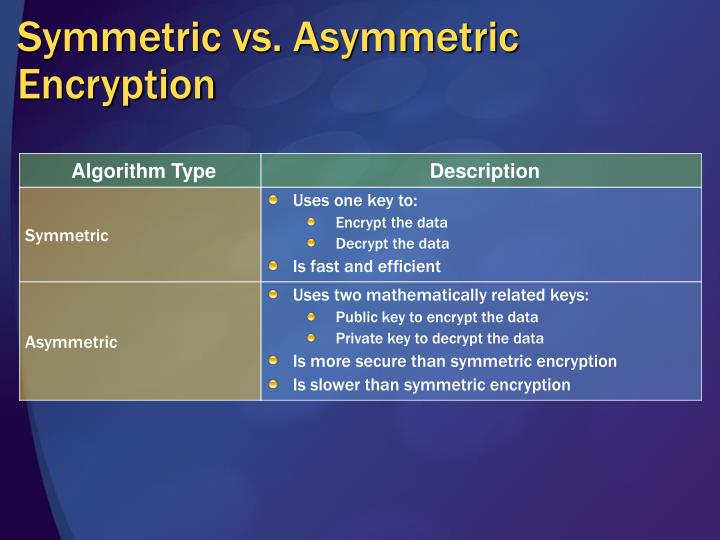
Symmetric encryption utilizes a single key for both encryption and decryption. This method is characterized by its speed and efficiency, making it well-suited for encrypting large volumes of data. However, the security of symmetric encryption hinges on the secrecy of the key used. If an adversary gains access to this key, they can easily decrypt the information. The crux of the challenge is the secure transmission of the key itself. If the key is intercepted during its transfer, all subsequent encryptions become compromised.
As we delve deeper into the advantages of symmetric encryption, it is essential to highlight its operational efficiency. Algorithms like AES (Advanced Encryption Standard) are not only fast but also capable of providing a robust level of encryption. This efficiency renders symmetric encryption favorable in environments where speed is paramount, such as real-time communications or when processing enormous datasets. Yet, these advantages come at a cost—namely, the difficulty of key management in a large organization where many users may require access to the same encrypted data.
Conversely, asymmetric encryption introduces a layer of complexity that addresses key distribution problems inherent in symmetric encryption. It employs a pair of keys: a public key for encryption and a private key for decryption. This dual-key mechanism allows anyone to encrypt data using the public key, but only the holder of the private key can decrypt it. The allure of asymmetric encryption lies in its ability to facilitate secure communication without necessitating the exchange of secret keys. However, this method typically suffers from slower processing speeds, partly due to the computational intensity of the algorithms used.
Now, one might ponder which approach ultimately provides a stronger security posture. The answer is not as straightforward as one might expect. While asymmetric encryption cleverly mitigates some of the vulnerability associated with key management, it is not devoid of pitfalls. Issues such as key exposure and reliance on the strength of the public/private key pair become paramount considerations. If a private key becomes compromised, the entire system’s integrity is called into question. In paradise lost, the allure of asymmetric encryption could quickly devolve into chaos if mishandled or poorly implemented.
Moreover, both encryption types face common threats that can undermine their effectiveness. For instance, a cryptographic algorithm must be robust against various attack vectors, including brute force attacks, replay attacks, and man-in-the-middle assaults. Advanced cryptographic techniques, combined with prudent implementation practices, are necessary in both cases. A less secure algorithm can render even the best key management systems ineffective, magnifying the vulnerabilities experienced across both encryption paradigms.
When examining resilience against contemporary cyber threats, it becomes clear that neither method can claim an unequivocal advantage. Instead, a layered approach often emerges as the most prudent strategy. Utilizing both symmetric and asymmetric encryption in tandem optimizes the strengths of each while minimizing their respective weaknesses. For instance, one could employ asymmetric encryption to securely exchange symmetric keys, which could then be used for subsequent rapid encryption of larger datasets. This synergy exemplifies a holistic view of encryption strategy, emphasizing the importance of context and scenario over simplistic labels of security superiority.
In addition, it is also vital to consider real-world applications of each encryption methodology. Symmetric encryption is frequently utilized in file encryption, VPN connections, and data-at-rest security, where the speed is essential. Meanwhile, asymmetric encryption is popular in secure email communications and digital signatures, where authentication is pivotal. Each serves a distinct purpose, underscoring the significance of understanding the context in which they operate.
Ultimately, the discourse surrounding whether symmetric or asymmetric encryption is more secure leads us to a more profound realization. The effectiveness of an encryption mechanism does not solely rest on its inherent characteristics but rather on the implementation and context of its application. Adopting both methods can yield optimal results, fortifying security infrastructures and resulting in robust defenses against an array of cyber threats.
In summation, rather than framing the discussion in binary terms—symmetric versus asymmetric encryption—one might consider a more integrative approach. How can we harness the strengths of both methods to construct a formidable barrier against cybercriminal activity? The answer may lie not in selecting one over the other but in employing their collective might to create a secure digital environment.







Leave a Comment