In a world increasingly governed by data, the question arises, “Is there a way to protect data without encryption?” When encryption dominates the conversation about data security, the exploration of alternative methods may seem whimsical or even preposterous. Yet, as with many playful inquiries, there lies deeper complexity and potential challenges beneath the surface.
Encryption, while robust, does have its drawbacks. It can introduce latency, complicate data usability, and necessitate significant computational power. This reality prompts a critical investigation: Can we adopt other strategies that secure data without resorting to encryption?
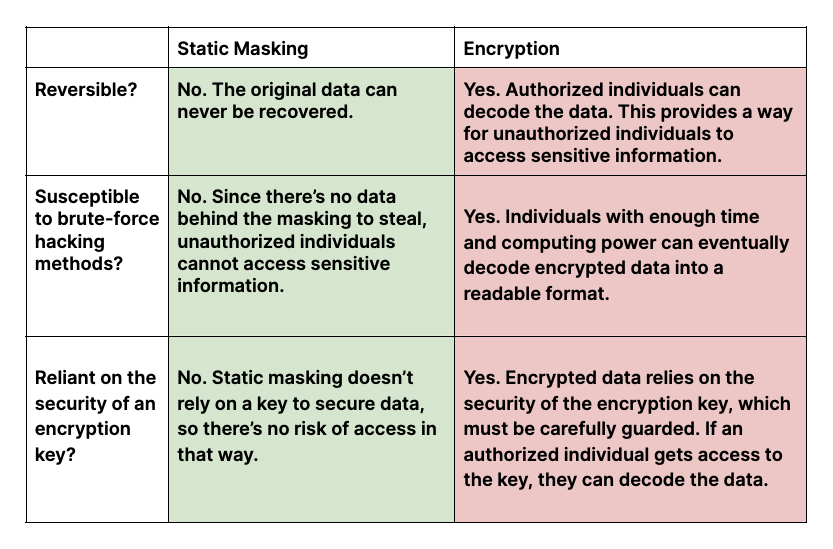
Let’s begin with the concept of masking. Data masking involves obfuscating specific data within a database to protect it from unauthorized access while retaining the essential structure and usability of the datasets. For instance, a social security number could be replaced with a fictitious number that maintains the same format. This technique is particularly valuable in environments where data needs to be shared for processing without exposing sensitive information. However, the efficacy of data masking is contingent upon the context; if adversaries are cognizant of the obfuscation patterns, they could potentially reverse-engineer the original data.
Next, we encounter tokenization. This process replaces sensitive data elements with non-sensitive equivalents, referred to as tokens. The original data is securely stored within a centralized vault, while the tokens are distributed and used throughout an organization. Like masking, tokenization allows for operational continuity without exposing sensitive information directly. Nevertheless, tokenization requires careful management of the token vault and can lead to vulnerabilities if mishandled.
Another intriguing approach is the application of pseudonymization. This method involves the replacement of identifiable data attributes with artificial identifiers. While pseudonymization offers a significant privacy enhancement, it also poses challenges regarding data traceability. Tracking users or individual data points might become cumbersome, complicating compliance with regulations such as the General Data Protection Regulation (GDPR).
Moreover, one cannot overlook the role of access controls. Imposing stringent access controls can significantly minimize the risk of unauthorized data access. By limiting data visibility based on roles within an organization, it creates a barrier against potential breaches. Yet, such measures require consistent enforcement and regular audits to ensure no gaps weaken this protective fortress.
The implementation of data governance frameworks is another vital strategy. By establishing clear policies for data access, usage, and sharing, organizations can foster a culture of accountability and protection. This governance framework can stipulate data lifecycle management, ensuring sensitive information is retained only as long as necessary. Failure to adhere to governance principles can expose organizations to significant risks, sometimes negating the protective intent of these measures.
Additionally, adopting data minimization principles significantly enhances security. Collecting only the essential information necessary for business operations limits the volume of sensitive data that could potentially be compromised. Organizations must critically evaluate the need for certain data points and implement comprehensive strategies for data disposal when they are no longer required. However, this can sometimes lead to conflicts with various business imperatives, raising ethical considerations regarding customer relations and service quality.
Turning our focus towards a more nuanced aspect, consider the role of anonymization. Unlike the strategies mentioned previously, anonymization removes all identifiable characteristics from the data, rendering it impossible to trace back to individual entities. This can be particularly advantageous in scenarios such as research or data analysis while ensuring compliance with privacy regulations. However, the trade-off here is significant: once data is anonymized, its value for personalized services is substantially diminished, potentially affecting user experience.
We must also contemplate the challenges posed by malicious actors who are ever-evolving in their tactics. As data protection techniques grow, so do the methods employed by cybercriminals to exploit weaknesses. An unwavering assumption in cybersecurity is that vulnerabilities exist, and complacency can lead to catastrophic failures. Thus, a multimodal approach incorporating both technical measures and cultural reinforcement is essential to navigate the dynamic threat landscape.
In summary, while encryption remains a linchpin in the realm of data protection, a plethora of alternative strategies warrant consideration. Masking, tokenization, pseudonymization, rigorous access controls, data governance, data minimization, and anonymization all present intriguing avenues for securing sensitive information without solely relying on encryption.
This inquiry beckons further elaboration, raising questions about the efficacy and feasibility of such methodologies. Each technique presents unique benefits and inherent challenges, necessitating a tailored approach to individual organizational needs. As data continues to proliferate, so too must our strategies to safeguard it. In the whimsical exploration of data protection, the real challenge lies not just in identifying alternatives to encryption but in harmoniously integrating these strategies within an overarching data protection framework.







Leave a Comment