In the realm of cryptography, the concept of digital signatures often evokes an array of inquiries and misconceptions. One such question that arises frequently is whether a private key signature is merely an encrypted message. To delve into this inquiry, it is essential to dissect the fundamental components of digital signatures, understand the role of private keys, and clarify the distinctions between encryption and signing mechanisms.
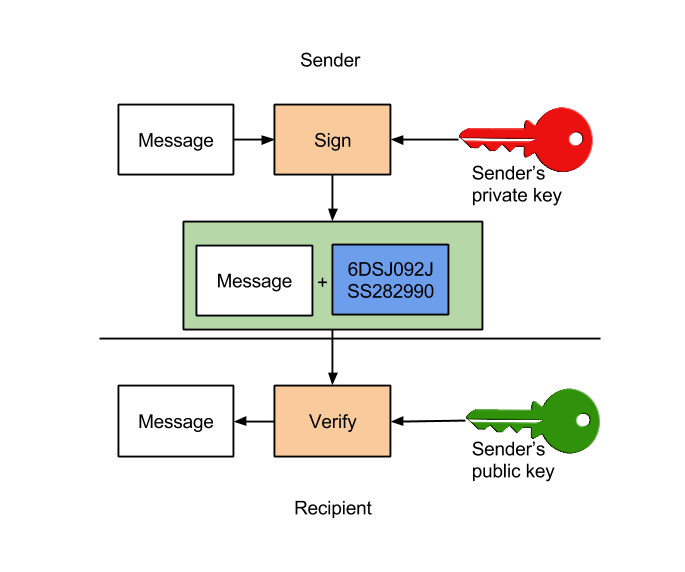
At its core, a digital signature serves as a cryptographic assurance of authenticity and integrity. Unlike a simple encryption process, whereby data is transformed into an unreadable format to preserve confidentiality, signing a message with a private key entails verifying that a specific entity authorized its contents. When a sender creates a digital signature, they first generate a unique hash (or digest) of the message. This hash represents a fixed-length string derived from the original data and is extremely sensitive to alterations. Even the slightest change in the message will yield a distinctly different hash.
The hash function utilized in this process typically adheres to established algorithms, such as SHA-256, which produce the hash in a way that is infeasible to reverse. Once the hash is computed, it is then encrypted using the sender’s private key. The subsequent product is what we term a digital signature. Thus, we should immediately recognize a pivotal distinction: while the signature does involve encryption, it is not an encrypted message in the traditional sense.
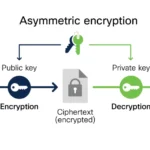
To comprehend the nuance further, one must consider the function of encryption. Encryption serves a singular purpose: to obfuscate data from unauthorized viewers. It guarantees confidentiality, ensuring that only individuals possessing the requisite decryption keys can access the plaintext information. In stark contrast, the goal of a digital signature is not to conceal information but to affirm its originality and authenticity. While a signature employs encryption, it operates under a different paradigm: it aims to verify that a message indeed originated from its purported sender and that it has not been tampered with.
In this light, the private key signature serves a dual function—while it cleverly incorporates an encrypted digest, it is primarily a means of validating the authenticity of the data. When a recipient receives a signed message, they can utilize the sender’s public key to decrypt the signature back into the hash. They then compare this hash with a freshly computed hash of the incoming message. If both hashes match, trust is established—the message remains intact, and the sender is validated. This fascinating interplay exemplifies how cryptographic algorithms can create confidence in an otherwise untrustworthy environment.
Moreover, digital signatures find their applications in a multitude of contexts—ranging from secure email communication to software distribution and blockchain technology. They act as the backbone of online security protocols, facilitating transactions that users often take for granted. Yet, the understanding of how they function, particularly in discerning the role of private keys, remains crucial for any stakeholder engaged in digital interactions.
Consider this: if a mere encrypted message was tantamount to a private key signature, we would not require differing pairs of keys for encryption and signing. Symmetric encryption uses the same key for both encrypting and decrypting, contrasting with the asymmetric paradigm employed by digital signatures, wherein the private key is used for signing and the public key for verification. This asymmetry lays the groundwork for a more robust security model, allowing individuals to share a public key widely while safeguarding the private key’s secrecy.
It emerges that perceiving a private key signature simply as an encrypted message undermines the intricacies of cryptographic principles. The signature encapsulates significant technical details and security assurances that transcend the straightforward act of encryption. This realization may shift perspectives, transforming how one navigates digital communications and appreciates the sophistication underlying the technologies utilized.
Furthermore, exploring the implications of this discernment is truly captivating. As cyber threats escalate, understanding the implications of digital signatures becomes imperative. By grasping their true nature—not as mere encrypted messages but as sophisticated validators of authenticity—individuals can better safeguard their digital identities and transactions. This paradigm shift may provoke curiosity about other cryptographic mechanisms, inspiring further inquiries into how these principles apply across the broad spectrum of technology and cybersecurity.
In conclusion, the assertion that a private key signature is merely an encrypted message misses the intricacies embedded within the fabric of cryptographic integrity. The interplay between hashing, signing, and the unique structure of asymmetric encryption portrays a complex landscape where assurance supersedes mere confidentiality. As we traverse the digital terrain, it is essential to adopt a nuanced understanding of these cryptographic mechanisms, not only to enhance personal security but also to advance the collective knowledge of best practices in digital communications.
Ultimately, it is in this venture of exploration that we cultivate an enriched comprehension of the digital domain. The revelation that a digital signature is not just an encrypted message but a sophisticated mechanism for affirming trust can reshape our engagements within the digital world. Curiosity ignites innovation, and an astute grasp of cryptographic functionalities will undoubtedly fortify the architecture of our cyber future.




Leave a Comment