In the realm of cybersecurity, two pivotal concepts often converge: hashing and encryption. While at first glance they may appear to serve similar purposes, a deeper examination reveals significant divergences in functionality, application, and underlying principles. This analysis seeks to clarify the distinctions between hashing and encryption, thereby dispelling the misconception that hashing is merely another form of encryption.
Understanding Hashing
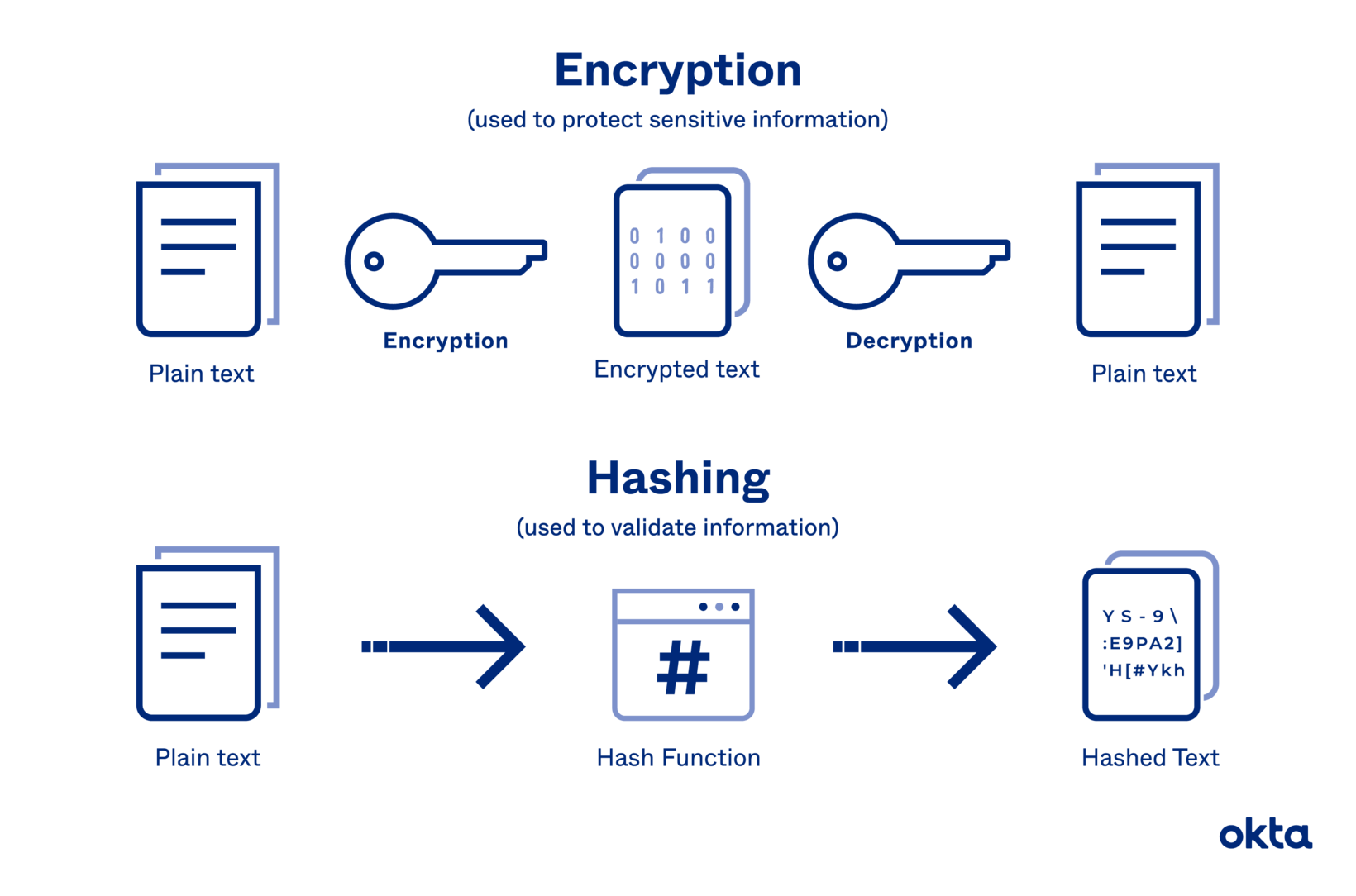
Hashing is a process employed to transform input data (known as a message) into a fixed-size string of characters, which is typically a sequence of digits and letters. This transformation is achieved through a hash function, a mathematical algorithm that processes the original data and returns a hash value or hash code. Importantly, hashing is a one-way operation: once the data has been converted into a hash, it is computationally infeasible to revert that hash back to its original data state. Furthermore, even the slightest change in the input produces a significantly different hash output, highlighting the sensitivity and uniqueness of hash functions.
Common applications of hashing involve maintaining data integrity and ensuring secure password storage. In modern applications, passwords are often hashed and stored in databases to protect against unauthorized access: unless one has the original password, it is virtually impossible to derive it from the hashed value. As a consequence, even in cases of data breaches, hashed passwords are rendered useless to attackers without the knowledge of the original input.
The Nature of Encryption
In stark contrast, encryption serves as a method of securing data by converting it into a format that can only be read by someone possessing the appropriate decryption key. Unlike hashing, encryption is a reversible process: the original data can be restored if one has access to the requisite keys. There are two primary types of encryption methods: symmetric and asymmetric.
Symmetric encryption employs a single key for both encoding and decoding the data, necessitating that both the sender and recipient possess the key. Examples of symmetric encryption algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES). Conversely, asymmetric encryption uses two distinct keys: a public key, which is shared freely, and a private key, which remains confidential. This method is exemplified by RSA (Rivest-Shamir-Adleman), where data encrypted with the public key can only be decrypted using the corresponding private key.
Comparative Analysis: Hashing vs. Encryption
One of the paramount differences between hashing and encryption lies in their primary objectives. Hashing is fundamentally concerned with verifying data integrity and authenticity. Its primary use case is not to conceal data but rather to ensure that it remains unchanged during transmission or storage. When data integrity is verified through hashing, one can detect alterations, whether intentional or due to corruption.
Conversely, encryption’s primary aim is confidentiality. In environments where sensitive information is exchanged, encryption ensures that eavesdroppers cannot decipher the data being transmitted. The goal is to shield proprietary or personal information from unintended access, thereby fostering a sense of security that a mere hash would fail to provide.
Another significant divergence is the way these processes handle data: a hash produces a fixed-length output, while encryption typically generates a variable output based on the length of the original data. This fixed output in hashing makes it compact and efficient for storage and lookup operations, which is particularly relevant when managing large datasets. However, the fixed nature of hashes introduces potential vulnerabilities; attackers can leverage techniques such as collision attacks, where two disparate inputs produce the same hash output.
Use Cases and Scenarios
The practical applications of hashing and encryption illustrate their unique roles. Hashing is routinely employed in digital signatures and software distribution. When a developer releases software, users can verify its integrity by comparing the hash of the downloaded file with the provided hash on the developer’s website. This verification process assures the users that the software has not been tampered with and is authentic.
Encryption, however, finds its utility in protecting personal communications or financial transactions. For instance, when transferring funds online, sensitive bank information is encrypted to safeguard against interception. In this way, both hashing and encryption contribute to the broader landscape of cybersecurity but fulfill distinctly different roles.
Conclusion
In conclusion, while both hashing and encryption are integral to modern security paradigms, they are not interchangeable nor is one simply a subset of the other. Hashing acts as a guardian of integrity, providing a way to ascertain that data has not been altered. Encryption, on the other hand, acts as a protective barrier, ensuring that unauthorized entities cannot access confidential data. Understanding these differences equips individuals and organizations with the knowledge necessary to implement appropriate security measures tailored to their specific needs. As the digital age continues to evolve, the importance of these two concepts remains paramount in safeguarding information integrity and confidentiality.







Leave a Comment