In the vast narrative of internet security, the acronyms SSL (Secure Socket Layer) and TLS (Transport Layer Security) often emerge as stalwart champions of data integrity and confidentiality. Yet, a common misconception persists regarding the operational position of these protocols within the layered architecture of network communications. Many may instinctively connect SSL/TLS with the application layer, anticipating that these protective mechanisms exist at the threshold where user applications interact with network protocols. However, the truth lies deeper—both SSL and TLS primarily function at the transport layer. This revelation invites a shift in perspective, positioning SSL/TLS within a framework that is both profound and essential.
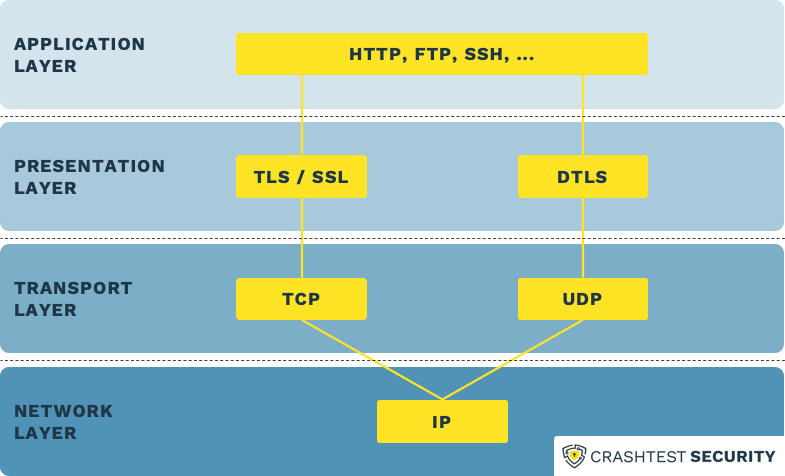
To fully appreciate the significance of SSL/TLS’s transport layer functionality, one must first grasp the layered model of the internet, particularly the OSI (Open Systems Interconnection) model, which consists of seven layers. These layers range from the physical layer, responsible for transmitting raw data bits over a physical medium, to the application layer, where end-user software operates. Each layer serves a distinct purpose, facilitating communication through defined protocols. Within this structure, the transport layer emerges as a critical juncture that delineates where end-to-end communication occurs, setting the stage for secure transmission.
The transport layer primarily manages the protocols that facilitate the transfer of data between two entities. Prominent protocols operating at this level include TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). SSL/TLS rides on the delicate shoulders of TCP, enhancing its capabilities by providing a secure channel for data transmission. Applying a layer of cryptographic protocols, SSL/TLS encapsulates application data within a secure framework, ensuring the confidentiality and integrity of information exchanged between web browsers and servers.
When one digresses into the intricacies of SSL/TLS, it becomes evident that the architecture of these protocols transcends simplistic functionalities. The initiation of a connection using SSL/TLS involves a series of exchanges collectively known as the “handshake.” During this handshake, key agreement and certificate verification take place, paving the way for symmetric encryption that will safeguard the data stream. This carefully choreographed sequence operates transparently between layers, illustrating the profound influence the transport layer wields within the wider context of internet security.
In pushing back against the notion that SSL/TLS resides solely within the application layer, one must consider the nature of encryption itself. Encryption fortifies data from interception, enabling secure transactions across potentially perilous channels. The operation of SSL/TLS within the transport layer not only emphasizes its role in securing data but also necessitates an understanding of the vulnerabilities inherent within the transmission medium. By operating at this foundational layer, SSL/TLS addresses threats such as man-in-the-middle attacks, injecting an essential level of resilience into the oft-vulnerable domain of internet communications.
Deconstructing the relationship between SSL/TLS and the transport layer suggests that the mere presence of these protocols does not guarantee security. The efficacy of SSL/TLS depends heavily on correct implementation, certificate validation, and adherence to best practices. Neglecting any of these components can expose data to malevolent actors. Therefore, a thorough understanding of SSL/TLS operations is imperative for both developers and users alike, merging technical proficiency with an acute awareness of security implications.
Now, consider the evolution of SSL/TLS, born out of necessity in a burgeoning digital landscape rife with insecurity. SSL was developed in the mid-1990s, poised to address early internet vulnerabilities. Over the years, TLS succeeded SSL, incorporating robust improvements, including support for stronger cryptographic algorithms and enhancements in performance and security. Awareness of this evolutionary timeline prompts curiosity about how SSL/TLS adapt to emerging threats and the inexorable march toward a more secure internet.
In examining the layered architecture of network communications, it becomes evident that the train of thought surrounding SSL/TLS must embrace a broader perspective. If one assumes that these protocols merely exist between end-user applications and the transport medium, one may inadvertently undermine their critical role in securing the communication highway. The implications are staggering: SSL/TLS acts as both conductor and shield, orchestrating the flow of data while defending against intrusions.
It’s crucial to underscore that security in the digital realm is a multifaceted challenge. While SSL/TLS plays an instrumental role, it is only one puzzle piece in a larger picture that includes firewalls, intrusion detection systems, and user education. Cybersecurity is an ongoing process, requiring vigilance and adaptability in response to ever-evolving threats. Recognizing the transport layer as the operating ground for SSL/TLS invites a more adept understanding of how to integrate these security measures effectively.
In summary, the location of SSL/TLS within the transport layer is not merely a location but a strategic positioning that underscores its functionality in the broader tapestry of internet security. Understanding this placement ignites curiosity and invites further exploration into the myriad ways in which data integrity and confidentiality can be upheld. As we navigate an increasingly interconnected world, embracing this nuanced understanding of SSL/TLS will undoubtedly empower individuals and organizations to foster stronger, more resilient networks.








Leave a Comment