The National Institute of Standards and Technology (NIST) Cybersecurity Framework is a comprehensive set of guidelines and practices designed to improve the security of organizations across various sectors. Formulated in response to the increasing incidence of cyberattacks, this framework is not only a tactical response to a pressing issue but also a holistic approach that reflects a deeper understanding of the complexities inherent in cybersecurity.
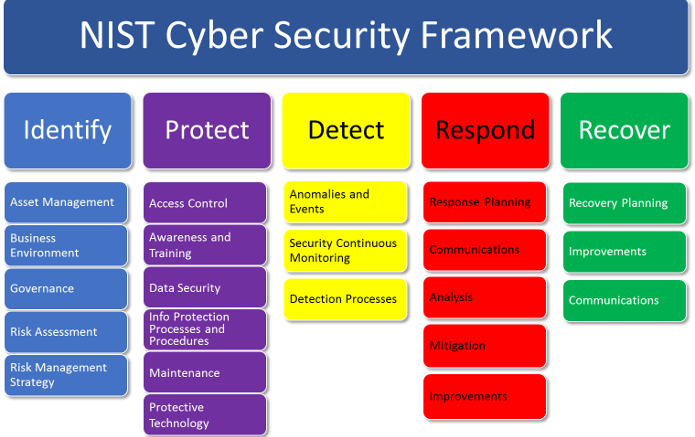
At its core, the NIST framework is structured around five key functions: Identify, Protect, Detect, Respond, and Recover. Each of these functions serves as a pillar supporting organizations in their quest for enhanced cybersecurity. The beauty of this framework lies in its adaptability; it can accommodate organizations of all sizes and maturity levels, from small enterprises to large corporations.
Firstly, the Identify function involves the comprehension of an organization’s environment, enabling it to manage cybersecurity risks effectively. This entails understanding not only the assets that need protection but also the potential threats and vulnerabilities that could exploit weaknesses. Organizations must catalog information systems, software, and data to develop a robust risk management framework. It is here that the significance of asset classification becomes apparent. An organization must discern which assets are integral to its operations and warrant the highest level of protection.
Transitioning into the Protect function, this segment addresses the veritable fortifications an organization can erect against potential threats. Protection strategies encompass a myriad of activities, including implementing access controls, maintaining protective technologies, and conducting security awareness training among employees. These measures collectively forge a bulwark against unauthorized access and exploitation, emphasizing the importance of employee vigilance. Often overlooked, the human element is a significant factor in cybersecurity; an educated workforce can mitigate risks considerably.
Discovery is paramount in the Detect function, which emphasizes the importance of timely identification of cybersecurity events. Organizations must cultivate capabilities for continuous monitoring and detection of anomalies, which may indicate a breach or potential threat. This requires the deployment of advanced detection technologies, such as intrusion detection systems (IDS) and security information and event management (SIEM) platforms. However, it is not merely about technology; it requires an organizational culture that promotes vigilance and responsiveness to deviations in normal behavior.
In the event of a breach or threat, the Respond function delineates how organizations should react. Effective incident response planning is imperative. An organization cannot afford to be reactive in the face of cyber incidents; a thoughtfully constructed incident response plan ensures that employees are cognizant of their roles in such scenarios. The aim is succinct: minimize the impact of the breach, communicate effectively both internally and externally, and fortify defenses against future incidents. The necessity of simulations and training exercises cannot be overstated; these practices prepare an organization to handle stress and chaos in real-time.
The final function, Recover, is often overshadowed by the urgency associated with the previous steps. Yet, it is critical for restoring operations and maintaining trust with stakeholders after an incident. Recovery strategies involve not only the restoration of systems and data but also the evaluation of lessons learned. These insights can inform future efforts and revisions of security protocols. Recovery is not merely about bouncing back; it encompasses forward-thinking strategies to prevent the recurrence of similar incidents.
An intriguing observation regarding the NIST Cybersecurity Framework is its emphasis on continuous improvement. In the unpredictable landscape of cyber threats, organizations that rest on their laurels are likely to become victims. Continuous assessment and adaptation in response to evolving technologies and threat actors are paramount. This embodies a proactive rather than a reactive posture towards cybersecurity, encouraging organizations to view their security measures as a living dynamic rather than a static requirement.
The interplay among the core functions reveals an intricate network of actions that, when executed in harmony, can significantly bolster an organization’s cybersecurity posture. It is essential to acknowledge that the implementation of this framework should be customized to an organization’s unique circumstances, including its industry, size, and risk profile. Embracing the framework as a flexible tool rather than a rigid mandate enables organizations to navigate their specific vulnerabilities more effectively.
As cyber threats become increasingly sophisticated, there exists a growing fascination with frameworks like NIST. The intrigue stems from their potential to demystify the complexities surrounding cybersecurity. By delineating a structured approach, the NIST framework provides clearer pathways for organizations to follow, thereby reducing the ambiguity that often accompanies cybersecurity strategies.
In conclusion, the NIST Cybersecurity Framework is not merely a set of guidelines but a strategic orientation towards safeguarding information systems. It acknowledges the multifaceted nature of cybersecurity, allowing organizations to cultivate resilience against cyber threats. As organizations continue to grapple with emerging vulnerabilities, the framework serves as an invaluable resource, guiding them toward a more secure digital future, embodying the essence of prevention, preparedness, and recovery in the modern era.







Leave a Comment