As quantum computing burgeons from theoretical conjecture into practical application, the ramifications for cybersecurity are profound and multifaceted. The advent of quantum processors capable of executing computations exponentially faster than classical computers raises critical inquiries: Will quantum computing render current cybersecurity paradigms obsolete? To address this intricate issue, it is essential to explore the intersections of quantum mechanics, encryption methodologies, and potential countermeasures.
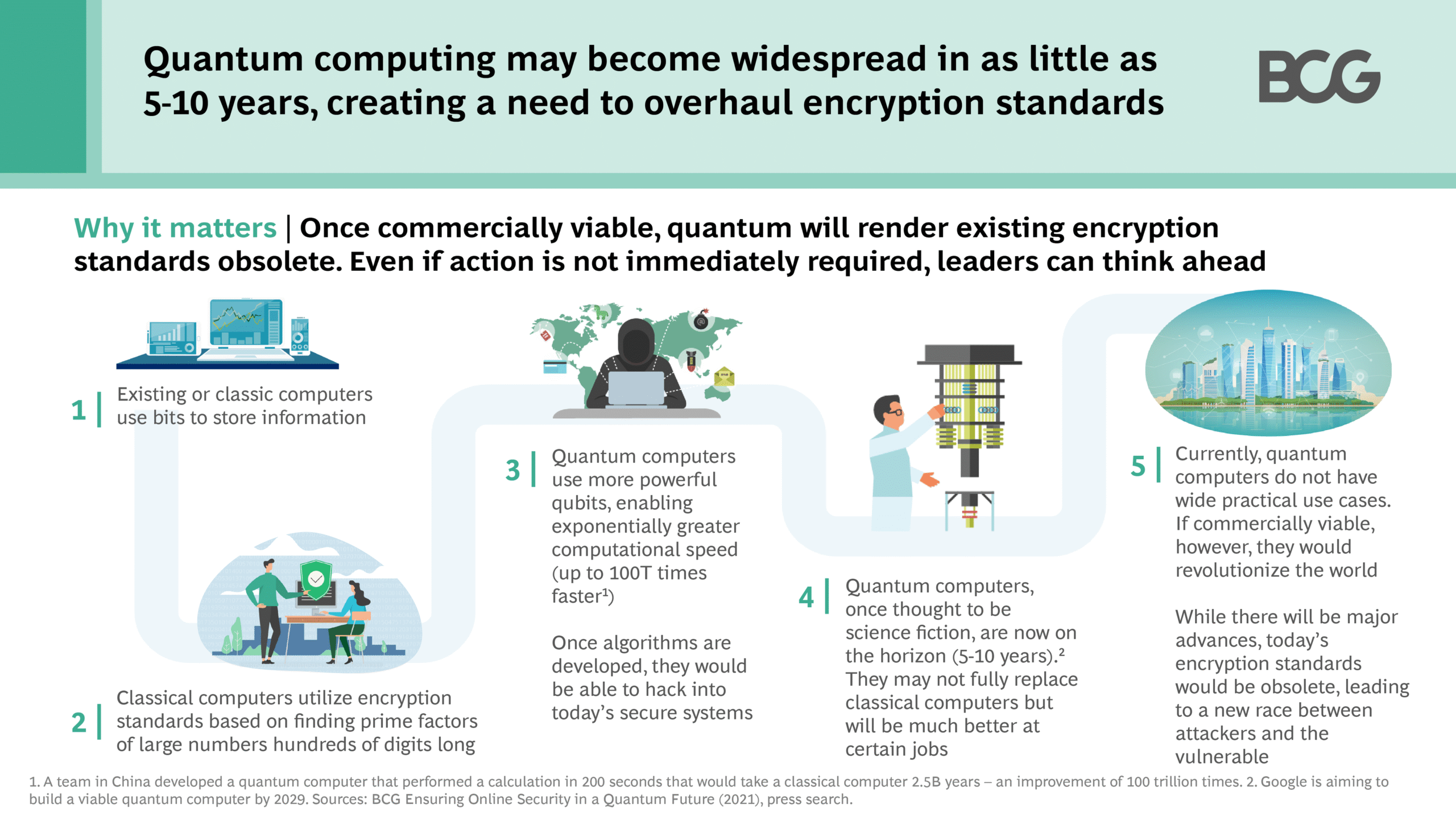
The cornerstone of contemporary cybersecurity relies heavily on cryptography, particularly asymmetric encryption algorithms such as RSA and ECC (Elliptic Curve Cryptography). These cryptographic methods underpin secure communications across the internet, safeguarding everything from financial transactions to personal data. Classical encryption schemes depend on complex mathematical problems, such as the factorization of large integers or the computation of discrete logarithms—tasks that are computationally burdensome for classical machines but manageably feasible for quantum computers equipped with relevant algorithms, notably Shor’s algorithm.
Shor’s algorithm presents a formidable challenge to current encryption standards by enabling a quantum computer to factor large integers in polynomial time. This potential shift threatens to unravel the very fabric of digital security as we know it. If a sufficiently powerful quantum computer could be deployed, it could hypothetically decrypt sensitive data, rendering established encryption tactics ineffective. Consequently, the urgency to transition to quantum-resistant algorithms intensifies.
Foremost among the cryptographic advancements is lattice-based cryptography, touted for its resistance to quantum attacks. Lattice-based schemes create hard mathematical problems that remain intractable even for quantum computers. Other contenders in the post-quantum cryptography landscape include multivariate polynomial equations and hash-based signature schemes. However, the transition from classical to quantum-resistant cryptography is fraught with challenges. For one, it requires an extensive overhaul of existing infrastructures and protocols, mandating cooperation across industries, governments, and academia.
Nevertheless, it is essential to dissect the broader cybersecurity ecosystem. While quantum computing poses threats to cryptographic systems, its emergence also opens avenues for enhanced security methodologies. Quantum key distribution (QKD) is one such innovation, leveraging the principles of quantum mechanics to enable secure communication channels. By using quantum bits (qubits) and the phenomenon of quantum entanglement, QKD ensures that any attempt at eavesdropping is detectable. The theoretical imperviousness to interception positions QKD as a compelling alternative to traditional key exchange mechanisms in a post-quantum world.
Despite the alluring prospects of quantum-enhanced security measures, the reality remains that not all cybersecurity threats will be neutralized by advancements in quantum computing. Threat vectors continually evolve, fostering an environment resembling a perpetual arms race. While quantum attacks may disrupt traditional encryption systems, other attack vectors persist autonomously: social engineering, insider threats, or zero-day vulnerabilities remain impervious to quantum advancements. The failure to acknowledge the comprehensive spectrum of cybersecurity threats could lead organizations to become overly reliant on quantum solutions at the expense of established defensive strategies.
Furthermore, the development of quantum computing itself is not a monolithic challenge. The disparity in quantum capabilities across organizations presents a dilemma. Current quantum processors are still in their infancy, with limited qubit counts and error-correction capabilities. As such, the existential threat posed by quantum computing remains largely prospective at the moment. Organizations must grapple with how to allocate resources—whether to fortify their defenses against theoretical quantum threats or to address the pressing vulnerabilities present in today’s digital landscape.
Another consideration is the regulatory and ethical landscape associated with quantum advancements. Governments and international agencies must devise frameworks that ensure that quantum technologies are employed responsibly. The potential misuse of quantum capabilities for malicious purposes—such as state-sponsored cyberattacks—ultimately leads to questions of accountability and governance. Therefore, addressing the implications of quantum computing on cybersecurity necessitates an interdisciplinary dialogue that encompasses technology, policy, and ethical considerations.
In light of these complexities, the dichotomy between optimism and apprehension surrounding quantum computing necessitates a balanced perspective. While the capabilities of quantum computers may outpace traditional defense strategies in specific contexts, the cybersecurity field possesses a resilient and adaptable nature. History illustrates that as threats evolve, so too do the methodologies employed to mitigate them. Thus, rather than heralding the obsolescence of cybersecurity, quantum computing augments the urgency to innovate and re-evaluate existing practices.
Moreover, the looming quantum threat has catalyzed an unprecedented collaboration between researchers, industries, and governmental bodies, driving innovations in both cybersecurity protocols and quantum technologies. The race towards quantum resilience incorporates not just cryptographic advancements but also systemic improvements in security architecture, emphasizing the integration of quantum principles into design philosophies and operational frameworks.
In conclusion, while quantum computing heralds a new era for encryption and cybersecurity, it does not signify the end of the established practices but rather a pivotal inflection point. The challenge lies not only in adapting to novel threats but in leveraging quantum advancements to bolster existing defenses. As interdependencies between quantum technology and cybersecurity deepen, a deliberate and informed response is imperative to ensure a secure digital future. The discourse surrounding quantum computing and cybersecurity must remain dynamic, nuanced, and comprehensive to navigate the complexities and efficacy of the evolving digital landscape.







Leave a Comment