In the modern digital landscape, the importance of secure communication cannot be overstated. The implementation of secure sockets layer (SSL) protocols has become a stalwart in safeguarding sensitive data transmitted over the internet. However, a common question arises: Is SSL symmetric, asymmetric, or both? To fully comprehend this topic, we must dissect the concepts of symmetric and asymmetric encryption and elucidate how they are utilized in the SSL framework.
Before delving into the intricacies of SSL, it is crucial to understand the foundational concepts of encryption. Encryption serves as the linchpin in data confidentiality, converting plaintext into ciphertext through algorithms and keys. Symmetric encryption employs a singular key for both encryption and decryption processes. This reliance on a single key uniquely positions symmetric encryption as both efficient and swift. Common algorithms in this category include Advanced Encryption Standard (AES) and Data Encryption Standard (DES).
Conversely, asymmetric encryption employs an innovative dual-key system, encompassing a public key for encryption and a private key for decryption. This architecture enhances security, as the public key can be disseminated without compromising the integrity of the private key. RSA and Elliptic Curve Cryptography (ECC) are prominent asymmetric algorithms notable for their robust security paradigms.
With these definitions crystallized, we can now navigate toward SSL and delineate its role in using both symmetric and asymmetric encryption. SSL, now more commonly replaced by Transport Layer Security (TLS), creates a encrypted tunnel between a client and server. This process is paramount for transactions necessitating security, such as online banking and e-commerce.
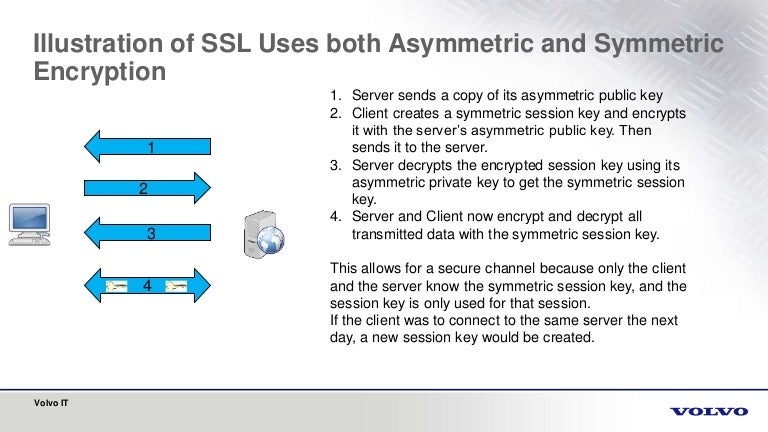
When a client attempts to establish a secure connection to a server using SSL, a process termed the SSL handshake occurs. This handshake serves as the initiation phase of the communication. Initially, the client sends a request to the server to initiate a secure connection. The server responds by transmitting its SSL certificate, which includes the public key, thus introducing asymmetric encryption into the dialogue. This stage is critical for validating the server’s identity and ensuring that clients are not communicating with malicious entities posing as legitimate servers.
The public key provided in the server’s certificate is then utilized by the client to establish a secure channel. The client generates a session key, a random symmetric key unique to the session. This session key is encrypted using the server’s public key and sent back to the server. Utilizing the private key, the server decrypts the session key, thereby establishing a secure connection devoid of eavesdropping. This nuanced interplay epitomizes the convergence of asymmetric and symmetric encryption within the SSL framework.
Upon the successful establishment of the session key, the communication transitions to symmetric encryption for the remainder of the session. This transition is pivotal as symmetric encryption is far swifter than asymmetric encryption, making it suitable for the voluminous data transmitted once the connection is secure. The session key allows both the client and server to encrypt and decrypt messages seamlessly. As a result, the considerable overhead of using asymmetric encryption for every piece of data is mitigated, leading to improved performance.
Thus, SSL employs both forms of encryption, exploiting the strengths of each to create a secure communication channel. Asymmetric encryption lends itself to the initial validation and secure exchange of keys, while symmetric encryption takes over for the data transmission phase, emphasizing efficiency and speed. This hybrid model is an astute design choice that ensures both security and performance.
Furthermore, the underlying security of any encryption mechanism relies heavily on the strength and management of the keys. For symmetric encryption, the security hinges on the secrecy of the session key. If the session key is exposed, unauthorized entities gain access to the data stream. In contrast, the security of asymmetric encryption lies in the computational difficulty of deriving the private key from the public key. This disparity emphasizes the necessity of employing robust key generation and management practices to maintain the integrity of the encryption methods used.
SSL and its successor, TLS, have evolved substantially since their inception, undergoing numerous revisions to enhance security algorithms and address vulnerabilities. Ongoing developments to combat potential threats, such as man-in-the-middle attacks and eavesdropping, further bolster the relevance of SSL in contemporary digital communication. Thus, maintaining an updated understanding of the protocols and refining security measures remains essential for stakeholders across industries.
In summary, it is evident that SSL is neither exclusively symmetric nor asymmetric; it is a sophisticated amalgamation of both types of encryption. This duality allows SSL to retain high levels of security while remaining efficient in managing the complexities of secure internet communication. As digital interactions become progressively integral to both personal and professional spheres, it is imperative for individuals and organizations to acknowledge the importance of SSL in safeguarding their communications and protecting sensitive information.
Ultimately, the evolution of encryption technologies and protocols warrants vigilance and an ongoing commitment to applied security practices. Individuals and organizations must endeavor to educate themselves on the nuances of SSL, appreciate the underlying encryption mechanisms, and implement robust security measures that encompass both symmetric and asymmetric paradigms.







Leave a Comment