Designing your own cipher can be an exhilarating intellectual pursuit. It offers an engaging means of exploring the intricate world of secret communication, propelling you into a realm where creativity meets logic. To effectively craft a functional cipher, it is crucial to navigate through a myriad of considerations, including the type of cipher, the system of keys, and the layers of complexity that can be incorporated into your design.
To begin, understanding the fundamental types of ciphers is imperative. Broadly, they can be classified into two categories: symmetric and asymmetric ciphers. Symmetric ciphers use the same key for both encryption and decryption. On the other hand, asymmetric ciphers employ a pair of keys, one for encryption and the other for decryption. These classifications hinge on the level of security required, the context of usage, and the complexity of implementation. Each type offers a unique framework that can be manipulated to create a bespoke cipher tailored to specific needs.
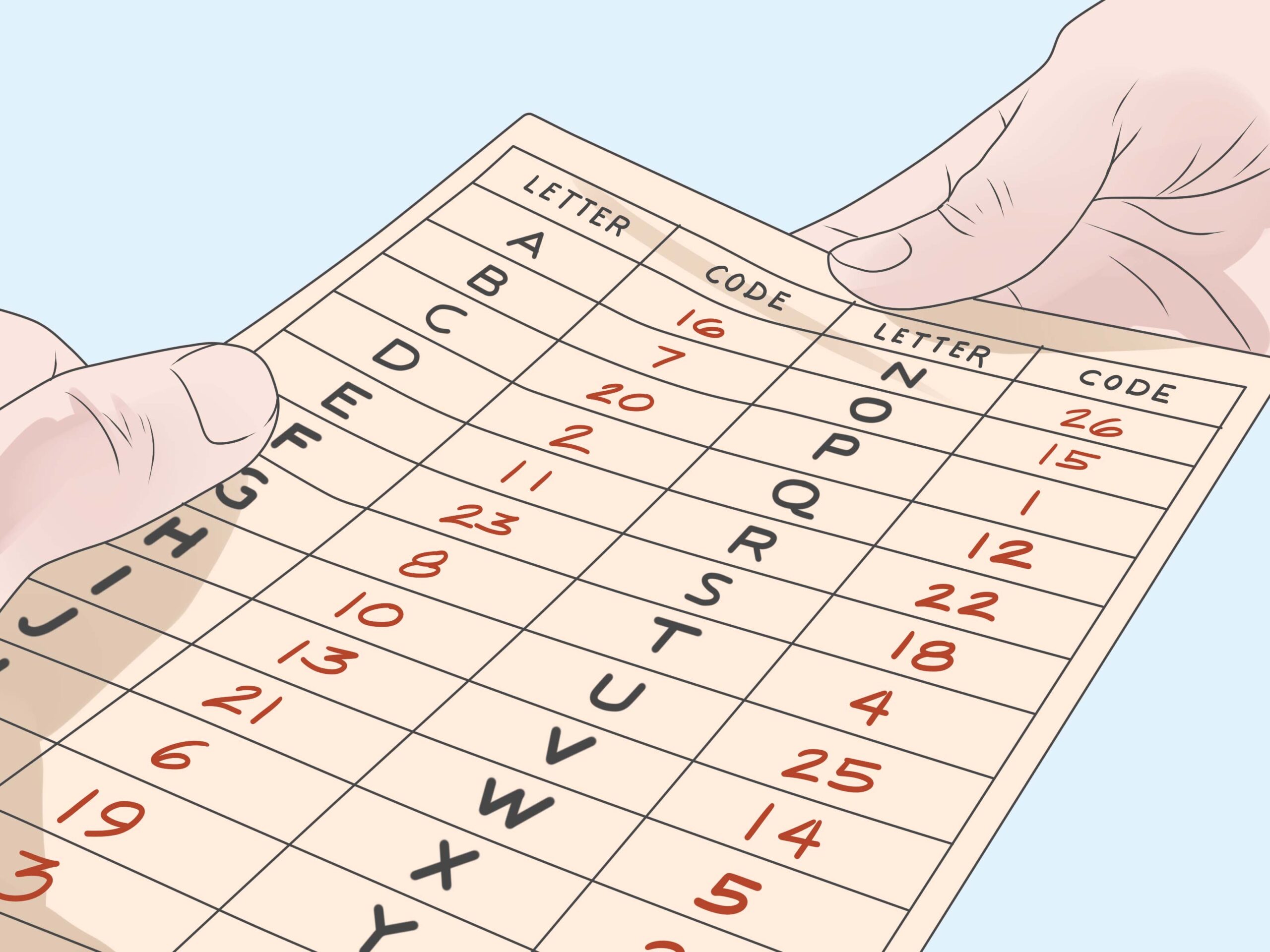
As you delve into the design process, it is paramount to consider the structural components of the cipher. This includes the alphabets used for substitution or transposition, the nature of key generation, and the algorithm employed. Substitution ciphers, for instance, transform letters into other letters, while transposition ciphers rearrange the letters in a particular pattern. By exploring various combinations of these methods, one can create increasingly sophisticated systems that defy easy decryption.
Next, the selection of a memorable yet obscure keyword that serves as the basis for the cipher must be considered. The keyword adds a layer of personalization and serves as the cornerstone for generating keys. When establishing a keyword, opt for strings that are unlikely to be guessed yet easy to recall. The entropy of your chosen keyword significantly influences the cipher’s durability against brute-force attacks, where an adversary attempts every possible combination to crack the code.
Once the foundational elements are in place, focus must shift to the intricacies of key generation. This can be achieved through various methods. Randomly generated keys can enhance security considerably, albeit with the trade-off of convenience. Alternatively, using predetermined algorithms based on the keyword can create a more systematic approach to key generation. The method you choose will influence the overall efficacy of your cipher. Remember, the goal is to create a system that is not only functional but also resilient against decryption attempts.
Another critical consideration is the incorporation of various layers of encryption. Layering enhances security but adds complexity to both encoding and decoding. Employing multiple ciphers sequentially or in tandem can significantly increase the challenge of breaking the code. Each layer can add an additional veil of obscurity, making it increasingly difficult for unintended recipients to decrypt the message. However, careful planning is required to ensure that the layers work harmoniously rather than detracting from the cipher’s effectiveness.
It is also essential to evaluate the practical application of the cipher. The medium through which messages will be communicated should inform how the cipher is designed. For instance, if the messages will be relayed via text messaging, your cipher must align with the constraints of character limits. Conversely, if the transmissions will occur on encrypted email platforms, a more intricate cipher may be viable. Understanding the context of your cipher will provide the necessary insight to optimize effectiveness.
Implementing your cipher presents the next challenge; a simple error in encoding can lead to complete misunderstandings. Therefore, devising a method to check the integrity of the transmitted message is crucial. Consider implementing redundant systems such as checksums or hash verification processes. These systems can signal if a message has been tampered with, allowing for the integrity of communication to be preserved.
Following the implementation, testing becomes vital. Through the intricate process of trial and error, you will discover vulnerabilities within your design. Engage peers or colleagues who are unaware of your designed cipher to elicit their perspectives. Their attempts to decode your messages can highlight weaknesses that may not have been apparent during the design phase. Learning from these evaluations can facilitate the refinement of your cipher, enhancing its security.
Furthermore, take into account the ongoing evolution of cryptography. As technology advances, so do the methodologies adopted for encoding and decoding messages. It is wise to stay informed about contemporary developments in cryptography, as this knowledge can influence how you approach your own designs. The ever-changing landscape may prompt you to continually adapt your cipher to retain its effectiveness over time.
In conclusion, designing your own cipher transcends the mere act of creating a system. It encapsulates a deeply analytical process that intertwines creativity with rigorous logic, affording you an opportunity to communicate securely in an increasingly interconnected world. With perseverance, an understanding of cryptographic fundamentals, and a willingness to innovate, you can craft a cipher that not only meets your needs but also invites intrigue and exploration into the enigmatic world of secret writing. The promise lies in the discovery: each cipher you design will challenge your intellect and inspire a shift in your perspectives on communication and security.








Leave a Comment