In an era where digital communication permeates every facet of daily life, the necessity for robust security measures has never been more pressing. End-to-end encryption (E2EE) emerges as a formidable defense mechanism against eavesdropping and unauthorized access. However, not all E2EE solutions are created equal. This piece elucidates the critical factors to consider when selecting end-to-end encryption that is both effective and resilient.
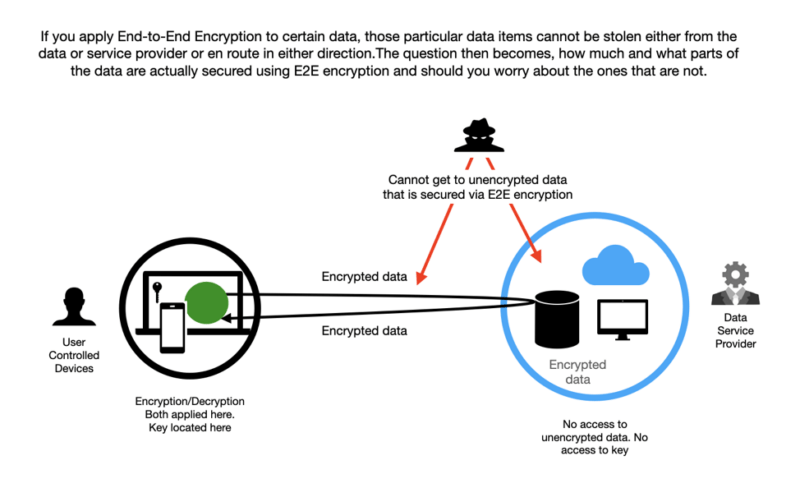
At the onset, it is essential to comprehend the core fundamentals of end-to-end encryption. E2EE ensures that only the communicating users can read the messages, effectively shielding the content from any intermediaries, including service providers. This technology employs sophisticated algorithms that encrypt data at its source and decrypt it only when it reaches its destination. Understanding these fundamentals provides a foundation for evaluating various encryption products.
First and foremost, scrutinizing the encryption protocol and its implementation is paramount. Various encryption standards exist, and some are inherently more secure than others. For instance, the Advanced Encryption Standard (AES) is widely regarded as one of the most secure algorithms available, especially when employed with a key length of 256 bits. Conversely, less potent encryptions, such as those relying on obsolete algorithms, can render the entire communication vulnerable. When examining protocols, a discerning consumer will favor systems that utilize AES in conjunction with secure key exchange methods, such as Diffie-Hellman or Elliptic Curve Cryptography (ECC).
Furthermore, transparency is a hallmark of a credible E2EE solution. Opt for providers that make their code publicly accessible or undergo regular security audits by independent third parties. This openness indicates a commitment to accountability and allows developers to identify and rectify potential vulnerabilities. A history of security breaches or inadequate response strategies can be a red flag. A forthright company will typically have a transparent approach, providing users with comprehensive details of their encryption methods and security practices.
Another salient consideration is the usability of the E2EE solution. Security measures that are arduous to implement or cumbersome to use are often abandoned in favor of convenience. An effective end-to-end encryption tool should strike a harmonious balance between robust security and user-friendly design. Intuitive interfaces, seamless integration with existing systems, and minimal friction in the user experience can significantly influence adoption rates. Moreover, consider whether the encryption tool supports multiple platforms and devices, ensuring functionality across the various environments users may encounter.
In addition to ease of use, assessing the provider’s data retention policies is critical. Some services may retain data or metadata even when utilizing end-to-end encryption, which can undermine the overall effectiveness of the encryption. Ideally, the provider should have a clear policy that minimizes data retention and maximizes user privacy. Examine the terms of service carefully to discern how data is handled and whether any provisions exist for user data requests from law enforcement — elements that could potentially expose users to surveillance.
Moreover, the geographic jurisdiction under which the encryption provider operates should not be overlooked. Different countries have varying laws regarding data privacy and security. A provider based in a jurisdiction with robust privacy laws may offer better protection against governmental surveillance. Conversely, some jurisdictions may have laws that compel companies to cooperate with law enforcement, potentially compromising user privacy. Gaining a thorough understanding of these geopolitical considerations can empower users to make informed choices about their encryption methods.
The support and community surrounding a particular E2EE solution can also play a pivotal role in its effectiveness. A rich ecosystem of users and contributors can foster better resilience against vulnerabilities, leading to quicker identification and remedial measures when issues arise. Active forums, customer support channels, and comprehensive user documentation are essential elements that indicate a provider’s dedication to both the product’s integrity and user satisfaction.
It is also prudent to reflect upon the encryption key management process. End-to-end encryption’s security significantly hinges on how the keys are generated, distributed, and stored. Solutions that peak in transparency about their key management approach are preferable. Two-factor authentication (2FA) for key access, using hardware tokens or biometric verification, can further bolster security, ensuring that only authorized users can decrypt sensitive information.
An equally important aspect is the potential for backdoors within the encryption implementation. These backdoors, whether intentional or unintentional, can be exploited by malicious actors. Evaluate any claims regarding the presence of backdoors critically. A reputable provider will staunchly advocate against such vulnerabilities and reassure users of their commitment to unfettered security.
Ultimately, choosing an effective end-to-end encryption solution necessitates thorough due diligence. By critically evaluating encryption protocols, usability, transparency, geographical jurisdiction, support structures, key management, and potential vulnerabilities, users can select E2EE solutions that not only promise security but deliver it. In a world fraught with digital risks, implementing appropriate encryption measures is not merely advisable; it is imperative.








Leave a Comment