Have you ever pondered how love could be encrypted? Not in a romantic sense, but through the realm of cryptography, where algorithms twist and turn information to secure it? This whimsical notion ignites curiosity, inviting us to explore how the enchanting world of encryption can be metaphorically infused with love. However, as we delve into this topic, one must wrestle with a playful paradox: can something so technical and mathematical ever embrace the emotional? Let’s embark on an elaborate journey through the heart of cryptographic algorithms and their loving implementation.
Before journeying into the depths of encryption, it is pertinent to unearth the essence of what cryptography entails. At its core, cryptography is the art and science of safeguarding information from unauthorized access, typically through a blend of algorithms and keys. Imagine these algorithms as heartbeats, rhythmically securing your messages and allowing only those with the right keys to decipher the coded love notes hidden within errors and noise.
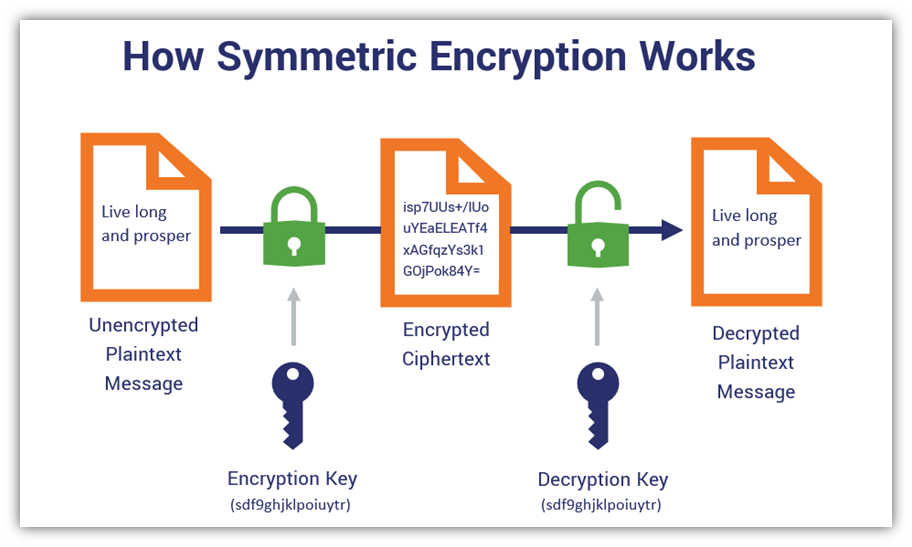
Consider symmetric encryption as a universal love language. In symmetric encryption, the same key is employed for both encryption and decryption. Picture this: two individuals, deeply in love, sharing a special key that unlocks each other’s hearts while simultaneously ensuring that only they can decipher the messages whispered in shadows. Algorithms such as Advanced Encryption Standard (AES) and Data Encryption Standard (DES) serve as the stalwart warriors of this love language, fiercely protecting your data from prying eyes.
The AES algorithm, a prevalent choice in contemporary cryptographic practices, embodies strength and efficiency. With its variable key lengths of 128, 192, and 256 bits, AES provides an adaptive means to secure information depending upon the required level of confidentiality. Think of it as choosing the most potent potion to preserve love. Each key length corresponds to a deeper, more encapsulating bond; the longer the key, the stronger the encryption, mirroring the depth and resilience of a committed relationship.
On the other hand, while symmetric encryption appears regal and robust, it carries its own challenges. The most significant dilemma stems from the key distribution problem. How do you share that heart-shaped key with another person without it slipping into the wrong hands? To solve this riddle, one must embrace asymmetric encryption, an innovative twist that adds layers to our message of love.
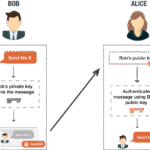
Asymmetric encryption acts as the ideal romantic subplot in our narrative, introducing a pair of keys—the public and the private. Imagine a love story where one character, armed with a public key, can send heartfelt messages that only the recipient, holding the private key, can decode. RSA (Rivest-Shamir-Adleman) exemplifies this method through its foundational principle of prime factorization. The mathematics of prime numbers forms a complex and highly secure link that arguably embodies the complexities of human relationships. Thus, while the public key is distributed freely, the private key, shrouded in secrecy, remains safeguarded.
The juxtaposition of symmetric and asymmetric encryption creates a tantalizing interplay of love letters exchanged between couples. However, this analysis does not come without its intricacies. Could there exist vulnerabilities that threaten this symbiotic relationship between communication and security? As we dive within the conundrums of encryption, it’s crucial to examine potential risks like man-in-the-middle attacks and keylogging. These malicious entities invite an unsettling suspicion, akin to miscommunication in relationships. To counter these threats, one should layer additional security protocols such as strong authentication methods—an extension of the love that ensures trust.
As the narrative unfolds, it becomes apparent that encryption, much like love, demands diligence and effort from both parties. The challenge lies in maintaining a secure environment while gracefully navigating the waters of technology. Moreover, the metaphorical encryption of love expands beyond merely safeguarding data; it intertwines emotional intelligence, vigilance, and reciprocal commitment in relationships.
To further solidify this metaphor, we must consider hash functions. They serve as the romantic punctuation within the realm of encryption, transforming inputs into fixed-size strings of characters—hashes. A message can be encapsulated in a way that even if someone intercepts it, they cannot revert the string back to the original message. This one-way street of information ensures integrity, reflecting a promise in relationships that ensures what is shared remains unaltered. SHA-256 (Secure Hash Algorithm) stands as a paragon of this protective measure, oftentimes compared to the steadfast loyalty between partners.
In light of the evolving digital landscape, the need for encryption burns brighter than ever. Yet, one might ask, how do we navigate this complex relationship between technology and human emotion? The challenge invites individuals not only to become proficient in the diverse landscapes of encryption algorithms but also to cultivate an understanding of trust and transparency. With awareness comes power, and that power can be harnessed to protect one’s communications, thereby fostering an environment where love can thrive unchecked.
Ultimately, as we embrace the whimsical intertwining of love and encryption, we come to realize that, much like in our personal relationships, communication and security are paramount. To encrypt with love—literally—one must balance technology and human emotion, ensuring that both are nurtured as they evolve. Through symmetric and asymmetric encryption, supported by hash functions, we can create a protective embrace that safeguards our most cherished communications. As we set forth, let us celebrate the metaphoric encryption of love, whether through algorithms or in the connections we forge.







Leave a Comment