Asymmetric encryption, also known as public key cryptography, is a powerful method for securing data that frequently mystifies those not immersed in technological parlance. To demystify this concept for friends who might not be versed in technical jargon, one must first establish a relatable foundation, utilizing analogies and scenarios from everyday life to facilitate comprehension.
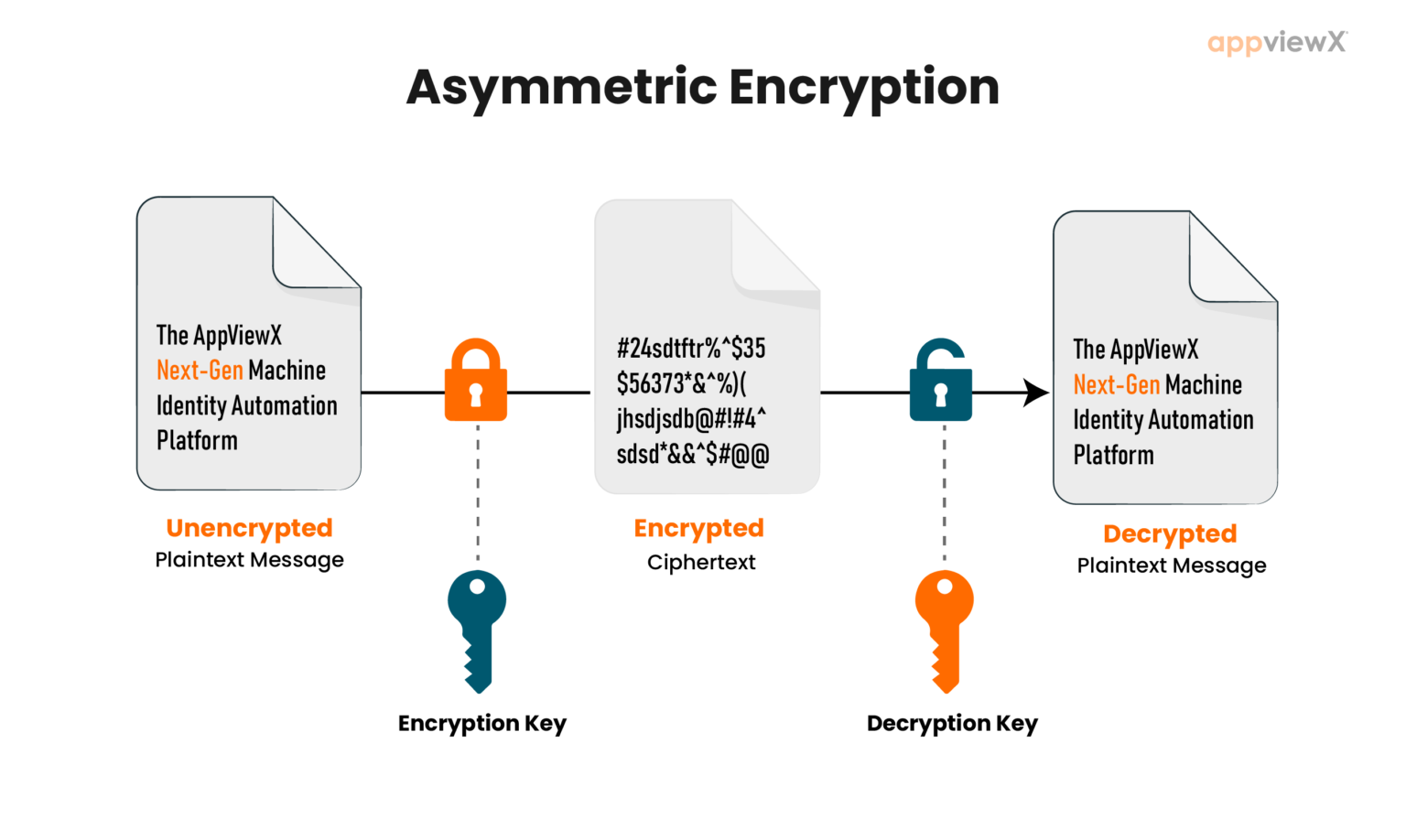
At its essence, asymmetric encryption functions like a secure communication channel that employs two keys: a public key and a private key. Imagine an individual wishing to send a confidential message. Instead of using a single key that could be easily intercepted, this person utilizes your public key, which anyone can obtain. Once the message is encrypted with this public key, it is rendered indecipherable to all but you—the sole possessor of the corresponding private key. This mechanism ensures that even if a malicious entity intercepts the message, it remains incomprehensible, safeguarded by cryptographic barriers.
When exploring how asymmetric encryption operates, one could draw parallels to a locked mailbox system. Picture a mailbox that can be locked with a unique key. Anyone can deposit a message into the mailbox as long as they have access to the public key, symbolized as an open slot. However, only the individual with the private key can retrieve and unlock the mailbox to access the contents. In this way, the security of the system is upheld, and only intended recipients can gain access to the information inside.
To solidify comprehension, consider the roles of the keys. The public key is akin to an address that one generously shares, enabling others to send messages. The private key, conversely, is a closely guarded secret—akin to a personal identification number (PIN) that must never be disclosed. This binary relationship between the keys undergirds the security of many modern digital communications, ensuring privacy in a world increasingly fraught with digital intrusions.
As one delves further into the practical applications of asymmetric encryption, it is enlightening to consider its pivotal role in secure web browsing. When an individual accesses a secure website (indicated by the HTTPS prefix), asymmetric encryption is at work. The website provides its public key to users, allowing their browsers to establish a safe connection. The browser then encrypts the data transmitted using this public key, ensuring that any data sent back and forth, such as credit card details, remains confidential. Thus, a non-techie friend can appreciate its significance in everyday transactions, reinforcing a more profound understanding of cybersecurity.
Yet, one must also address the limitations inherent in asymmetric encryption to cultivate a holistic understanding of the topic. For instance, while it offers significant advantages over symmetric encryption—where a single key is used for both encryption and decryption—it is computationally more intensive. The mathematical complexities required to generate key pairs can lead to slower performance, especially with larger data sets. Consequently, in practice, asymmetric encryption is often paired with symmetric encryption to achieve optimal efficiency while ensuring robust security.
Another common perception that could be discussed involves key management. Although the public key can be shared liberally, the private key is a sensitive piece of information that must be safeguarded. If a malicious actor gains access to one’s private key, the entire communication is compromised. Chew on that; even the most sophisticated encryption is rendered futile if the key holder’s security practices falter. This disparity underscores the vital importance of adopting stringent measures—such as using hardware security modules and state-of-the-art password management techniques—to protect the keys.
To further enhance understanding, introduce real-world examples illustrating where the technology is employed. One can point to blockchain technology, particularly in cryptocurrencies, where asymmetric encryption secures transactions, preventing fraud and unauthorized access. Additionally, digital signatures—a critical component of software distribution—rely on this same principle. When software developers sign their applications with their private key, it serves as a guarantee that the application has not been tampered with by cybercriminals, offering users a measure of trust.
In academic, governmental, and corporate sectors, asymmetric encryption is indispensable. Governments employ it to secure communications involving sensitive data, while corporations utilize it to protect intellectual property. By supplying relatable scenarios, one can illustrate that this cryptographic method transcends technical labyrinths and profoundly shapes various facets of contemporary life.
In conclusion, bridging the knowledge gap surrounding asymmetric encryption involves methodical elucidation through relatable analogies, real-world applications, and a concise examination of its inherent limitations. By catering to the non-techie’s perspective, one can unveil the layers of complexity that shroud this potent security mechanism. This approach not only fosters understanding but cultivates an appreciation for the significance of encryption in preserving privacy and securing our digital interactions in an increasingly interconnected world.







Leave a Comment