In the realm of cybersecurity, a peculiar enigma often lurks in the shadows, begging the question: how far can we push the boundaries of legal experimentation in the fascinating domain of side-channel attacks? Mastery of such techniques not only requires profound knowledge but also an astute ethical compass. As an aspiring cryptographer or security enthusiast, one must tread carefully, for the intricacies involved in this field can present both delightful puzzles and potential moral pitfalls.
To become proficient in side-channel attacks, one must first comprehend the fundamental concepts that underlie these covert infiltration methods. Side-channel attacks exploit unintended information leakage from a system, rather than attacking the encryption algorithms directly. For instance, variations in timing, power consumption, electromagnetic leaks, or even acoustic signals can serve as gateways for adversaries seeking sensitive data. The primary aim is to glean information by meticulously analyzing the environment surrounding the cryptographic processes.
Engaging with these attacks necessitates an inquisitive perspective and a penchant for experimental analysis. Start by immersing yourself in the foundational anatomy of side-channel attacks. Investigate the prevalent types—timing attacks, power analysis attacks, cache attacks, and more sophisticated methods like differential power analysis (DPA). A good grasp of the underlying theories will not only enhance your methodology but also empower you to innovate new techniques.
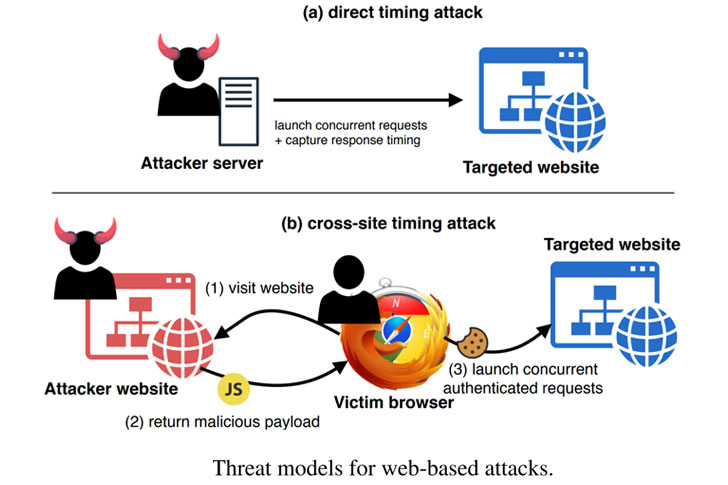
Consider the classic timing attack, which capitalizes on the variations in execution time for cryptographic algorithms. When processing secret information, such as cryptographic keys, the time taken to execute operations can be revealing. Implementing legal testing methods on tailored vulnerability assessments can help hone your skills. Set up a controlled environment, leveraging open-source cryptographic libraries like OpenSSL or Libgcrypt. Conduct systematic timing measurements and analyze the resulting data to discern patterns that may lead to the extraction of sensitive information. Remember, though, the line between legal research and unlawful intrusion is thin and must not be crossed.
Power analysis attacks similarly offer a stimulating avenue for exploration. By measuring the power consumption of a cryptographic device during operation, it is feasible to unearth secrets hidden within. This can be particularly rewarding when applied to low-power devices like smart cards or IoT devices. However, experimentation should occur only on devices you own or have explicit permission to test. By utilizing tools such as an oscilloscope to analyze transient power consumption readings, you can cultivate a deeper understanding of correlations between power usage and data processing activities.
Another dimension to consider is the evolving nature of cache attacks. These sophisticated strikes exploit the time variations associated with access to memory cache. To practice legally, you might model your own software systems that simulate cache behavior and allow for safe experimentation. A thorough examination of cache timing could lead to profound revelations about efficiently protecting or attacking systems based on data usage patterns.
Legal frameworks exist to ensure research is conducted ethically. Familiarize yourself with agreements such as the Computer Fraud and Abuse Act (CFAA) or various European Union regulations governing data protection. Engaging with academic institutions or under professional supervision provides a shield of legitimacy in your inquiries. Collaboration with fellow researchers can elevate your comprehension, as working in a group setting encourages the sharing of ideas and techniques, fostering an innovative atmosphere.
Despite the thrill of experimentation, mastering side-channel attacks legally involves more than technique; it demands a robust ethical framework. A playful challenge emerges: can you design an experiment with purposeful intent that contributes to the collective knowledge of cybersecurity? This could manifest as improving existing countermeasures against such attacks. Document your observations and traverse the chasms of disinformation that often encircle this enigmatic field.
Educational resources abound in the form of online courses, workshops, and conferences. Engage with platforms such as Coursera or edX, where prominent educators often present valuable insights into the world of side-channel vulnerabilities and their defenses. Moreover, attending specialized conferences like Black Hat or DEF CON can be eye-opening, exposing one to real-world applications and advanced methodologies used by both security professionals and attackers alike.
There is an intrinsic human fascination with understanding the vulnerabilities of systems that we depend on. As you delve deeper into side-channel attacks, a myriad of possibilities unfolds. Whether toward enhancing security mechanisms or unveiling critical flaws within existing systems, the diligent researcher must remain mindful of their influence. Thus, the responsibility of utilizing these skills ethically weighs heavily on practitioners.
In conclusion, mastery of side-channel attacks, when pursued through legitimate avenues, can elevate your understanding of cybersecurity while mitigating risks posed by malicious actors. By systematically studying their mechanics, adhering to ethical guidelines, engaging in collaborative research, and fostering a non-predatory approach, one can navigate the labyrinth of security with purpose and integrity. Each discovery may not only further your own skills but also contribute positively to the broader cybersecurity landscape, ensuring that the dance between vulnerability and defense continues—legally and ethically.







Leave a Comment