Learning how to implement Advanced Encryption Standard (AES) can seem daunting, especially for beginners. Yet, with an organized approach, this complex topic can be navigated effectively. This guide will elucidate the facets of AES encryption while examining the types of content that learners can expect to encounter along their educational journey. Whether through theoretical understanding or practical application, a structured method can help demystify the process.
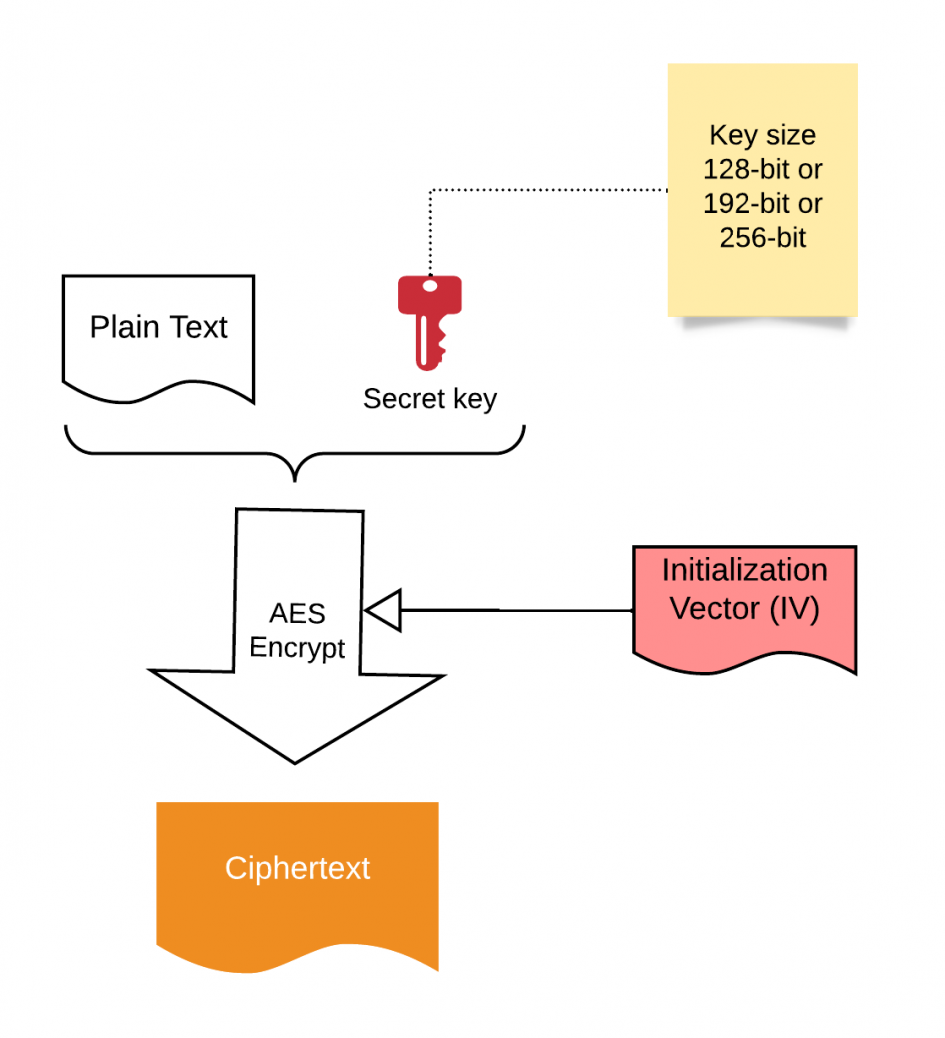
To begin, one must grasp the foundational concepts of cryptography. AES, a symmetric key encryption algorithm, secures data by transforming plaintext into ciphertext utilizing a key. This transformation is reversible, empowering authorized entities to retrieve the original data. A comprehensive understanding involves delving into symmetric vs. asymmetric encryption, where the former employs a single key for both encryption and decryption, while the latter utilizes a pair of keys.
When embarking on the journey to master AES encryption, one can anticipate varied types of content. Initially, introductory materials are indispensable. These resources are designed to provide a broad overview of AES, outlining its history, significance, and architecture. Readers might encounter articles, videos, and infographics that elucidate these fundamental concepts, laying a groundwork for deeper exploration.
Next, learners will likely engage with detailed technical documents and white papers. These scholarly articles delve into AES’s specifications, including block size, key lengths, and the encryption process itself, characterized by rounds of transformation and substitution. The importance of the key schedule, known as key expansion, ensures the security of the algorithm by deriving multiple keys from the original key, enhancing the robustness of encryption.
Once the theoretical groundwork is established, practical tutorials become integral to the learning experience. These step-by-step guides frequently appear in the form of programming tutorials in languages such as Python, Java, or C#. A discerning learner will recognize the value of engaging with interactive platforms or coding exercises that allow for hands-on practice. The active involvement in crafting encryption and decryption implementations fosters a pragmatic understanding of AES, reinforcing theoretical knowledge through real-world application.
Moreover, open-source libraries significantly facilitate the learning of AES encryption. By utilizing robust frameworks such as OpenSSL, learners can experiment with pre-existing implementations, modifying parameters to observe varied outcomes. This practical engagement aids in bridging the gap between theoretical principles and applied knowledge, transforming abstract concepts into tangible skills.
A vital component of understanding AES encryption is the exploration of its security properties. Here, learners encounter content addressing potential vulnerabilities, side-channel attacks, and the importance of key management. Engaging with case studies that illustrate the impact of compromised encryption, such as high-profile data breaches, elucidates the critical role AES plays in contemporary data security. Cognizance of these security dilemmas helps solidify the necessity of employing encryption ethically and responsibly.
Furthermore, learners should familiarize themselves with various cryptographic protocols that leverage AES, including Transport Layer Security (TLS) and Internet Protocol Security (IPsec). Understanding how AES synergizes with these protocols provides insight into its practical applications in securing network communications. Such knowledge equips learners with a broader perspective on encryption beyond just the algorithm itself.
In addition, it is essential to explore alternative encryption algorithms. While AES remains prevalent, understanding the contrasts with algorithms like RSA or Blowfish can enrich a learner’s comprehension of the cryptographic landscape. This exploration enables learners to select appropriate encryption methods based on situational requirements and desired security features.
Participating in forums and communities dedicated to cryptography can also enhance the learning experience. Engaging in discussions with like-minded individuals can uncover additional resources, answer lingering questions, and foster a collaborative environment for problem-solving. Platforms such as Stack Overflow or specialized cryptography stack exchange forums allow learners to contribute and glean knowledge from the community, reinforcing their understanding through interaction.
As learners progress, continuous practice through challenges and competitions, such as Capture The Flag (CTF) events, can provide invaluable experience. These exercises enhance problem-solving skills, requiring participants to employ AES in real-world contexts, reinforcing learning and enhancing retention.
Additionally, learners should keep abreast of current trends and advancements in cryptography. Joining newsletters, podcasts, or attending webinars can provide insight into the ever-evolving landscape of encryption technology. Such resources help learners remain informed about developments in cryptographic research, potential vulnerabilities, and emerging standards—all of which contribute to a well-rounded understanding of AES.
The complexities inherent in learning AES encryption can be overwhelming, but with a strategic approach and structured content consumption, it becomes a manageable endeavor. By engaging with diverse types of resources—ranging from introductory articles to practical tutorials and community forums, learners can cultivate a profound comprehension of AES encryption.
Ultimately, the journey to mastering AES encryption is not merely about understanding the algorithm itself but grasping its significance in the broader context of data security. In an era where data breaches and cyber threats proliferate, the ability to implement AES encryption effectively is more than a technical skill; it is a vital contribution to safeguarding sensitive information.








Leave a Comment