In the digital age, where sensitive information flows like blood through the veins of society, the security of this information is paramount. Encryption, often likened to a fortified fortress, promises safety against the marauding threats of cybercriminals. Yet, is your encryption method a paragon of security, or is it merely a house of cards, susceptible to the slightest breeze? To answer this question, one must embark on a meticulous journey of evaluation. The quest to ascertain if your encryption method is foolproof involves several key steps, each unfolding layers of complexity akin to peeling an onion.
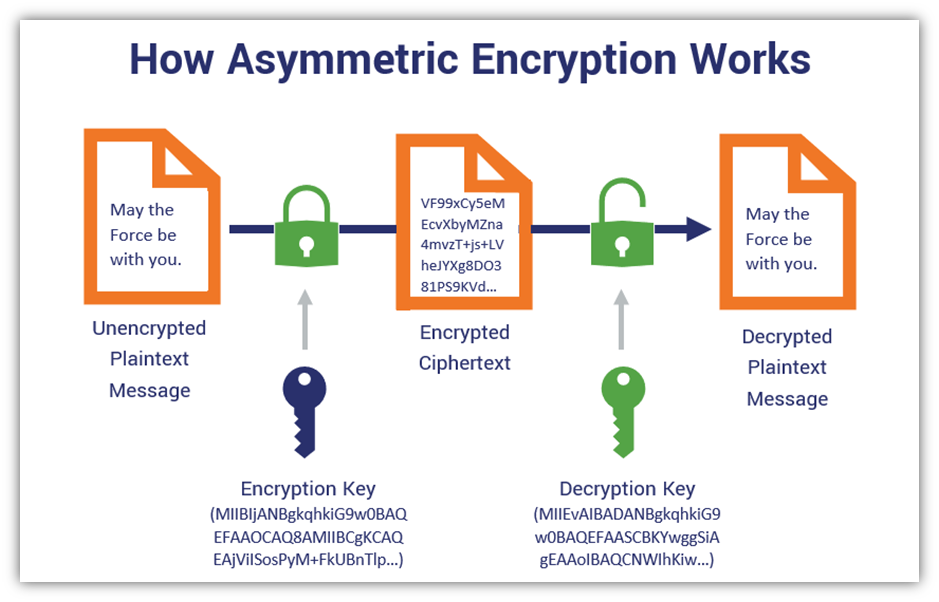
First and foremost, understanding the very foundation of the encryption method is critical. Each encryption scheme is built on unique algorithms and mathematical principles. For instance, symmetric encryption employs a single key for both encryption and decryption, whereas asymmetric encryption uses a pair of keys—a public key for encryption and a private key for decryption. This duality reveals its intricate dance, where one key’s integrity is paramount for the security of the entire system. Conducting a thorough review of the cryptographic algorithm employed is essential. Look into compliance with established standards such as AES (Advanced Encryption Standard) or RSA (Rivest-Shamir-Adleman). Adherence to these standards acts as a stamp of credibility, assuring the efficacy of your encryption.
Furthermore, investigating the key length is crucial. Consider the analogy of a safe: the longer and more complex the combination, the more resilient it is against brute-force attacks. For symmetric encryption, a key length of at least 128 bits is recommended; for asymmetric encryption, a key length of 2048 bits or more provides sufficient protection. However, one must also gaze into the horizon to anticipate future developments in computing power. The inexorable march toward quantum computing heralds a new era in cryptographic challenges. Consequently, a method deemed secure today may not withstand the advancements of tomorrow’s technology. This looming specter necessitates a proactive approach in choosing encryption methods capable of resisting potential future threats.
Once the foundational elements have been scrutinized, one must evaluate the implementation of the encryption scheme. Even the most robust encryption method can falter under poor execution. Analyze whether the keys are securely generated, stored, and distributed. Key exposure constitutes a principal vector for vulnerabilities, akin to a leak in a dam that could ultimately lead to catastrophic failure. Utilize strong key management practices to ensure that keys are only accessible to authorized entities and consider employing hardware security modules (HSM) for enhanced storage security.
To further bolster confidence in your encryption, perform rigorous testing. This step could be visualized as an athlete training for a marathon; preparation through systematic trials is vital. Employ penetration testing and vulnerability assessments to uncover any potential chinks in the armor. Engaging third parties to conduct these evaluations can yield unbiased insights, reminiscent of a fresh pair of eyes examining a tapestry for flaws that may have eluded the original weaver. Consider also implementing a method called “cryptographic agility,” which allows for easy upgrades to newer algorithms without overhauling the entire system. This flexibility is akin to keeping a spare tire readily accessible for unforeseen roadblocks during a journey.
Another pivotal aspect lies in scrutinizing the environmental factors influencing your encryption method. Surrounding infrastructure plays a significant role; after all, a fortress is only as strong as its moats and drawbridges. Assess the physical security measures surrounding data storage and transmission processes. Ensuring that all data in transit is encrypted using protocols like TLS (Transport Layer Security) can mitigate risks arising from eavesdropping or man-in-the-middle attacks—threats that can compromise even the most sophisticated encryption methodologies.
In addition, consider the human factor. The most advanced encryption does not matter if end-users lack the knowledge to implement it effectively. Educational endeavors informing users about secure practices, such as recognizing phishing attempts or safeguarding passwords, are essential. This awareness can often serve as the first line of defense, protecting the fortress from both external and internal threats. Human error is unpredictable; thus, bolstering user education can drastically reduce susceptibility to breaches.
Lastly, establish a regular review cycle for your encryption methods. The digital landscape is fluid, constantly evolving with newfound vulnerabilities and emerging threats. By institutionalizing the practice of periodic audits, organizations can maintain vigilance akin to a sentinel eternally watching over the castle gates. Assessing the encryption protocols periodically allows for timely upgrades, adaptations, and the reinforcement of security best practices.
In conclusion, the journey toward determining whether an encryption method is foolproof encompasses a detailed examination of numerous facets, each interwoven like threads in a tapestry of security. From understanding the underlying algorithms, evaluating implementation practices, and testing resilience, to managing user education and adapting to new threats, each aspect plays a crucial role. Ultimately, robust encryption is not merely a solitary endeavor; it is a comprehensive approach that demands attention to detail aligned with a commitment to ongoing vigilance. By acknowledging vulnerabilities and embracing adaptive strategies, one can aspire towards the fortified stronghold that ensures the confidentiality and integrity of sensitive data amidst the multifaceted challenges of the digital world.







Leave a Comment