In an age where data breaches are rampant and cyber threats loom large, how can one secure sensitive information, such as credit card numbers, while maintaining efficiency? This poses a playful challenge: Can we achieve a balance between robust encryption and seamless user experience? Let’s delve deeply into the intricacies of credit card encryption, examining various methodologies, evaluating their efficacy, and ultimately charting a pathway toward a solution that doesn’t compromise speed.
Encryption is the bedrock of data security. At its core, it transforms readable data into a format that is virtually unintelligible to unauthorized users. When it comes to credit card numbers, the stakes are palpably high. Mischievous actors are perpetually on the prowl for unguarded data. Therefore, implementing stringent encryption techniques is paramount.
However, one must navigate the dichotomy between robust security and operational efficiency. Traditional encryption methodologies often impose latency, thus hampering the user experience during transactions. This brings forth a critical inquiry: How can we fortify our defenses without introducing a bottleneck? To answer this, we must explore innovative encryption techniques that can withstand scrutiny without sacrificing performance.
One such technique is symmetric encryption. Utilized predominantly for its expediency, symmetric encryption relies on a single key for both encryption and decryption processes. Algorithms like the Advanced Encryption Standard (AES) exemplify this approach. AES, particularly in its 128-bit form, offers a commendable balance of security and speed, making it an appealing choice for encrypting credit card information. However, the challenge lies in securely managing the encryption keys. A compromised key leads to compromised data. Thus, even this relatively swifter method is plagued by its own pitfalls.
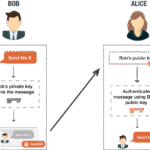
Next, consider asymmetric encryption, which employs a pair of keys: a public key for encryption and a private key for decryption. While this method inherently offers enhanced security due to its two-key system, it suffers from inefficiencies. The computational load required to process asymmetric encryption often results in slower transaction speeds. Consequently, it is generally impractical for situations necessitating rapid transactions, like online purchases.
Yet, a hybrid approach emerges as a promising avenue. This method combines both symmetric and asymmetric encryption techniques to deliver quick yet secure transactions. Initially, the credit card number can be encrypted using asymmetric encryption to safeguard the key exchange process, thereby minimizing vulnerability during transmission. Following this, symmetric encryption can be employed for the encryption of the actual credit card data, leveraging its speed for subsequent transactions.
In addition to method selection, further optimization can be achieved through the deployment of field-level encryption. Instead of encrypting whole datasets, field-level encryption enables the protection of specific fields, such as credit card numbers, while leaving others unrestricted. This strategic choice significantly mitigates performance impacts. When implemented deftly, the system encrypts only what is necessary, facilitating a more agile data processing framework that enhances user experience without compromising security.
Moreover, embracing tokenization offers a robust solution in the quest for speed. Tokenization substitutes sensitive credit card data with unique identifiers or tokens, rendering the actual data meaningless in the event of a breach. This practice dramatically reduces the risk associated with holding sensitive information, while maintaining the ability to process transactions efficiently. With tokenization, the need for continuous encryption during transactions is diminished, permitting swifter processing times.
Compression algorithms can also play a supportive role in improving transaction speeds. By compressing data prior to its encryption, organizations can lighten the data load, expediting the time it takes to transmit and process transactions. Although compression must be executed cautiously to avoid introducing vulnerabilities, properly applied techniques can yield noteworthy enhancements to performance.
In conclusion, the dual challenge of encrypting credit card numbers while preserving speed is indeed formidable, yet not insurmountable. Employing a multifaceted strategy that leverages symmetric encryption for its rapid capabilities, asymmetric encryption for initial secure exchanges, alongside tokenization and field-level encryption significantly bolsters the security framework without unnecessarily encumbering transaction speeds. The addition of compression techniques further enhances performance, propelling organizations toward a user-friendly experience while safeguarding sensitive information.
Ultimately, the imperative for a meticulous approach to credit card encryption cannot be overstated. By harmonizing security with expediency, organizations can navigate the treacherous waters of cybersecurity with confidence and efficacy. Are we prepared to embrace these methodologies, or will we allow complacency to usher in an era of vulnerability? The choice remains in our hands.








Leave a Comment