The digital age has ushered in profound transformations across various domains, with encryption emerging as a stalwart defender of our confidential information. Symmetric-key encryption, in particular, functions as a double-edged sword—offering security while presenting unique challenges in its development and implementation. Have you ever pondered what it takes to design a new symmetric key encryption algorithm like a pro? The answer isn’t straightforward, but it poses fascinating challenges and educational opportunities. In this exploration, we will delve into the intricate process of designing a symmetric-key algorithm that can withstand scrutiny and offer reliable protection against nefarious entities.
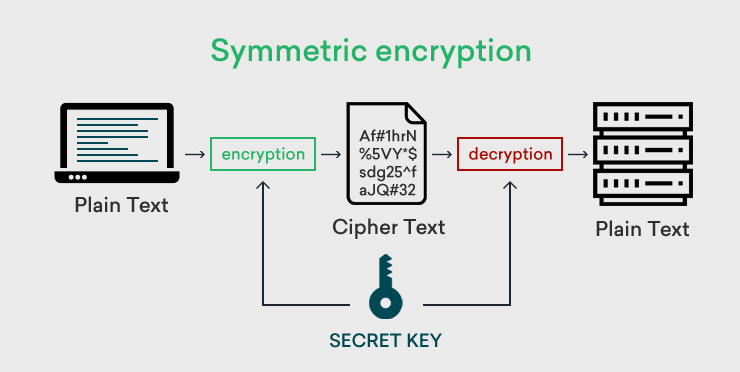
To embark on this journey, it is vital first to understand the foundational principles of symmetric-key encryption. This type of encryption involves a singular key, which is used for both the encryption and decryption processes. The efficiency of symmetric encryption is paramount, as it often outperforms its asymmetric counterparts due to lower computational requirements. However, this advantage also necessitates a robust design to mitigate the risks associated with key distribution and management. Without further ado, let’s dissect the stages involved in crafting a new symmetric-key encryption algorithm.
**1. Define Objectives and Scope**
In the nascent stages of algorithm development, one must clearly delineate the objectives. What are the specific security requirements the algorithm needs to satisfy? Is it intended for general use or specific applications such as securing communications, safeguarding data at rest, or ensuring integrity in transactions? Understanding the scope will help in determining the algorithm’s architecture and its resistance to potential vulnerabilities.
**2. Research Existing Algorithms**
Upon establishing objectives, thorough research into existing symmetric-key encryption algorithms is crucial. Familiarize yourself with benchmark protocols such as AES (Advanced Encryption Standard), DES (Data Encryption Standard), and more contemporary innovations like ChaCha20. Examine their structural designs, strengths, and weaknesses to glean insights and inspiration. This iterative learning will better inform your design framework, creating a balance of originality while adopting proven strategies.
**3. Key Length and Structure**
Next, one must deliberate over the key length. The efficacy of symmetric encryption is heavily predicated on the length of the key — a longer key typically offers increased security but can introduce complexities in processing. Contrary to outdated practices such as DES, which employed a mere 56-bit key, modern standards advocate for at least 128 bits, favoring 256 bits for enhanced security against current computational capabilities. The design should also accommodate key generation mechanisms that ensure randomness and unpredictability.
**4. Develop the Permutation and Substitution Functions**
One hallmark of effective symmetric algorithms is the integration of complex substitution and permutation functions. These functions transform the input data into ciphertext while obfuscating the original information. A robust design integrates multiple rounds of these operations to stave off brute force and cryptanalysis. Researchers often utilize confusion and diffusion principles — ensuring that a change in a single input bit produces an unpredictable change in the output. Incorporating well-distributed S-Boxes (substitution boxes) will enhance the algorithm’s strength, drawing from combinatorial principles of non-linearity.
**5. Establish Feistel or SPN Structure**
The design phase must also include a clear structure — either a Feistel network or a substitution-permutation network (SPN). Feistel networks simplify the design and make it easier to construct encryption/decryption routines since the same operations can be applied in reverse. On the other hand, SPNs often lead to greater diffusion, making them inherently resistant to differential cryptanalysis. This decision hinges on previously established objectives and performance requirements.
**6. Implement a Secure Key Scheduler**
Once the design framework is in place, implementing a key schedule is imperative. The key scheduler must generate round keys from the initial key in a manner that resists attacks. Often, why breakdowns occur in encryption attempts stem from weaknesses in key scheduling. Thus, ensuring that round keys exhibit high entropy and promote randomness is essential for fortifying the algorithm’s defenses.
**7. Conduct Rigorous Testing and Validation**
No encryption algorithm can be deemed secure without exhaustive testing. This phase entails both functional testing to check for operational efficiency and security testing to assess resistance against known attacks, such as differential and linear cryptanalysis. Furthermore, tools such as NIST’s Cryptographic Algorithm Validation Program can be employed, presenting a broad spectrum of methodologies to validate the algorithm’s performance in real-world scenarios.
**8. Document and Review**
Good practice dictates documenting every decision made during the design process. This documentation serves as both a reference and a means for others to review and potentially critique the algorithm. Peer reviews through open cryptographic forums or scholarly articles ensure the approach stands up against the collective expertise of the community. This accountability mechanism is integral for fostering trust in the algorithm’s reliability.
**Conclusion**
Designing a new symmetric key encryption algorithm is a multifaceted endeavor that requires a delicate blend of creativity, analytical thinking, and deep technical knowledge. It’s a task that, when undertaken with diligence, can lead to significant advancements in the field of encryption. Armed with to tools, methodologies, and an unwavering commitment to security, aspiring cryptographers have the potential to create solutions that not only protect our data but also bolster the wider digital ecosystem. As you embark on your own algorithm design journey, may your work challenge existing paradigms and contribute to an era of resilient encryption.







Leave a Comment