Creating your own encryption algorithm can be both a daunting and exhilarating venture. In an age where data breaches are rampant and personal privacy is increasingly compromised, the ability to encode your communications and safeguard your information is invaluable. The journey of building an encryption algorithm from scratch not only equips you with essential cryptographic knowledge but also enhances your understanding of data security, instilling a sense of empowerment over your digital footprint.
Before diving into the nitty-gritty, it is prudent to examine the foundational principles that underscore the practice of cryptography. Encryption serves to transform readable data, or plaintext, into an obscured format known as ciphertext, rendering it unintelligible to unauthorized users. Within this blog, we will elucidate the steps required to formulate a basic encryption algorithm, encompassing the theoretical underpinning, essential considerations, and practical applications.
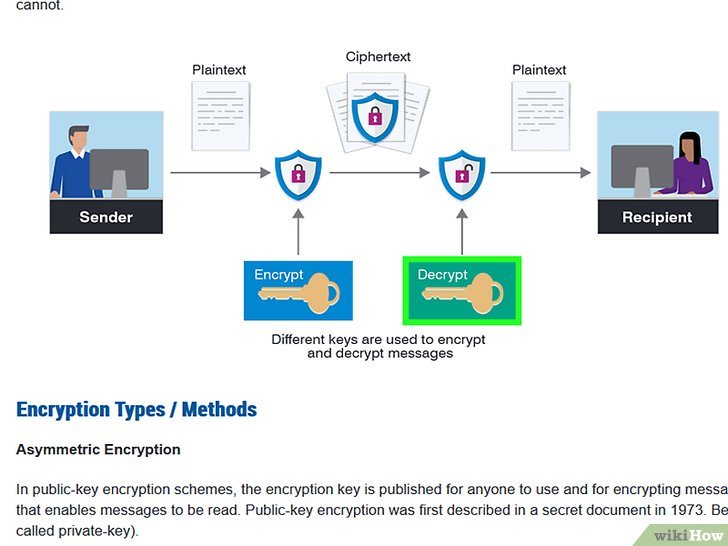
First, one must comprehend the two fundamental types of cryptographic systems: symmetric and asymmetric encryption. Symmetric encryption employs a single key for both encoding and decoding data, necessitating that both sender and receiver securely exchange the key beforehand. In contrast, asymmetric encryption utilizes a pair of keys; a public key for encryption and a private key for decryption. This bifurcation is crucial in determining the design of your algorithm.
Let us begin the journey of crafting your encryption algorithm with a critical focus on key design. The efficacy of any encryption system hinges on the strength of its key. A robust key must possess sufficient entropy to thwart brute-force attacks, which systematically attempt every possible combination until the correct one is discovered. To achieve this, consider utilizing keys of considerable length, ideally 128 bits or more. Furthermore, employ a secure random number generator to produce your keys, eschewing predictable patterns that could jeopardize security.
Next, define the operational mechanics of your encryption algorithm. At this juncture, you’ll establish the function that will transform plaintext into ciphertext. This could be achieved through a variety of methods, including substitution ciphers, transposition ciphers, or more advanced techniques such as block ciphers and stream ciphers. Substitution ciphers replace individual letters with others, while transposition ciphers rearrange the positions of the characters while maintaining their identities. Both methods lay the groundwork for more complex procedures.
Consider implementing a substitution cipher as a fundamental exercise. This can be illustrated through the Caesar cipher, a rudimentary yet instructive example. By shifting each character in the plaintext a certain number of places down the alphabet, you can easily encode your message. For instance, with a shift of three, ‘A’ transforms to ‘D’, ‘B’ to ‘E’, and so forth. While the Caesar cipher is a mere stepping stone to cryptographic sophistication, it illustrates essential principles of substitution.
As you refine your encryption technique, delve into the realm of permutation and combine both substitution and transposition for a more secure cipher. One might interleave your prior substitution output with a transposed sequence, effectively obscuring the original message even further. Such an implementation not only complicates decryption efforts but introduces complexity, which is a stalwart defender against cryptanalysis.
Now that you have established a method for encrypting data, it is essential to devise the decryption process. To successfully decode the ciphertext back into plaintext, maintain the inverse operations of your encryption mechanism. If you substituted ‘A’ with ‘D’ during encryption, ensure that during decryption, ‘D’ returns to ‘A’. This reversibility is paramount, as it embodies the principle of a functional encryption algorithm.
Furthermore, it is vital to consider the integrity of the data. To bolster your cipher against alteration, integrate checksums or hashes. A hash function converts data into a fixed-size string of characters, effectively producing a digital fingerprint for your message. By appending this hash to your ciphertext, you establish a method of verification during decryption to ascertain that the data remains untarnished.
Once you have a functional algorithm, testing becomes indispensable. Subject your encryption and decryption processes to various scenarios, utilizing test cases that cover diverse inputs and edge cases. Rigorous testing will expose vulnerabilities, enabling you to fortify your algorithm against potential exploits. Use cryptanalysis techniques to break your cipher and draw insights on its vulnerability.
In the final stages of crafting your encryption algorithm, documentation of your work is crucial. Carefully articulate the design choices, algorithm functions, and potential weaknesses for future reference. A meticulous ledger will not only facilitate future enhancements but also assist in educating peers and interested enthusiasts about your methodology.
In conclusion, building your own encryption algorithm is not merely an exercise in coding; it is an invitation to internalize the intricacies of data protection. Through a deliberate focus on key design, operational mechanics, and rigorous testing, you can construct a robust encryption framework. This venture could shift your perspective on digital interactions, empowering you to navigate the complexities of data privacy. Ultimately, the ability to craft a secure environment for your information becomes not just a skill but a crucial element of modern digital citizenship.
With the ever-evolving landscape of cybersecurity threats, equipping oneself with the tools and knowledge to protect one’s own data is of paramount importance. As you embark on this journey of discovery and mastery, remember that the world of cryptography is expansive. Continuous learning and adaptation will ensure that your algorithm remains resilient against the continuous onslaught of adversarial tactics in the digital realm. The exploration of encryption yields not only knowledge but a profound appreciation for the relentless pursuit of secure communication and data integrity.







Leave a Comment