In the ever-evolving landscape of cryptographic standards, a question emerges: How secure is it to use HMAC with SHA-1 in 2025? As organizations and individuals increasingly depend on digital security mechanisms to protect sensitive information, understanding the implications of leveraging dated cryptographic technologies like SHA-1 becomes paramount.
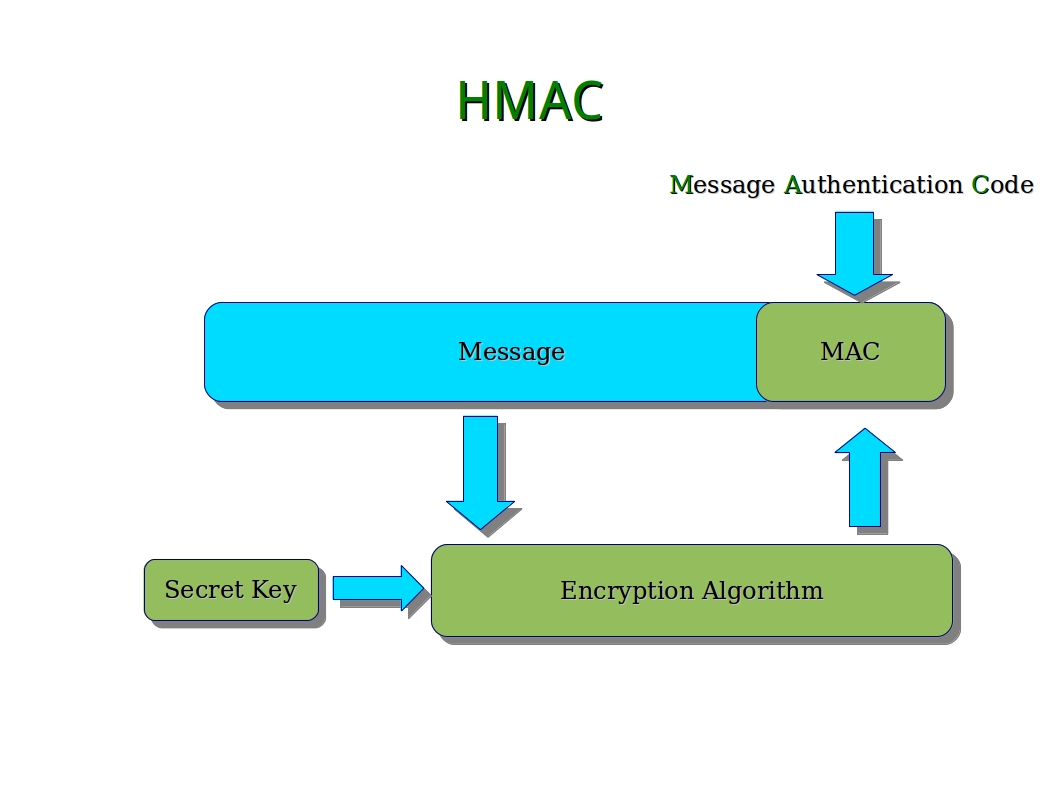
The HMAC (Hashed Message Authentication Code) is a widely adopted construction designed to provide message integrity and authenticity through the combination of a cryptographic hash function with a secret key. When paired with SHA-1, HMAC can theoretically offer a layer of security; however, it is critical to assess the underlying hash function’s robustness as we progress into 2025.
Historically, SHA-1 (Secure Hash Algorithm 1) was developed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST) in 1995. Initially heralded for its strength and practicality, SHA-1 quickly found its way into numerous applications, including SSL certificates and digital signatures. Yet, as computational power surged and cryptanalysis techniques advanced, so too did concerns surrounding its security. Significant vulnerabilities were exposed, culminating in practical collisions demonstrated by researchers in 2017. These developments sparked a widespread abandonment of the algorithm in favor of more robust alternatives, such as SHA-256 and SHA-3.
Fast forward to 2025. As machines become more efficient, the computational heft required to run sophisticated attacks diminishes, but the fundamental weaknesses inherent in SHA-1 remain. Consequently, the question looms larger: Does integrating this frail hash with a well-designed HMAC provide sufficient security, or are we gambling with our digital safety? The very fabric of security frameworks can unravel with the flick of a virtual wrist if this choice is made with inadequate discernment.
Let us delve into the mechanics of HMAC themselves. An HMAC is resilient in that it combines the strength of a cryptographic hash function with a secret key, allowing it to withstand certain traits of collision resistance. This construction improves the integrity and authenticity aspects of data. However, the effectiveness of HMAC is intrinsically tied to the cryptographic strength of the hash function used. If SHA-1 falters, then so does HMAC’s reliability.
Using HMAC with SHA-1 may initially appear to be an accessible solution, especially for legacy systems. Organizations may feel a sense of security, believing they have implemented a standard encryption protocol. But this false confidence raises an important consideration: How long can one truly rely on SHA-1 before exposure to potential risks? It is no longer speculative; real-world threats are live and unfolding. Attack vectors emerge, increasingly sophisticated and capable of undermining even the most diligent security measures.
Moreover, replaceability plays a critical role in the analysis of cryptographic security. Transitioning to more contemporary alternatives like HMAC-SHA-256 requires time and resources, yet the cost of resistance against evolution may outweigh the financial implications of bolstering cybersecurity. The primary question here is not merely about feasibility, but rather, how urgently is the need to adapt and ensure stronger safeguards against potential breaches?
When assessing the lifespan of cryptographic solutions, one must also consider regulation and compliance frameworks. In 2025, many countries may enforce stricter security protocols, making it non-inclusive for organizations to continue employing SHA-1. Certification bodies, regulatory architectures, and best practices within the domain of data protection may render SHA-1 obsolete. Adhering to these frameworks becomes imperative not just for compliance but to maintain customer confidence in the digital ecosystem.
Additionally, it would be remiss not to factor in the dimension of threat modeling. Security protocols must be evaluated not only in terms of their design but also in alignment with the realities of the threat landscape. Compromise scenarios involving HMAC-SHA-1 may reveal vulnerabilities that can be exploited by attackers equipped with sufficient resources. As threat actors inventively recalibrate their techniques, reliance on an outdated hash function is akin to leaving the front door wide open during a storm.
In conclusion, while the prospect of using HMAC with SHA-1 in 2025 may still carry a semblance of reassurance, a thorough examination of its effectiveness unveils a tapestry woven with risk. As society increasingly leans into a digital future, the imperative to upgrade security systems becomes critical. By embracing modern and robust algorithms, organizations do not merely enhance their defensive architecture; they cultivate a culture of safety, vigilance, and accountability within their operational frameworks. Thus, the playful question posed earlier transforms into a pressing reality: Are we willing to place our trust in a crumbling edifice, or are we ready to fortify our defenses against the vicissitudes of technological evolution?







Leave a Comment