In the realm of digital communications, the security of information exchange often contends with an intricate dance between need and vulnerability. For every piece of sensitive data transmitted across networks, there exists a potential threat, a lurking adversary poised to intercept and exploit. Public key exchange arises as a crucial mechanism in this theater of security, operating much like a courtly dance where each participant plays a pivotal role, maintaining decorum while ensuring the confidentiality of their movements.
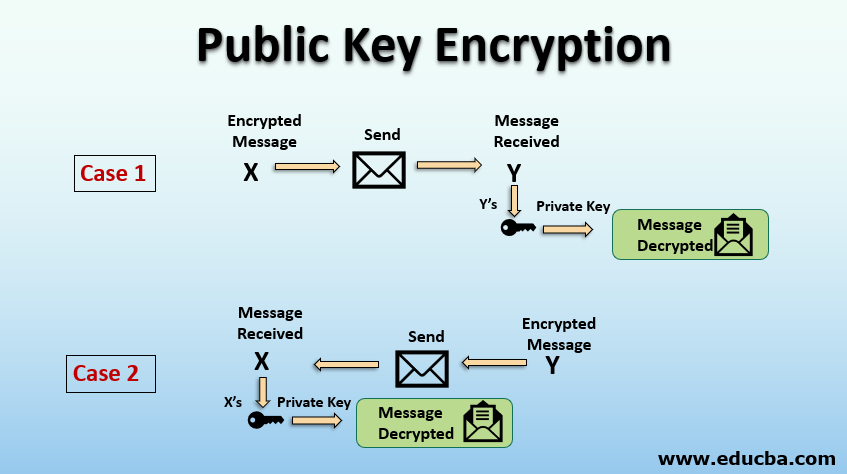
The essence of public key exchange lies in its asymmetric nature. Imagine two correspondents, Alice and Bob, each equipped with a unique set of keys. Alice wields a public key, akin to an ornate lock displayed prominently for all to see, while her private key, a closely guarded secret, remains hidden from prying eyes. Bob, similarly, possesses his own keys. When Alice wishes to send a secret message to Bob, she deftly encloses her missive within the confines of Bob’s public lock, casting it into the digital ether. The allure of this arrangement is compelling; anyone can use Bob’s public key to secure messages for him, yet only Bob can unlock them with his private key.
This interaction mirrors a modern-day diplomacy, where trust is established through the assurance that neither party can unveil the other’s secrets without proper authorization. Yet, how can we be certain that the keys exchanged aren’t part of a nefarious scheme? The answer lies in robust cryptographic protocols that underpin this seemingly effortless exchange.
Central to this security is the concept of key generation, executed through complex mathematical algorithms designed to generate keys that pair off in a way that—although easy to create—remains infeasible for adversaries to calculate the private key from its public counterpart. The computational difficulty associated with prime factorization, for instance, is foundational to the RSA algorithm, one of the most widely utilized public key encryption systems. Encrypting data using this method transforms simple messages into convoluted strings of characters intelligible only by the rightful receiver.
Intriguingly, the notion of ephemeral keys introduces a layer of dynamism to the exchange process. Much like a fleeting mirage, these temporary keys emerge only momentarily during communication, minimizing the risk of being compromised during prolonged exchanges. Once the conversation concludes, the ephemeral keys dissipate, leaving no trace for potential eavesdroppers. This strategy ensures that even if an attacker were to gain access to the keys, they would find little use in the absence of the ephemeral context that once empowered the secure transmission.
Furthermore, the implementation of digital signatures serves as an essential ingredient in this ballet of trust. By signing a message with her private key, Alice leaves behind a unique fingerprint, an assurance that the message indeed originates from her. This signature can then be verified using her public key, facilitating a confirmation of authenticity. Should an attacker endeavor to alter the message, the digital signature would not align, effectively rendering the tampered communication detectable.
The paradigm of public key infrastructure (PKI) fortifies this delicate interplay, serving as a digital stamp of legitimacy for the keys exchanged. Certificates issued by trusted authorities act as vouches for the authenticity of the public keys. When Bob receives Alice’s public key, he can verify its provenance through these certificates, ensuring that he isn’t entrusting his secrets to an impostor. Thus, PKI becomes the trusted arbiter in the exchange, echoing the role of a notary public in the physical world.
Security, however, is an ever-evolving landscape where threats are constantly adapting. The advent of quantum computing heralds new challenges that the current cryptographic systems may struggle to withstand. The potential for quantum algorithms to factorize large numbers efficiently could undermine the foundational principles of traditional public key systems. As the digital realm anticipates the rise of quantum attacks, cryptographers tirelessly innovate, exploring post-quantum cryptography as a versatile bulwark against impending threats.
In the grander scheme of cybersecurity, the role of public key exchange transcends mere technical utility. Rather, it becomes a metaphorical tapestry interwoven with trust, resilience, and adaptability. Just as a fortress withstands sieges, the intricacies of public key exchange endure threats by fortifying its foundations with layers of cryptographic innovations and protocols. With every key exchanged, a silent accord is established—one that fortifies the bonds of trust essential for the proliferation of secure digital communication.
Thus, as Alice and Bob continue their exchanges, unperturbed by the shadow of potential interception, the beauty of public key exchange unfolds—an intricate ballet of mathematics, trust, and technology that safeguards the essence of modern communication. The ever-watchful vigilance against adversaries, combined with the commitment to enhancement in cryptographic methods, ensures that this artful dance of security continues, preserving the sanctity of their shared secrets in an ever-volatile digital landscape.








Leave a Comment