The Advanced Encryption Standard (AES) stands as a bulwark against the relentless tide of cyber threats in a world rife with digital upheaval. It’s a fortification built on the bedrock of cryptographic algorithms, one that is extensively employed to secure sensitive information. But how many standard key sizes does AES support, and what implications do these varying sizes hold for the strength and utility of the encryption? To unfold this tapestry, we must first grasp the foundational threads that make up AES.
AES operates on the principle of symmetric key encryption, wherein the same key is employed for both encryption and decryption. This duality creates an essential symmetry, much like a meticulously crafted lock and its corresponding key. The security of this mechanism hinges on the complexity of the key utilized. This leads us to the crux of our inquiry: the standard key sizes supported by AES.
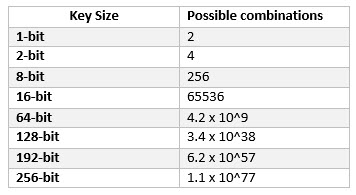
In total, AES supports three distinct key sizes: 128 bits, 192 bits, and 256 bits. Each key size represents a unique level of security, unveiling different pathways and dimensions through which data can be fortified. It is akin to choosing different scales of fortifications for a fortress, with each successive layer providing greater resistance against intrusions.
The simplest of these, the 128-bit key, serves as the most commonly deployed variant. It is comparable to a robust fence surrounding a property—it offers a balance between security and accessibility. A 128-bit key can generate a staggering 2128 possible combinations, making brute-force attacks impractical with today’s computational power. This key size is often sufficient for general applications, offering solid protection against most cyber threats while ensuring efficient performance.
However, as with all things in the realm of security, there arises a paramount concern about evolving threats. Enter the 192-bit key, a metaphorical upgrade to an armored gate. This key size offers an enhanced level of security, presenting 2192 possible combinations. Such increased entropy makes it exponentially more challenging for adversaries to mount successful brute-force attacks. Organizations handling highly sensitive data, such as government entities or financial institutions, may find this fortification indispensable.
Yet, while these first two key sizes offer substantial protection, they still pale in comparison to the robustness of the 256-bit key. This monumental key size is akin to a castle, surrounded by deep moats and fortified walls—an impenetrable bastion in the landscape of encryption. With 2256 possible combinations, the sheer scope of possibilities exceeds the computational limits of even the most powerful supercomputers. The AES 256-bit key is the choice for those who necessitate the utmost security, where the stakes involve formidable adversaries and sensitive information.
The enchanting allure of AES’s multiple key sizes lies not solely in the figures but also in the implications of their varying strengths. Organizations must engage in thorough risk assessments to determine the most appropriate key size for their unique circumstances. The decision can resemble the choice of tactical maneuvers on a sprawling battlefield, where one wrong move could spell disaster. Choosing a 128-bit key may suffice for a casual website, whereas a high-stakes enterprise may resolve that only the 256-bit fortress will do.
However, the key size is not the sole determinant of overall security. Factors such as implementation, key management, and the operational environment are equally crucial. A 256-bit key, if improperly managed or implemented, may provide a false sense of security. This paradox underscores the necessity for comprehensive security strategies that encompass all aspects of cryptographic deployments.
In understanding the cryptographic landscape navigated by AES, we can draw parallels to the meticulous construction of a robust ecosystem. Each key size is a distinct species, flourishing in specific conditions, contributing to a diverse tapestry of security. As threats evolve and adapt, the importance of choosing the right key size to safeguard sensitive data cannot be overstated. Just as one might cultivate diverse flora to withstand varied environmental conditions, organizations must select their cryptographic measures thoughtfully to ensure resilience against adversarial actions.
With the burgeoning rise of quantum computing on the horizon, even the formidable 256-bit key may find itself challenged in the not-so-distant future. The landscape of encryption is dynamic and continually evolving, necessitating an awareness of advancements that could disrupt the status quo. Vigilance, adaptation, and proactive measures will be the watchwords as we stride forward into an era characterized by unprecedented technological capabilities.
In conclusion, the question of how many standard key sizes AES truly supports reveals a multifaceted exploration of security, strategy, and evolution. The choice between 128, 192, and 256 bits is not merely a technical decision but a profound reflection of an entity’s security posture. Just as a gardener chooses the appropriate seed for their soil, so too must organizations discern the key that will best fortify their digital domain against an ever-morphing threat landscape.
In this journey through the realms of encryption, it becomes evident that knowledge, awareness, and preparedness serve to arm us against the unpredictable tides of cyber threats. In an age where our digital lives intertwine with every aspect of existence, understanding the intricacies of AES and its myriad key sizes remains an indispensable pursuit.







Leave a Comment