Digital signatures have emerged as a cornerstone of modern communication, particularly in the realms of legal documentation and online transactions. They serve not only as a means of authenticating documents but also as a pivotal component in establishing trust within digital environments. This article endeavors to elucidate the mechanisms behind digital signatures and the reasons courts lend them credibility.
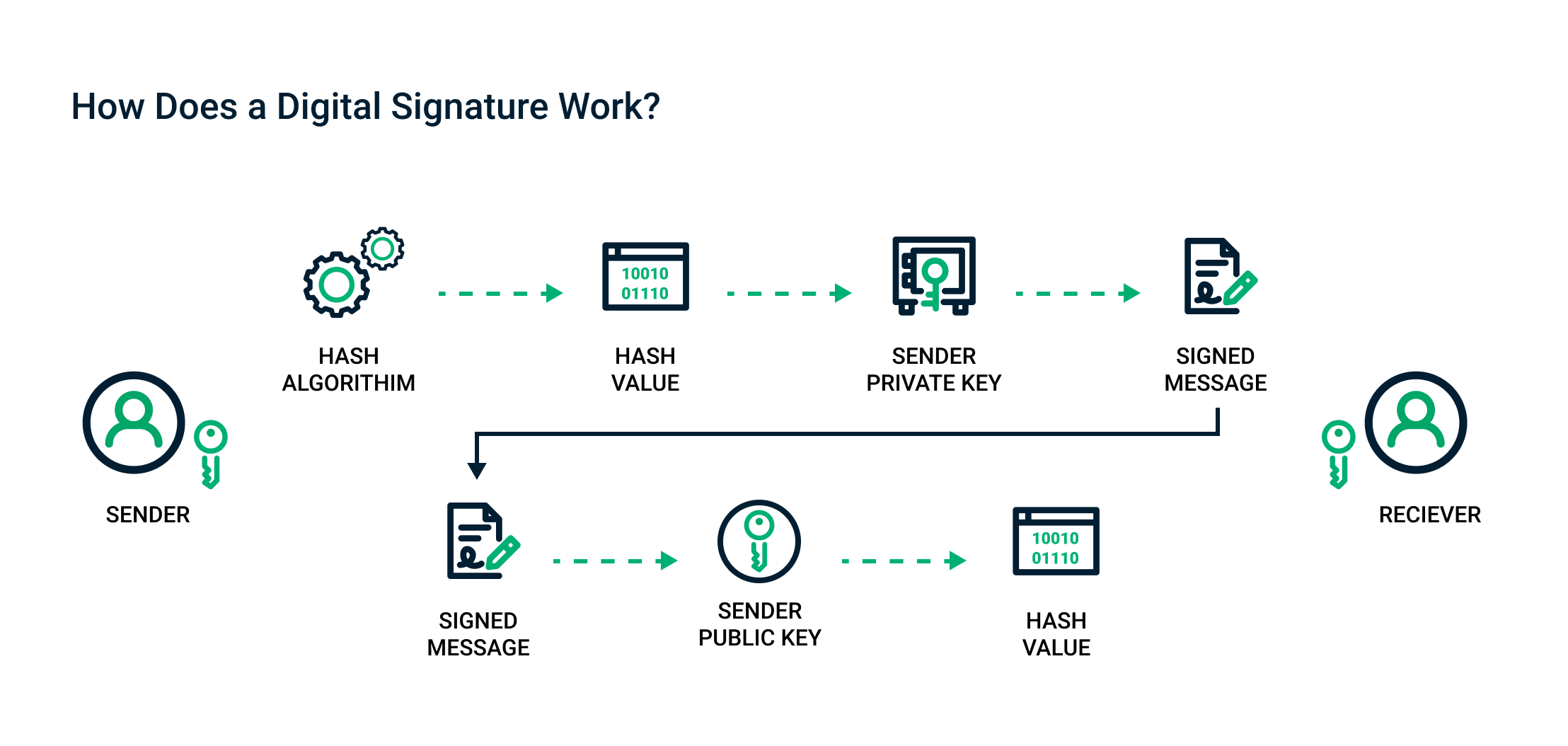
At their core, digital signatures rely on asymmetric cryptography, a method that employs a pair of keys: a public key and a private key. The private key, which remains confidential to the signer, is utilized to create the signature, while the public key can be shared openly. This unique pairing is the foundation upon which the integrity of digital signatures is built. To grasp the functionality of digital signatures, one must first understand the concept of hashing.
When a document is signed digitally, its contents are first run through a cryptographic hash function. This produces a fixed-size string of characters unique to the document, known as a hash value. Any alteration to the original document, even the slightest change, will result in a substantially different hash. This characteristic ensures that the integrity of the document can be verified by anyone who has access to both the original document and the signature.
Once the hash is generated, the signer uses their private key to encrypt this hash value. The resulting encrypted hash becomes the digital signature. When the document is sent to the recipient, it arrives alongside the digital signature. Using the sender’s public key, the recipient can decrypt the signature, resulting in the original hash value. By then independently hashing the received document and comparing it to the decrypted hash, the recipient can confirm the authenticity and integrity of the document. If the two hash values match, the signature is valid.
This dual-lock mechanism—comprising the private key held by the signer and the public key that anyone can use—affords an unprecedented level of security. While the private key safeguards the signature, the public key facilitates transparency and accessibility. Thus, both parties involved can verify the authenticity of the document without the fears associated with traditional signatures, which can be easily forged or manipulated.
Beyond the mechanics of digital signatures lies the overarching framework of trust that courts and institutions have established. Digital signature technologies must adhere to stringent cryptographic standards to be deemed reliable. In many jurisdictions, digital signatures are regulated by formal frameworks such as the Electronic Signatures in Global and National Commerce (ESIGN) Act or the Uniform Electronic Transactions Act (UETA) in the United States. These legal statutes define the parameters within which digital signatures can operate and establish guidelines for their validation.
Moreover, courts have developed a profound trust in digital signatures, owing to several factors. First, the auditable trail that accompanies digital transactions serves as a powerful deterrent against fraud. When digital signatures are implemented correctly, they create an immutable ledger that chronicles the signing process. Each action is timestamped, recorded, and verifiable, significantly bolstering the reliability of evidence presented in court. This auditability is a critical advantage when assessing disputes regarding contract formation or the authenticity of documents.
Second, the shift toward digital documentation and transactions is mirrored by advancements in technology that enhance security protocols. The incorporation of biometric authentication, two-factor authentication, and blockchain technologies adds additional layers to digital signature systems. This evolution further alleviates concerns regarding data breaches and unauthorized access, fortifying the court’s reliance on digital signatures as a valid means of verification.
The robustness of public key infrastructure (PKI) also plays a pivotal role in ensuring the validity of digital signatures. PKI involves the issuance of digital certificates by Certificate Authorities (CAs), which serve to validate the ownership of public keys. This adds a level of scrutiny to the process, ensuring that signers are who they claim to be, and further solidifies the legitimacy of digitally signed documents. CAs undergo rigorous auditing processes to maintain their status, thus enhancing the framework of trust within which digital signatures operate.
Indeed, the traction gained by digital signatures in legal proceedings signals a significant evolution in how society perceives trust in documents. The transition from ink and paper to bits and bytes has not only facilitated greater convenience but has also sparked discussions about the future of legal agreements. As courts embrace digital signatures, legal professionals are compelled to adapt to this changing landscape, harnessing technology to enhance their practices and safeguard their clients’ interests.
Despite their many advantages, it’s essential to acknowledge the potential risks associated with digital signatures. As with any technology, vulnerabilities exist, particularly regarding the protection of private keys. Consequently, organizations must implement comprehensive security measures to mitigate these risks, ensuring that the processes surrounding digital signatures remain secure and reliable.
In conclusion, the intricate interplay between cryptography, technology, and legal frameworks has birthed digital signatures—an innovation that embodies both trust and security. By understanding how digital signatures work and the rationale behind their acceptance in courts, one can appreciate the profound shift in our approach to authentication and documentation. As this technology continues to evolve, it promises not only greater efficiency in transactions but also enriches the legal landscape, redefining paradigms of trust in a digital age.







Leave a Comment