In an increasingly digital world, safeguarding information is paramount. One of the cornerstone principles in data security is ensuring data integrity, which refers to the accuracy and consistency of data throughout its lifecycle. Hashing, a cryptographic technique, plays a fundamental role in achieving this objective. This guide will delve into the mechanics of hashing, its various applications, and the types of hashing algorithms commonly utilized.
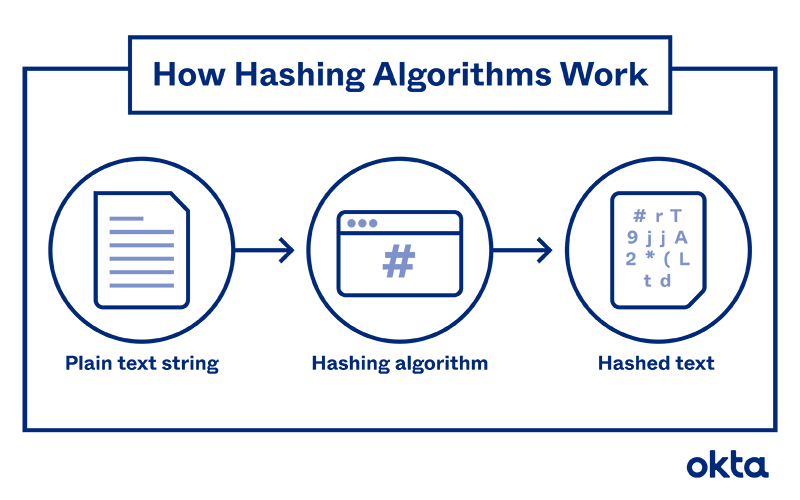
At its core, hashing is a process that transforms input data of arbitrary length into a fixed-length output, known as a hash value or hash code. This transformation employs a mathematical function, known as a hash function. The resultant hash offers a unique fingerprint for the original data, enabling users to verify its integrity. The transformative nature of hashing is one critical aspect that contributes to its efficacy in ensuring data integrity.
One of the most salient attributes of a cryptographic hash function is its determinism. For any given input, the output will invariably be the same, thereby allowing for consistent validation. If someone were to alter even a single character in the original data, the hash value would change dramatically. This sensitivity is vital, as it guarantees that any unintended modifications—whether they are accidental or malicious—are immediately detectable.
In the realm of hashing, we encounter several distinct types of algorithms, each serving specific purposes. These algorithms can be broadly categorized into three main types: cryptographic hashing algorithms, non-cryptographic hashing algorithms, and those that are specifically designed for file integrity verification.
Firstly, cryptographic hashing algorithms, such as SHA-256 (Secure Hash Algorithm 256-bit) and MD5 (Message Digest 5), are designed with security as a primary focus. Their primary application includes securing password storage, generating digital signatures, and ensuring the authenticity of transmitted data. Cryptographic hashes are engineered to be computationally infeasible to reverse, meaning that generating the original input from a hash value should be virtually impossible. This is critical for scenarios requiring stringent security measures, such as financial transactions, where the risk of fraud can have dire consequences.
On the other hand, non-cryptographic hashing algorithms, like MurmurHash and CityHash, prioritize speed over security. These algorithms are widely used in applications like data retrieval, database indexing, and checksums. While they are suitable for certain use cases, their inherent vulnerabilities render them unsuitable for security-sensitive applications, as they may not provide adequate resistance against intentional corruption.
File integrity verification hashes are designed to ensure that files remain unaltered throughout their transmission or storage. Algorithms, such as SHA-1 and CRC32 (Cyclic Redundancy Check), are extensively utilized for this purpose. When a file is transmitted, a hash of the original file can be computed and sent alongside it. The recipient can generate a hash of the received file and compare it with the original hash. If they match, it is reasonably assured that the file has not been tampered with; if not, the file may be corrupted or maliciously modified.
As with all technologies, hashing is not without its challenges. The emergence of advanced computational techniques has led to vulnerabilities in certain algorithms. For instance, MD5 and SHA-1 have been shown to have weaknesses that allow attackers to generate collisions, where two different inputs produce the same hash output. This phenomenon can lead to significant security ramifications, prompting the transition to more robust hashing algorithms like SHA-256 and SHA-3.
In addition to the inherent security concerns associated with specific algorithms, the choice of hashing application can impact overall data integrity. For password storage, implementing a strong hashing function is essential. Salt, a random value added to the password before hashing, provides an additional layer of security against pre-computed attacks, such as rainbow table attacks. By increasing the complexity of the input, this technique enhances the security of stored passwords significantly.
Another critical consideration in the hashing landscape is the potential for misuse. While hashing is a powerful tool for ensuring data integrity, its effectiveness is contingent upon proper implementation. A hashed value, if poorly managed or improperly utilized, can introduce vulnerabilities rather than alleviate them. For example, storing hashes without adequate security measures—such as restricting access or using salting and key stretching techniques—may leave systems exposed to brute-force attacks.
In conclusion, hashing is an indispensable technique for ensuring data integrity in digital communications and storage. By transcending the variability of input lengths and generating fixed output lengths, hashing creates a unique representation of data, making any alterations easily identifiable. Understanding the various hashing algorithms and their applications facilitates informed decision-making when implementing security measures. As threats to data security evolve, so too must the strategies employed to ensure the integrity of information. Heightened awareness and diligence in adopting robust hashing practices can significantly bolster defenses against data tampering and loss.








Leave a Comment